Introduction
We always prefer Operating system which has all penetration testing tools bundled in one. HackingTool is one of that kind, its an open-source framework and we use this for penetration testing. This tool has 73 hacking tools of different range. In this framework, we have all the tools in one place, which the penetration tester needs while testing. Researcher of International Institute of Cyber Security also agrees, that it is easier for hackers/penetration tester while testing/hacking any device or a network. During this post we will demonstrate step by step process on the usage of this tool.
Environment
- Os: Kali Linux 2020 64 bit
- Kernel version: 5.6.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/Z4nzu/hackingtool
root@kali:/home/iicybersecurity# git clone https://github.com/Z4nzu/hackingtool Cloning into 'hackingtool'... remote: Enumerating objects: 24, done. remote: Counting objects: 100% (24/24), done. remote: Compressing objects: 100% (23/23), done. remote: Total 174 (delta 9), reused 0 (delta 0), pack-reused 150 Receiving objects: 100% (174/174), 666.21 KiB | 853.00 KiB/s, done. Resolving deltas: 100% (91/91), done.
- Use this command to provide file permissions and enter into the directory.
- chmod -R 755 hackingtool && cd hackingtool
root@kali:/home/iicybersecurity# chmod -R 755 hackingtool && cd hackingtool root@kali:/home/iicybersecurity/hackingtool#
- Next, use this command to install the requirements sudo pip3 install -r requirement.txt
root@kali:/home/iicybersecurity/hackingtool# sudo pip3 install -r requirement.txt Requirement already satisfied: lolcat in /usr/local/lib/python3.8/dist-packages (from -r requirement.txt (line 1)) (1.4) Requirement already satisfied: boxes in /usr/local/lib/python3.8/dist-packages (from -r requirement.txt (line 2)) (0.0.0) Requirement already satisfied: flask in /usr/lib/python3/dist-packages (from -r requirement.txt (line 3)) (1.1.2) Requirement already satisfied: requests in /usr/lib/python3/dist-packages (from -r requirement.txt (line 4)) (2.23.0)
- Now, use this command to launch the tool. python3 hackingtool.py
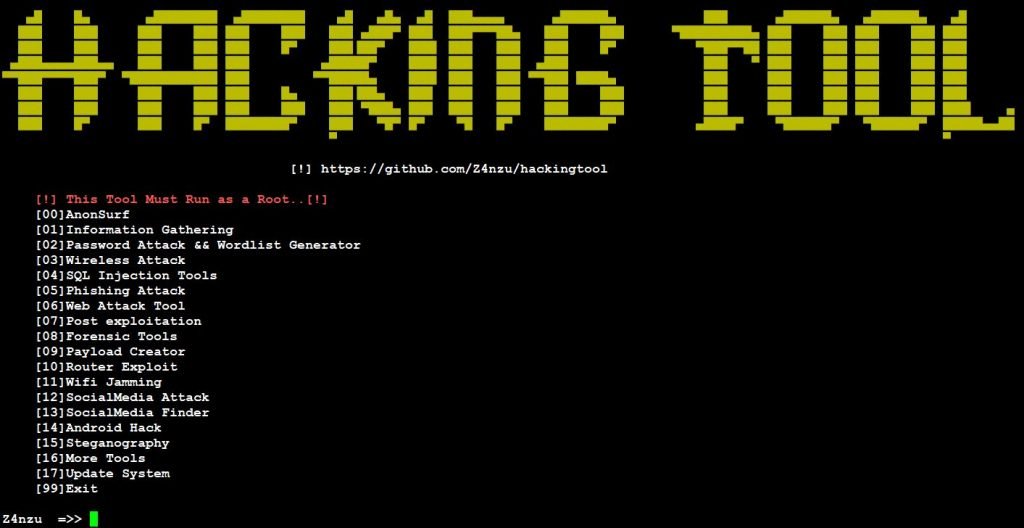
- Successfully launched the tool.
