Secure-D specialists identified that a popular Android app was responsible for a fraudulent transaction campaign that could have generated up to $27 million in fake charges for users. The VivaVideo app has been making millions of Premium subscription attempts, delivering invisible ads to prevent users from detecting them.
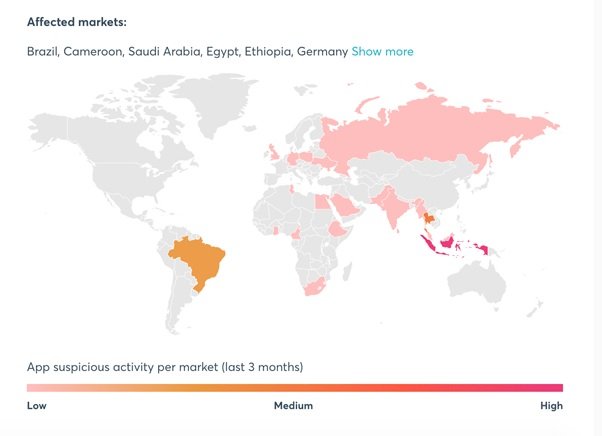
According to the report, Secure-D detected and blocked about 20 million suspicious mobile transactions, all originating from the VivaVideo app, for Android mobile systems. This fraudulent campaign affected VivaVideo users in at least 19 countries, including Brazil, Indonesia, Egypt and Thailand.
Previous Secure-D reports had VivaVideo considered it one of the most suspicious apps available for Android devices, so experts considered it relevant to conduct a detailed investigation of this tool. The application is developed by Chinese company QuVideo Inc.
It should be remembered that VivaVideo is a free app for Android that offers basic video production functions such as editing tools, effects, music overlay, among others. Users from all over the world have turned to this app to edit their posts on Instagram, TikTok and other social media platforms, registering up to 100 million installations.

Arbitrary actions detected in the app
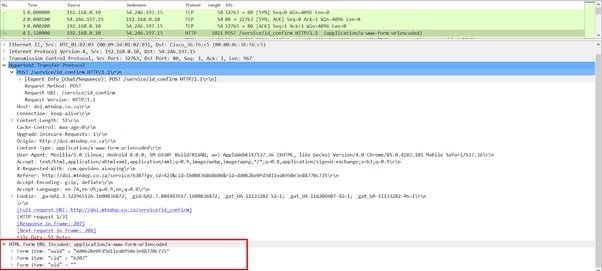
Secure-D experts detected in real time multiple subscription attempts that the app executed without user permission. These attempts were more than obvious when analyzing the network logs produced by VivaVideo (v7.3).
Subsequently, researchers performed a static code analysis to learn more about the behavior of this app, discovering that VivaVideo (v8.4.2) is able to verify the existence of emulation frameworks, so it can stop its fraudulent activity when it is being monitored.
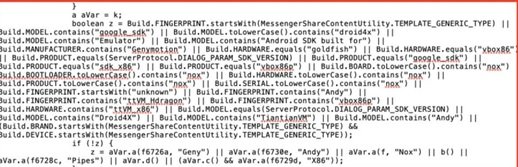
Secure-D concluded that the app contains code snippets to verify the existence of monitoring software installed on the user’s device. Although it might seem like a common practice, this is a method employed by sophisticated groups of scammers.
Too much permission for a simple video editing app
When installing the app, VivaVideo prompts the user to grant their permission to access image gallery, location data, apps running in the background, among other system details.
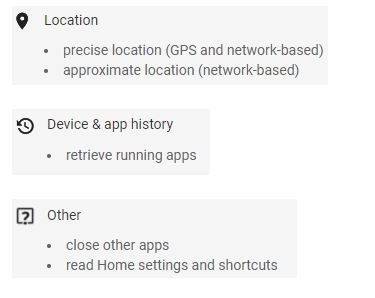
Without a doubt these are more permissions than the app requires, which makes it a highly intrusive tool.
Using tools banned by Google
A couple of years ago Google began a thorough investigation into three potentially malicious software development kits (SDKs) that would eventually be removed from the Play Store along with their developers. One of these company-banned SDKs was Batmobi, which abuses user permissions to perform click injection attacks.
Batmobi is the SDK used by VivaVideo developers, one more reason to doubt the legitimacy of this application.
Had they not been blocked, these attacks could have resulted in losses of nearly $27 million through unwanted charges and unsolicited Premium subscriptions. VivaVideo users may want to reconsider their use to edit their social media posts.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











