Oracle recently released its Critical Patch Update for October 2020, in which it first lists all updates to address failures in third-party components that cannot be exploited in the context of an Oracle product under the product risk matrix.
Oracle Critical Patch Updates are a set of updates to address security flaws detected over a given period. These patches fix vulnerabilities in Oracle code and third-party components included in company products and system administrators are encouraged to review these security alerts in detail.
For this update, Oracle released two versions of its alert, highlighting the company’s distinction between non-exploitable vulnerabilities in third-party components, in addition to the traditional warning of potentially exploitable failures.
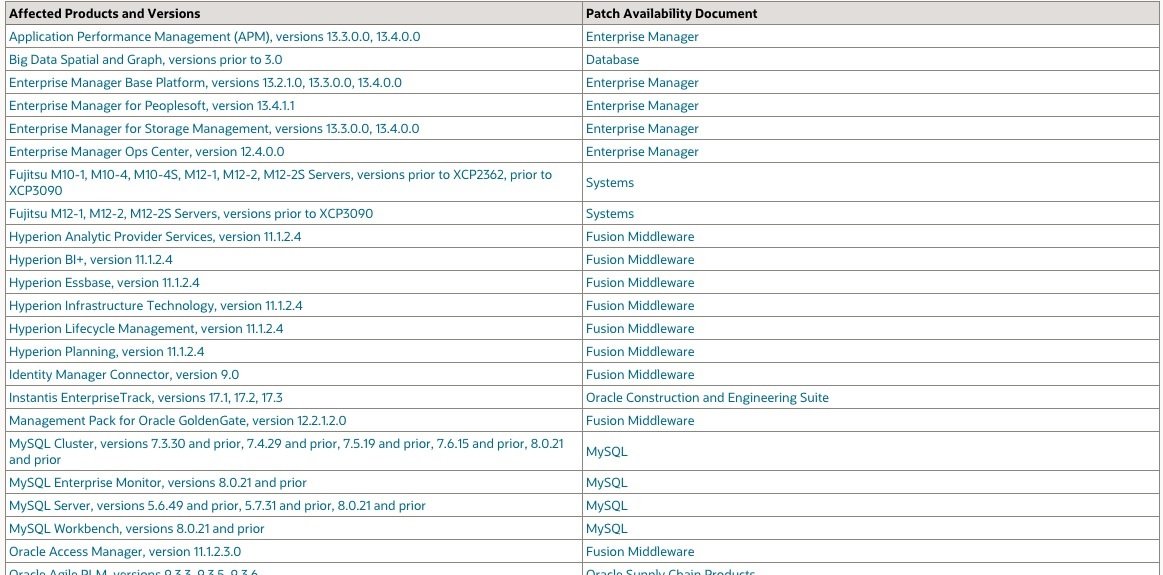
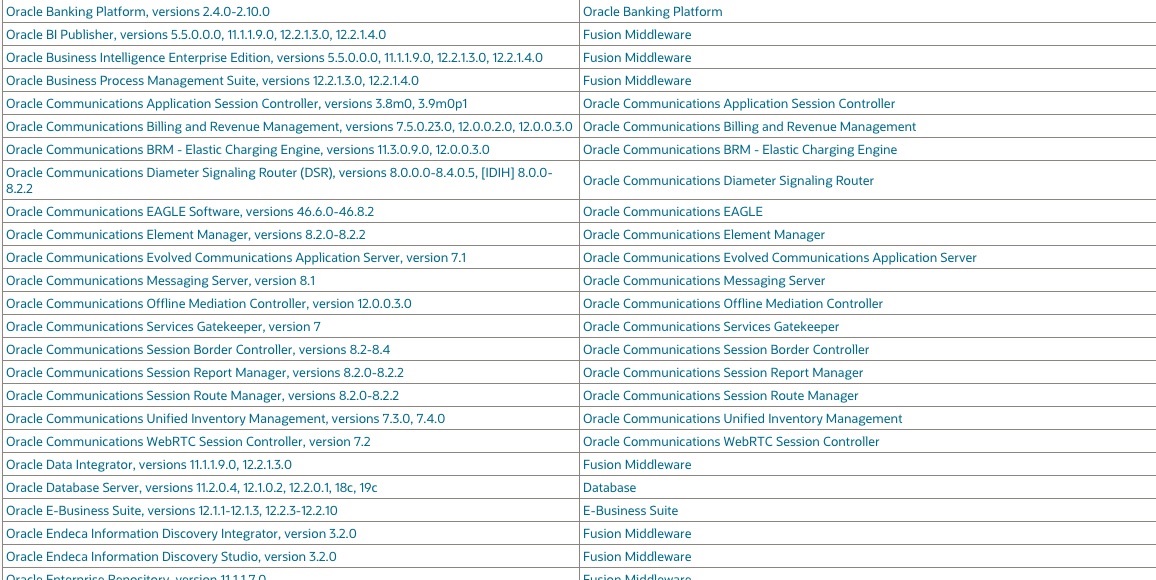
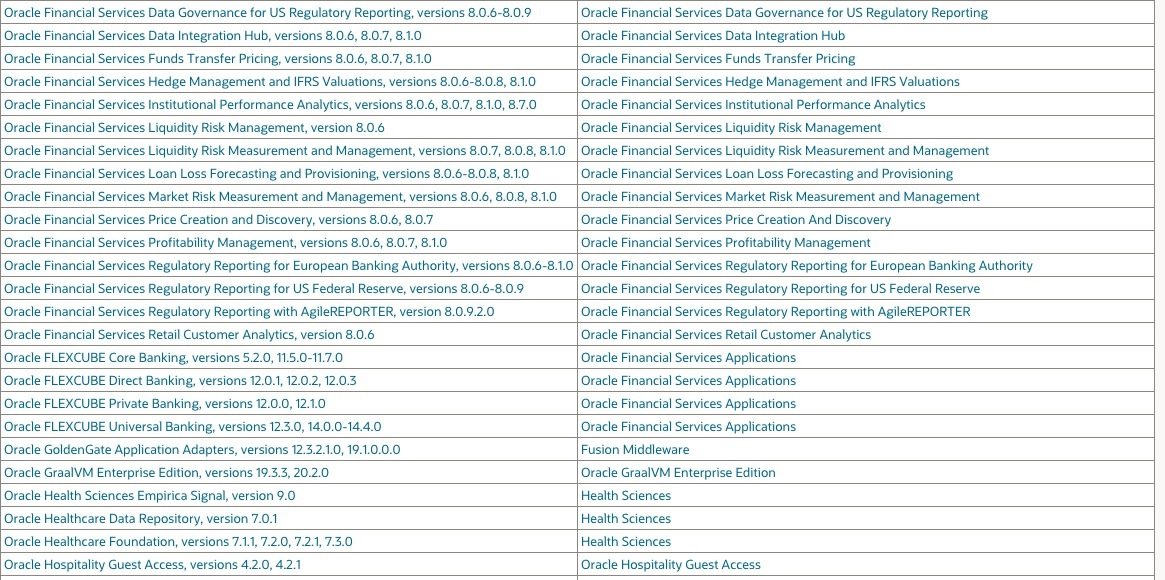
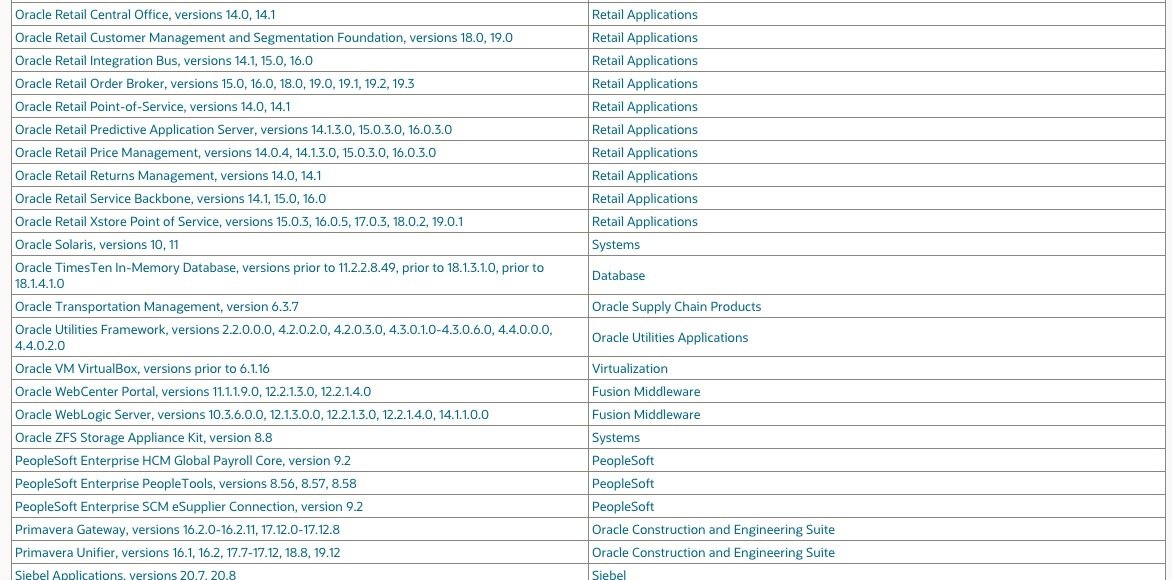
This update contains a total of 402 new security patches in a wide variety of product families. Oracle’s detailed list of objectives with this Critical Patch Update can be found on the company’s official platforms. On the other hand, below is a list of the corrected vulnerabilities and potentially affected products:
Active exploitation of any of these failures is a real possibility, so Oracle strongly recommends that users of vulnerable products update as soon as possible. If patch deployment is not feasible at the moment, specialists mention that it is possible to mitigate the risk of attack by blocking network protocols abused by threat actors.
Some of the attacks described by Oracle require elevated privileges or access to specific packages, so users may be able to test changes on non-production systems to mitigate the risk of exploitation; however, administrators should note that these are not long-term solutions, so installing the Update is the best measure to mitigate these attacks.
The release of oracle’s next major update is scheduled for January 21, 2021.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.