- Here, we see 15 different modules.
- Detailed below are different modules:
AnonSurf
What is Anonmously surf
Anonymously surf is a place where we can hide by changing our location. Here we are using the Anonsurf tool, this tool sets iptables settings to set transparent proxy via TOR network. This anonsurf tool sends all our outgoing traffic through the TOR network, so by using this we can be safe while browsing the internet.
- Here, choose 00 AnonSurf.
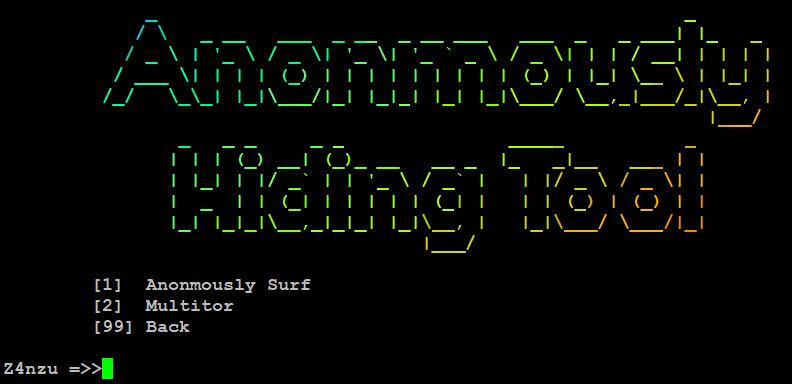
- Now, choose option 1 for Anonmously surf. Before launching this tool, we have to download the tool by choosing option 1.
sh: 2: boxes: not found sh: 1: echo: echo: I/O error [1]install [2]Run [3]Stop [99]Main Menu >> 1 Cloning into 'kali-anonsurf'... remote: Enumerating objects: 321, done. remote: Total 321 (delta 0), reused 0 (delta 0), pack-reused 321 Receiving objects: 100% (321/321), 167.72 KiB | 377.00 KiB/s, done. Resolving deltas: 100% (99/99), done. --2020-07-06 10:36:14-- https://geti2p.net/_static/i2p-debian-repo.key.asc Resolving geti2p.net (geti2p.net)... 91.143.92.136, 2a02:180:a:65:2456:6542:1101:1010 Connecting to geti2p.net (geti2p.net)|91.143.92.136|:443... connected. HTTP request sent, awaiting response... 200 OK =============================================================================================================SNIP============================================================================================================================== Processing triggers for systemd (245.6-1) ... Processing triggers for man-db (2.9.3-1) ... Processing triggers for kali-menu (2020.3.1) ... dpkg-deb: building package 'kali-anonsurf' in 'kali-anonsurf.deb'. Selecting previously unselected package kali-anonsurf. (Reading database ... 525307 files and directories currently installed.) Preparing to unpack kali-anonsurf.deb ... Unpacking kali-anonsurf (1.2.2.2) ... Setting up kali-anonsurf (1.2.2.2) ... Processing triggers for systemd (245.6-1) ... Processing triggers for kali-menu (2020.3.1) ...
- Now, choose option 1 to select anonsurf tool and choose option 2 to run the tool.
sh: 2: boxes: not found sh: 1: echo: echo: I/O error [1]install [2]Run [3]Stop [99]Main Menu >> 2 * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping IPv6 services: [ i ] Starting anonymous mode: * Modified resolv.conf to use Tor and Private Internet Access DNS * All traffic was redirected through Tor [ i ] You are under AnonSurf tunnel
- Here, we have successfully started the tor network.
- Now, type ifconfig.me in browser to verify our IP.
