Specialists from a cyber security consulting company report the finding of a critical vulnerability in Tomcat and JBoss that could allow unauthenticated remote threat actors to access the content of any file on a vulnerable web server (or servlet container) to obtain sensitive configurations or to execute arbitrary code if the server allows uploading files.
The flaw, tracked as CVE-2020-1938, was discovered by China-based cybersecurity firm Chaitin Tech. This vulnerability resides in Apache Jserv Protocol (AJP) in Apache Tomcat. AJP is a highly reliable protocol, so it should never be exposed to untrusted clients.
According to the experts of the cyber security consulting company, AJP is a binary protocol that allows you to roll back proxy requests from a FrontEnd web server to a BackEnd application server, effectively propagating all the information necessary for the request/response flow to be successful.
This protocol is enabled by default, with the AJP connector listening on TCP port 8009 and bound to IP address 0.0.0.0. Exploiting the vulnerability, an unauthenticated remote hacker could abuse this configuration to read web application files from a server, exposing the AJP port to untrusted clients.
By scanning with the Onyphe tool, experts detected that there are more than 170,000 devices with an exposed AJP connector that responds to AJP13 requests.
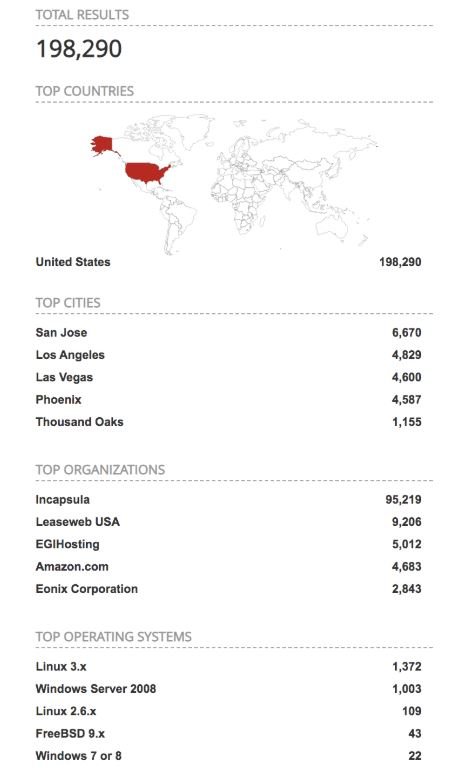
On the other hand, the scan with Shodan indicates that there are approximately 198 thousand 200 servers with AJP port (8009) exposed only in the U.S., mention the experts of the cyber security consulting company.
How do you know if your deployment is vulnerable?
You may be exposed if your infrastructure encompasses any component built using:
- Apache Tomcat, versions 6.x, 7.x, 8.x and 9.x
- JBossWeb Server, versions 3.1.7 and 5.2.0
- JBoss EAP, versions 6.x and 7.x
- Red Hat Enterprise Linux, versions 5.x ELS, 6.x, 7.x and 8.x
The risk of exploiting these failures is real, so vulnerable version users are advised to implement the following mitigation measures:
- Upgrade to the latest version of Apache Tomcat (9.0.31, 8.5.51 and 7.0.100)
- For Tomcat-based deployments, if your service is not using the AJP connector, disable it from <TOMCAT_HOME>/conf/server.xml
- For Tomcat-based deployments, if an AJP connector is required and cannot be disabled, update and set a secret password for the AJP conduit. Edit conf/server.xml
- For JBoss-based deployments, verify and edit the default AJP connector that is enabled by default only on standalone-full-ha.xml, standalone-ha.xml, and ha and full-ha profiles in domain.xml
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











