The coronavirus pandemic has created new problems of all kinds, and cybersecurity is no exception. Specialists from a cyber security course have detailed the detection of a massive phishing campaign that could reach up to 5 million individuals and companies, spanning six countries on most continents.
The emails used by the operators of these campaigns contain information allegedly sent by local authorities and in connection with COVID-19 disease. Emails include attachments that redirect users to malicious websites designed to extract their personal and financial data. These emails have been sent to users in Japan, Singapore, South Korea, India, the United Kingdom and the United States.
A few months ago, cyber security course experts from CYFIRMA assured that Lazarus, the well-known cybercriminal group funded by the North Korean government, was preparing a global phishing campaign, so researchers believe it is these hackers who are behind this attack. In addition, some details have been found that indicate similarities between the various emails related to this campaign, even though they have been sent to users in different countries. The main feature is that all selected countries have issued considerable economic stimulus to counteract the economic consequences of the pandemic:
- Singapore: This small nation’s government announced stimulus for nearly $100 billion local dollars to curb job loss
- Japan had emergency funds of approximately 234 trillion yen
- The Korean government has earmarked nearly $200 billion for emergency containment, supporting the country’s critical industry
- India announced a $300 billion credit program for small, medium and large enterprises
- The UK implemented multiple support programs to prevent job losses
- U.S. to invest an undetermined figure to prevent job loss
Users who receive these emails are highly likely to require financial support, so this is an ideal means of attack. The main objective of the operators of this campaign appears to be economic fraud, although experts from the cyber security course believe that they could also engage in the theft of information for sale on dark web.