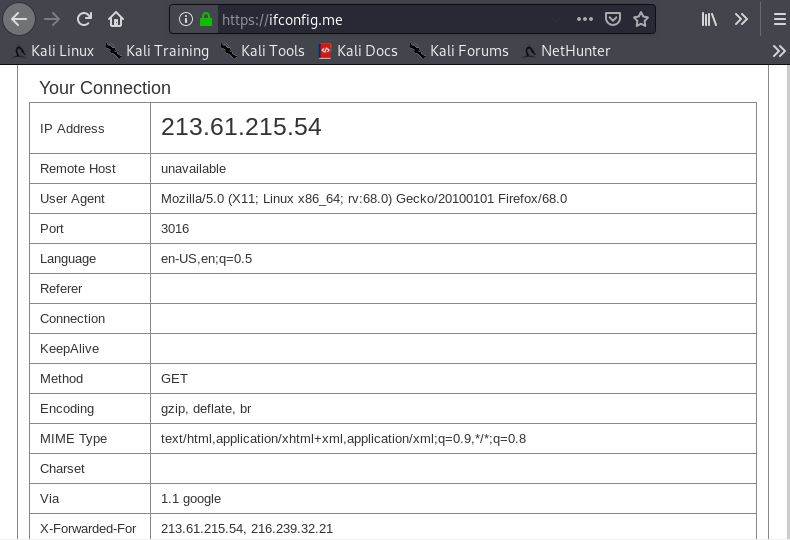
- Successfully we have changed the location.
Information Gathering
What is information gathering?
Information Gathering is collecting some unique information about the target it can be active or passive.
- Now, choose option 1 to use information gathering.
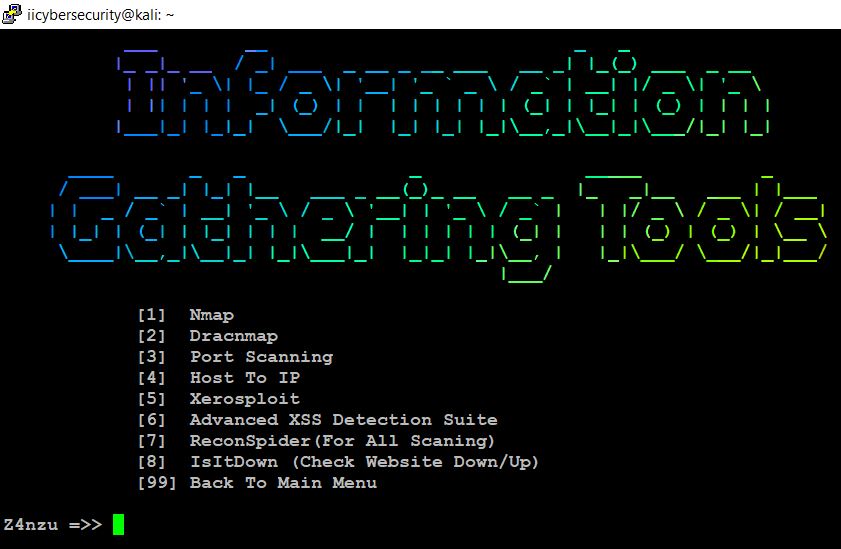
- Successfully launched the information gathering module.
- Now, choose option 5 to use “Xerosplit” tool.
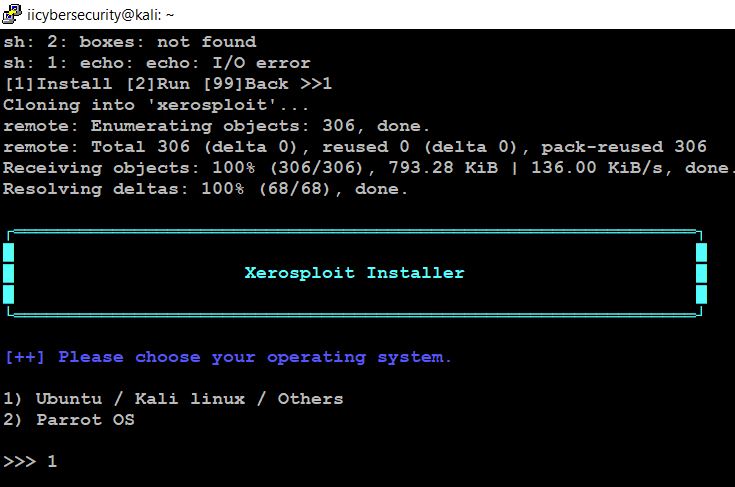
- Before running the tool, we have to install the tool by selecting option 1 Install.
