Security specialists reported detecting a malicious campaign operated by the Hacking Group DoNot exploiting Firebase Cloud Messaging (FCM), Google‘s cross-platform cloud messaging service for deploying Android malware over the Internet.
Researchers argue that DoNot is using FCM as a communication mechanism to connect to its command and control (C&C) servers in order to evade detection of some security mechanisms using an attack dubbed Firestarter.
DoNot hackers are experimenting with new attack variants to maintain an entry point into the victims’ machines, demonstrating how dangerous this hacking group is and the great development they have achieved in just a few months.
With regard to the victims of this group, DoNot’s main targets for attack lie in Pakistan and India, especially Pakistani government officials and non-governmental organizations in Kashmir. According to a report released by Cisco Talos, threat actors use APKs not available in the Play Store with file names such as Kashmir_Voice_v4.8.apk, kashmir_sample.apk and other similar variants.
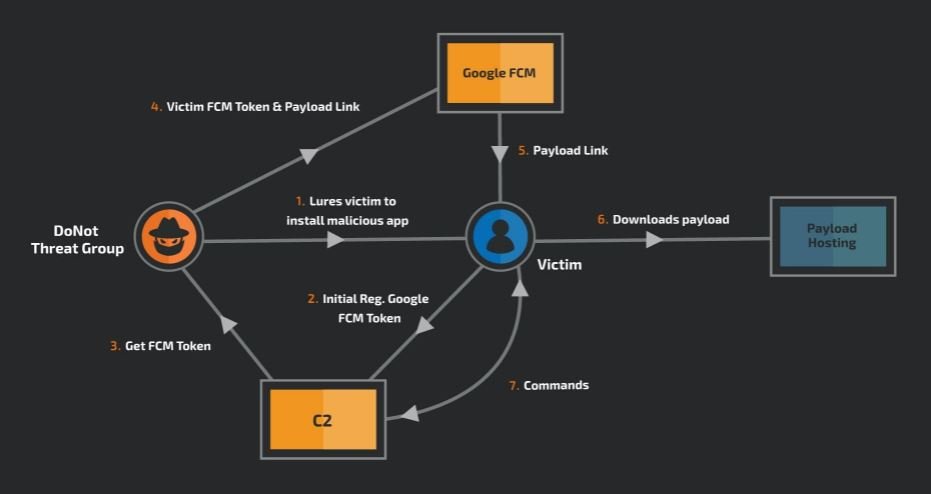
Using social engineering, threat actors seek to convince victims to install these malicious apps by claiming that they are only harmless chat platforms. If the app is downloaded and installed, a message will appear informing users that the app is not compatible with their device, so the file will be uninstalled. Although the application icon disappears, the software is still present on the device.
Once it starts operating in the background, the application downloads a payload when communicating with its C&C server via FCM. Since the final payload is not built into the malicious application, it was impossible to analyze it as part of this investigation, which makes this attack variant much more dangerous for its potential targets.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











