Virtual private networks (VPN) are the main alternative for users to browse the Internet with complete privacy, although like any other technological development, these can present flaws, mention experts from a pentest training course. According to a recent report, a flaw in the iOS 13.4 system prevents VPNs from encrypting all network traffic, which could expose users’ browsing data.
The flaw was reported by ProtonVPN research team, which decided to post their findings on their official site. The publication includes a brief explanation of the flaw and some tips for mitigating it, at least until Apple releases the corresponding updates.
As previously mentioned by pentest training course experts, when an Internet-connected device uses a VPN, its operating system closes all existing connections and then resets them through the VPN tunnel.
One of ProtonVPN researchers found that iOS 13.3.1 does not properly close existing connections on Apple devices; while most of these connections are short some data prevails and might remain open for a few minutes, and even hours, outside the VPN tunnel. An example of this is Apple’s push notification service, which maintains a long-lasting connection between the device and the company’s servers, although the flaw could affect any service running on iOS.
This flaw could expose user data if the affected connections are not encrypted, as mentioned by pentest training course experts. One of the most likely scenarios due to this failure is IP leakage; a threat actor could access a user’s IP and the servers it connects to because of this error.
Experts used the Wireshark tool to capture network traffic from an iOS device with this flaw. As shown in the following screenshot, traffic between the iOS device IP and an external IP address that does not correspond to a VPN server was detected.
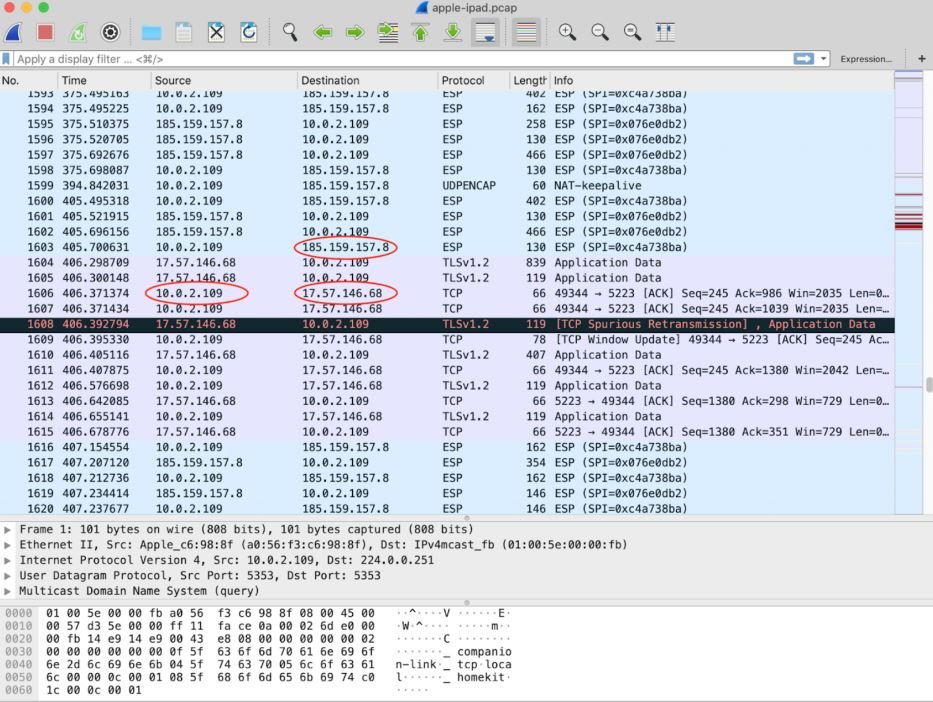
For obvious reasons, this flaw poses a security risk to VPN users, so the International Institute of Cyber Security (IICS) recommends implementing the following steps to prevent leaks:
- Connect to your VPN service provider
- Activate airplane mode, which will eliminate all Internet connections and temporarily disconnect the VPN
- Turn off airplane mode. The device will automatically reconnect to the VPN, so there will be no normal persistent connections
This process must be implemented until the company releases the required updates.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