- It automatically clone the file and we have to choose the operating system, depending on this it will download the requirements.
[++] Installing Xerosploit ... Hit:1 http://deb.i2p2.no unstable InRelease Hit:2 http://mirror.neostrada.nl/kali kali-rolling InRelease Reading package lists... Done Reading package lists... Done Building dependency tree Reading state information... Done build-essential is already the newest version (12.8). build-essential set to manually installed. git is already the newest version (1:2.27.0-1). =================================================================================================================SNIP======================================================================================================================== Installing ri documentation for network_interface-0.0.2 Parsing documentation for pcaprub-0.13.0 Installing ri documentation for pcaprub-0.13.0 Parsing documentation for packetfu-1.1.13 Installing ri documentation for packetfu-1.1.13 Parsing documentation for xettercap-1.5.7xerob Installing ri documentation for xettercap-1.5.7xerob Done installing documentation for em-proxy, net-dns, network_interface, pcaprub, packetfu, xettercap after 7 seconds 6 gems installed
- Now, choose option 5 for the Xerosploit tool, then choose option 2 to run xerosploit tool.
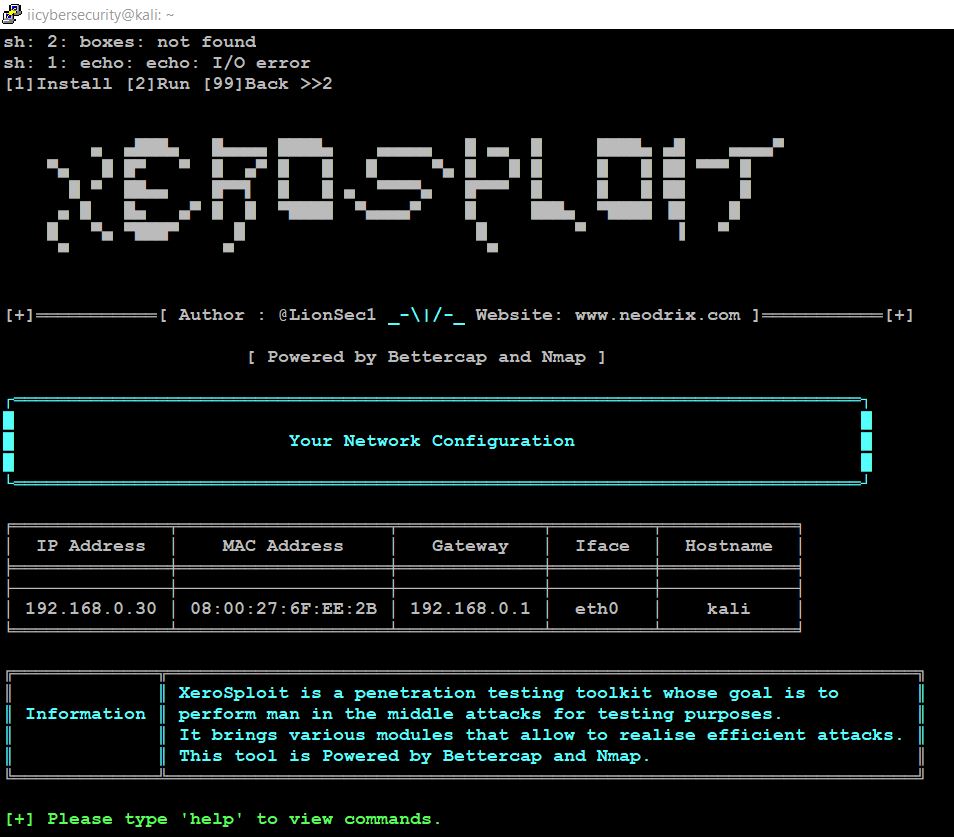
- Now, type help to view the options.