According to information collected by CYFIRMA, hackers planned a massive attack in the six chosen countries for two consecutive days. Lazarus created seven different mail templates in order to tailor the campaign to each attacked country, even taking the real names of some local government agencies.
Hackers have used several legitimate-looking email addresses, such as the ones shown below:
- covid19notice@usda.gov
- ccff-applications@bankofengland.co.uk
- covid-support@mom.gov.sg
- covid-support@mof.go.jp
- ncov2019@gov.in
- fppr@korea.kr
Regarding the message sent to potential victims, this also differs by country:
- UNITED States: Hackers mention to users that their account has been selected by the authorities to receive a thousand-dollar financial support.
- UK: Attackers try to extract confidential information by email allegedly sent by the Bank of England offering financial stimulus.
- Japan: An email allegedly sent by the Japanese Ministry of Finance offers an additional 80,000 yen payment for all citizens and residents who complete a form.
- India: Cybercriminals offer supposed free testing for COVID-19 detection in residents of multiple cities in exchange for completing some online forms.
- Singapore: By usurping the identity of the Ministry of Human Resources, hackers deceive users by offering a payment of 750 Singapore dollars to employees of private companies and public organizations.
- South Korea: Hackers use emails allegedly sent by the local government to redirect users to malicious sites so they can extract their confidential information.
Below are some examples of email templates developed by hackers. Users are advised to ignore any similar email, as it is most likely to be a scam; As in any phishing campaign, the best way to protect yourself is to identify any potentially malicious email before opening it, in addition to not sharing personal information through this medium.
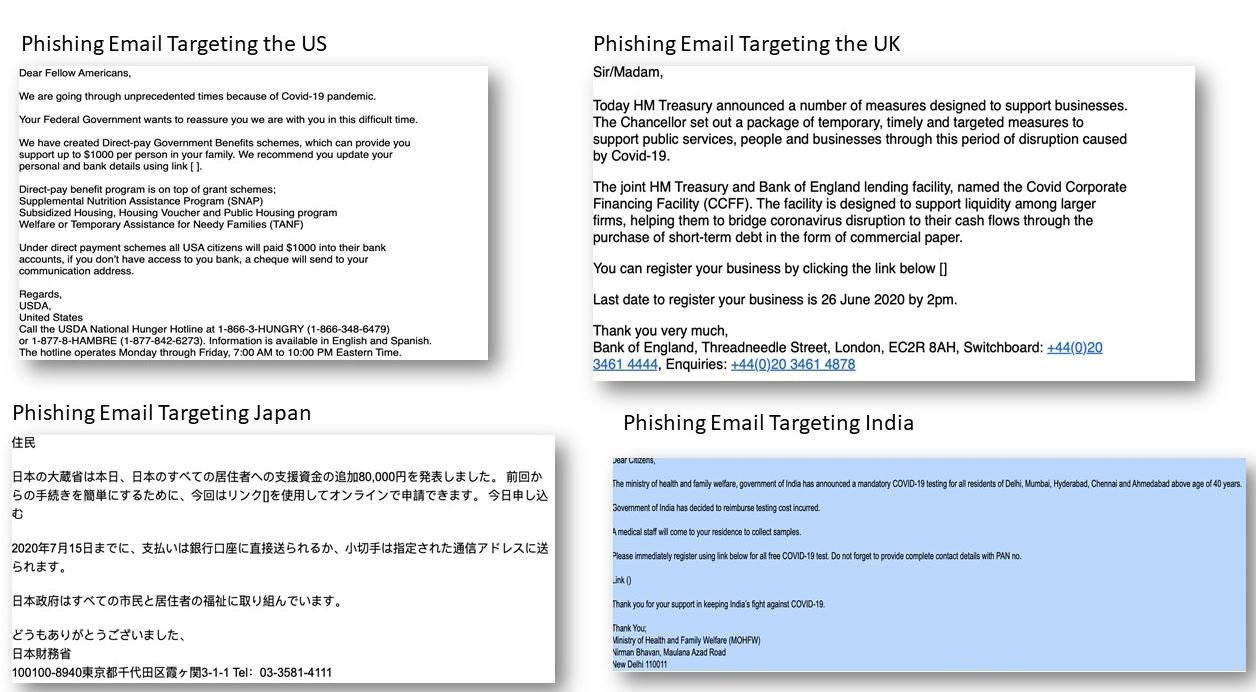
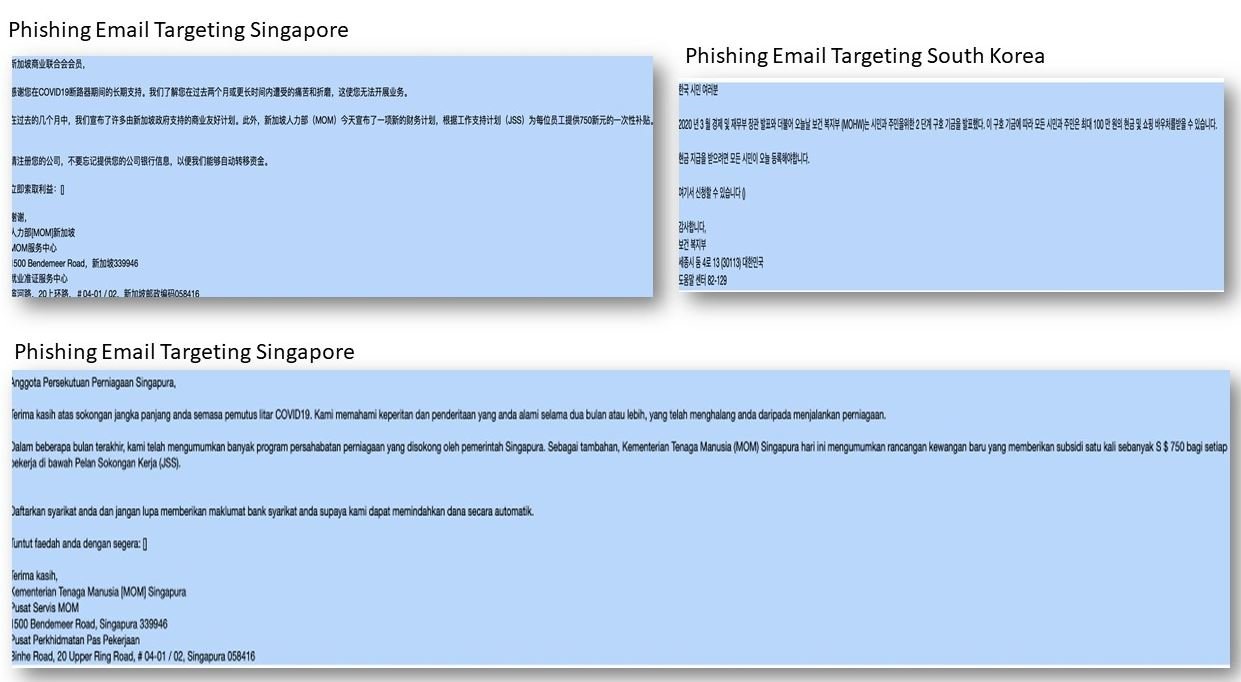
Researchers say this campaign will be launched over this weekend, specifically between June 20 and 21 (although it is not ruled out that it can be extended over the next few days).
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











