Although digital signatures in software or files are an indicator of trust, threat actors may be able to bypass this security measure, as mentioned by malware reverse engineering experts. A recent study by researchers at Ruhr-University Bochum in Germany has revealed that 15 of the 28 most popular PDF readers are vulnerable to an attack that allows hackers to modify the content of a digitally signed PDF document.
This method, dubbed “Shadow Attack”, involves exploiting the “view layers”, which refers to the various sets of content added on top of other elements within a PDF file. To do so, threat actors must create multi-layered documents and send it to the target user, who will need to add the digital signature with a benign layer on top of the malicious content.
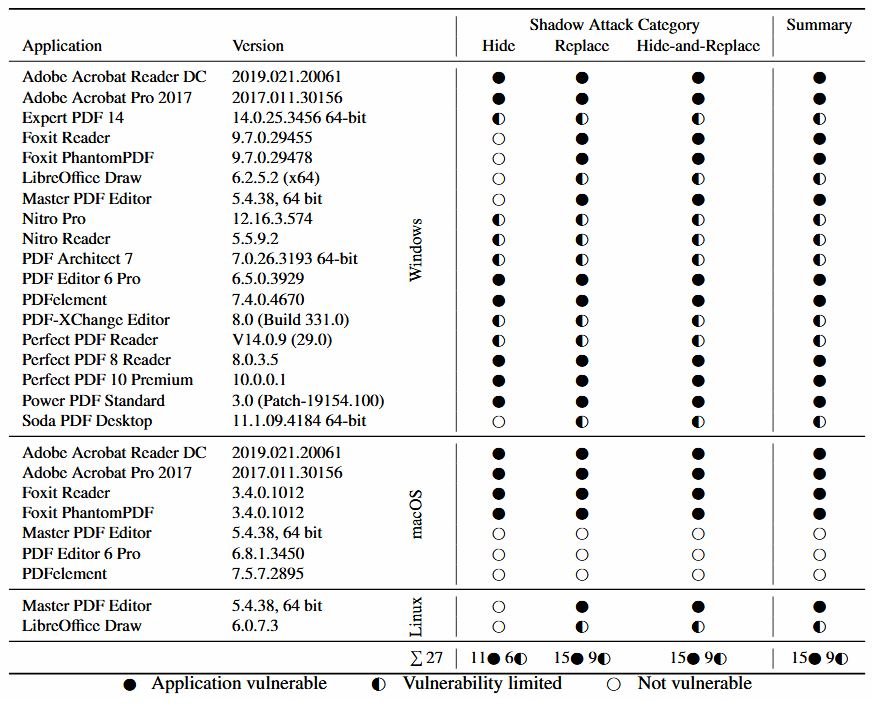
Altering the order of view layers does not modify the digital signature, the malware reverse engineering experts mentioned, so hackers will be able to use the malicious document as if it were a legitimate file. In other words, an attacker could modify a PDF document to be added as the recipient of a bank transaction, property ownership, and more.
Researchers found three variants of the attack:
- A hacker can use the Incremental Update feature of the PDF standard and hide a layer without having to replace it with another
- Attackers can also use the Interactive Forms feature to replace the original content
- A third variant consists of the combination of previous attacks; hackers use a second PDF document, replacing the original content with the above features
In their report, the researchers that this latter variant is the most dangerous, because it is possible to replace the entire contents of the document, except for the digital signature: “The threat actors can create a complete document that influences the presentation of each page, or even the total number of pages, as well as on each object it contains”.
Moreover, malware reverse engineering specialists mention that this attack variant is possible because PDF files allow unused objects to be present in their content, even when a digital signature exists. It should be noted that PDF viewer applications are not affected by this attack, as they remove unused objects by default.
This attack variant is really dangerous, although it’s not all bad news. PDF application manufacturers have already been notified about this new attack vector, so it’s only a matter of days before the fixes are ready for installation.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