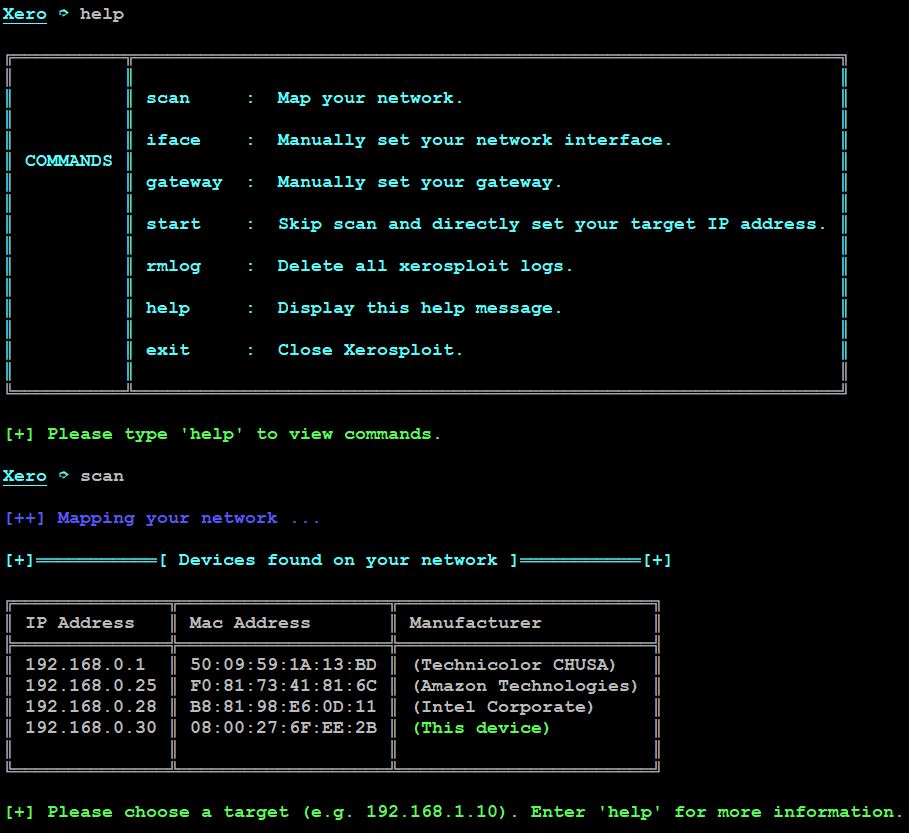
- Here, we have selected “scan” option. This will collect all the IP address and MAC address, which are connected to a LAN (Local Area Network).
Wordlist Generator
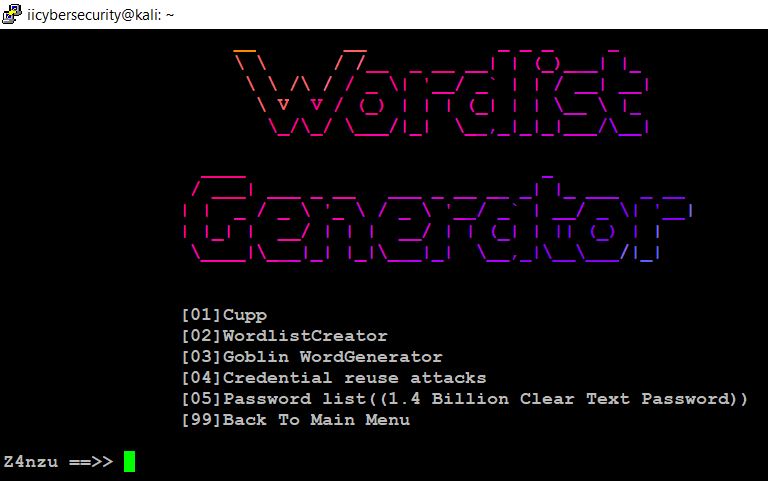
The Goblin word creator is used to generate the wordlist. This wordlist is useful for password cracking techniques in brute force attacks etc.
- Now, choose the option 3 to run Goblin wordCreator tool.
sh: 1: boxes: not found sh: 1: echo: echo: I/O error [1]Install [2]Run [99]Back >>2 ------------------ G 0 B L ! N 2.0 | WORDGENERATOR ~ by: UndeadSec and Sam Junior:@un00mz ------------------ [!] provide a size scale [eg: "1 to 8" = 1:8] : 1:3 [?] Do you want to enter personal data ? [y/N]: y [*] Fist Name: vemula [*] Last Name: nandu [*] Birthday: 20 [*] Month: may [*] Year: 1996 [!] Insert a name for your wordlist file: wordlist [?] Do you want to use uppercase characters? (y/n): n [?] Do you want to use special characters? (y/n): n [?] Do you want to use numeric characters? (y/n): y
- First, choose option 1 to install the tool and it’s requirements, then choose option 2 to launch the tool.
- Here, it asks to use the scale size for wordlist length. Then it will ask to use a few personal details and select the required option. Then the tool starts generating the wordlist.
v e Q p l a =============================================================================================================SNIP=============================================================================================================================== 003 004 005 006 007 008 009 000
- Successfully we got the list.
- If you want to generate wordlist offline then you can also use crunch tool.
Wireless Attack
What is Wireless Attack
The wireless attack can be of many types. Example like Man In The Middle Attack, DOS attack.
- In this module we have 7 different tools.
- WIFI – Pumpkin: WIFI – Pumpkin help hacker to create open-source fake wifi. If any victim connect to that wifi, we will be able to track his/her activities
- Pixiewps: Pixiewps tool is used brute force the WPS pin in offline. This tool is built-in C language.
- Fluxion: Fluxion is a wifi hacking tool. This tool doesn’t need any wordlist to crack the password. Using this tool we can hack two different ways manually reveal the hidden WIFI access and how to access hidden wifi.
- WIFITE: WIFITE is used to attack the WIFI to steal the credentials for this, this performs a dictionary attack with a high number of wordlist for this we need a wireless adapter.
- EvilTwin: EvilTwin is a hacking tool, using this tool hacker setups a fake WIFI network. If the victim connects to this wifi network, so it will be easy to steal the victim’s login credentials or other sensitive information.
if you want to learn all the tools then you can refer to the ethical hacking course offered by International Institute of Cyber Security.
SQL Injection tools
What is SQLMap
SQLMap is an automatic SQL injection tool. We can use this tool to find out SQLi vulnerabilities on a webpage and stealing the confidential data from the database server. This is an open-source and penetration testing tool.
Phishing Attack Tools
The main aim of Phishing Attack is to steal the victim’s credentials by creating the fake phishing page.
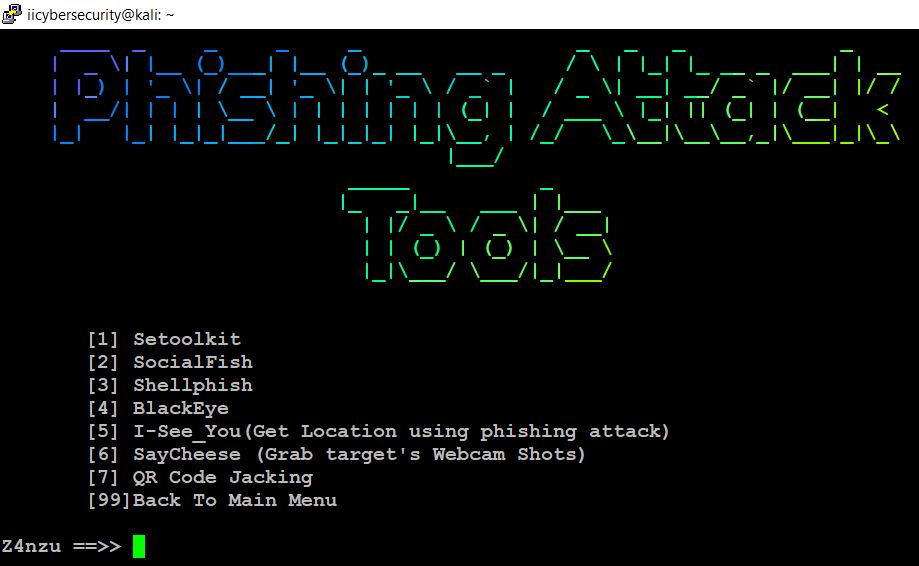
- Setoolkit: Setoolkit is also called a social engineering tool kit. We can use this social engineering tool to create the fake webpage to the victim to steal the victim’s credentials and we can also create the different payload to bypass the victim’s machine.
- SocialFish: SocialFish is used for a phishing attack. Using this tool, we can create phishing pages to steal the victim’s credentials and collecting those credentials using traffic collector servers.
- Shellfish: ShellFish is used for phishing attacks. Using this tool, we can create 18 popular phishing pages to steal the victim’s credentials and most of the social media phishing pages are available in this tool.
- BlackEye: BlackEye is used for phishing attacks. Using this tool, we can create 32 popular phishing pages to steal the victim’s credentials and most of the social media phishing pages are available in this tool.
- I See You: I See You is used for a phishing attack. Using this tool we can get the victim’s location details.
- Say cheese: Say cheese is used for phishing attacks. This tool creates a malicious link, if the victim opens this link it starts taking the webcam shots and sends back to the hacker’s machine using port forwarding techniques.
- QR code Jacking: QR code jacking is used for phishing attacks. This tool creates a malicious QR code, if the victim scan this malicious QR code with his account, the same hacker will able to access the victim’s account.
Web Hacking
What is Web Hacking
Web hacking is exploiting the websites by collecting information, scanning the websites with different tools, finding out the vulnerabilities, exploiting the website and stealing the visitor’s information, spreading viruses, etc.
- In the web attack module, we have 5 different tools.
- Web2Attack
- Skipfish
- SubDomain Finder
- CheckURL
- Blazy (Also Find ClickJacking)
- In the web attack module, we have 5 different tools.
Blazy
Blazy is another brute-force tool and very good error detecting tool, using this tool we can find out the CSRF (Cross-Site Request Forgery), Clickjacking, Cloudflare. This tool has a default username and password.txt file or we can also create our own username and password list file.
- Before launching the tool, we have installed this by choosing option 1. This will install the file and follow the same steps then chose option 2 to launch the tool.
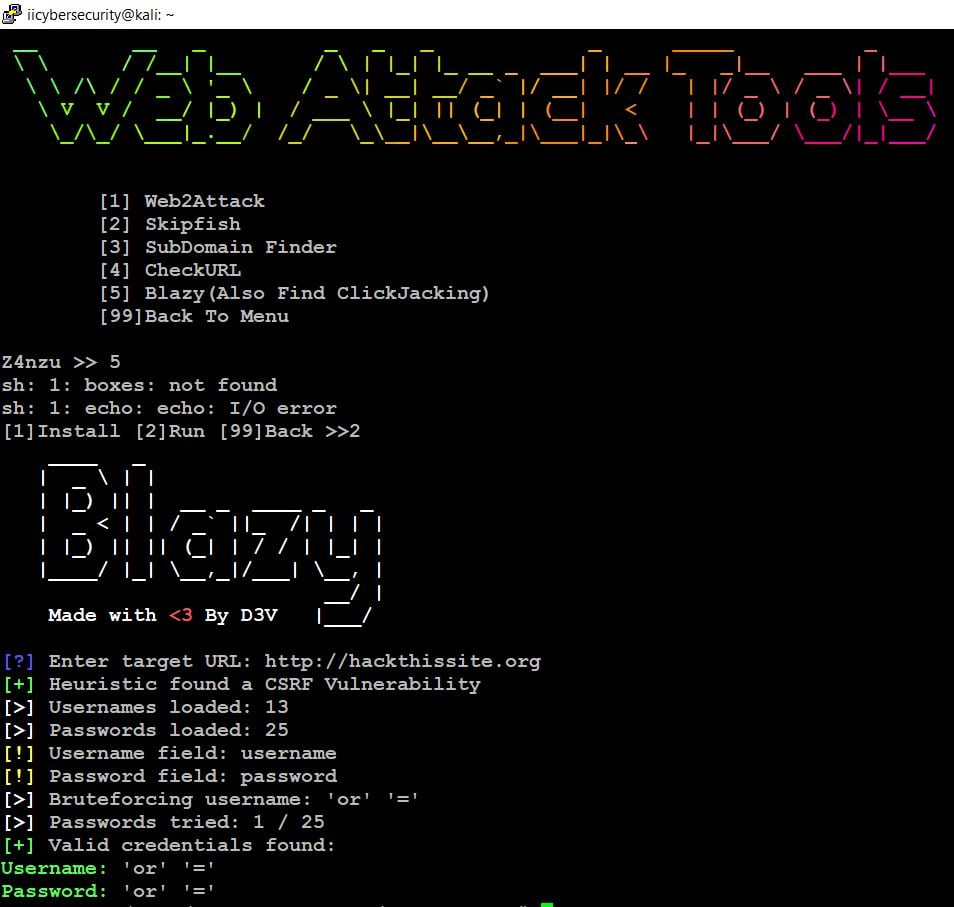
- Here, we have entered the target URL hackthissite.org. This tool scanned and found CSRF Vulnerability in this website.
Post exploitation
What is Post Exploitation?
We use the post-exploitation module after compromising the machine. In this process, the hacker’s aim is to collect the victim’s sensitive data.
- In post exploitation we have 2 different tool
- Vegile – Ghost in the shell
- Chrome Key logger
Forensics tools
The computer forensics tools are used to check the operating system after post exploitation in system or network.
- In the forensic module, we have 5 different tools
- Autopsy
- Wireshark
- Bulk_extractor
- Disk Clone and ISO Image Acquire
- Toolsley
Payloads
What is Payloads
The payloads is a simple scripts/malicious content file used by hackers to exploit any victims machine by simply executing this payload on the victims machine.
- In this module we have 6 different payloads
- The FatRat
- Brutal
- Stitch
- MSFVenom Payload Creator
- Venom Shellcode Generator
- Spycam
Router Exploit
Router Exploit is an open-source and powerful hacking tool. Using this tool, we can find the vulnerabilities in routers, Cameras, etc
- In this module, we have 2 different tools
- RouterSploit
- Fastssh
wifi-jammer
What is wifi-jammer?
WiFi-jammer is a powerful hacking tool, using this tool we can restrict any user while connect connecting to the wifi.
- In this module we have one tool
- Using Airmon
SocialMedia Finder
What is SocialMedia Finder
Social Media Finder is same like information gathering. In this we investigate different social media profile by using they usernames and they photos.
- In this module we have two different tools.
- Find SocialMedia By Facial Recognition System
- Find SocialMedia By UserName
Steganography
Steganography is the best tool for hiding any type of file like Images, confidential information, file, etc.
- In this module, we have 3 different tools.
- SteganoHide
- StegnoCracker
- WhiteSpace
Conclusion
We saw all the penetration testing tool bundled in HackingTool which can be used to perform penetration testing. Most of the tools are widely used in a real-time environment. Using this tool, it makes easier for penetration tester to do his/her job.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











