Public organizations and private companies around the world use website blocking tools as a simple method to prevent employees from wasting time on entertainment platforms, social media, or any other website unrelated to their work activities.
While setting these restrictions strengthens the security of enterprise networks, not all employees in an organization require the same level of Internet access, so many believe that more complex tools need to be used to avoid encountering the padlocks established by IT. Below are some ways to circumvent these restrictions by obtaining administrator permissions, although their use is entirely the responsibility of each person according to pentesting experts from iicybersecurity.
Obtaining the necessary rights on one computer begins with loading another operating system with a set of hacking utilities. There are online articles describing many methods for creating multi-boot USD drives, although here you can find the most important aspects of this practice.
Booting a system from a USB drive is complex, even with physical access to the target device. Booting from arbitrary media was not a problem before the arrival of EFI. Simply enter the BIOS settings and change the boot order in the boot section. On some computers, I had to press Delete, on other F2; in any case, the required key was indicated on the screen or in the manual. UEFI now uses a list of reliable bootloaders and two different boot sequence modes, and Windows 8, 8.1, and 10 can be started to accelerate directly from EFI without any suggestion to enter the settings according to pentesting experts.
If you see Windows load immediately and don’t have time to do anything, wait until it starts and do one of the following:
- Click “restart” on the Windows Welcome screen while holding down the shift key
- After downloading, go to “→ And Security → Recovery → Special Boot Options”. Click Restart Now → Troubleshooting → Advanced Options → Boot Options
- You can also enter shutdown.exe/R/O on the command line
Regardless of the method chosen, it will restart with a selection of parameters and can be found in BIOS/UEFI settings. If the rights are strictly limited and it is impossible to enter Windows 10 settings using the software method, you can try to physically disable the HDD/SSD. Then, on the next boot, an error message will appear and the item will be displayed to enter UEFI.
Although it seems difficult to turn off your computer’s HDD manually, this is a really simple process. You should only place the switch on the model in question and remove part of the plastic cover from the enclosure.
Quick start using a USB stick
The option to select a bootable device, implemented in some firmware, can facilitate this process. When you turn on the computer, in addition to the message “Press [key] to enter the settings”, one more will appear: “… or [key] for the start menu.” Usually these are the Enter, F1 – F12 keys, their combinations with the Alt, Ctrl, Ins, and Esc keys. A complete list of options would take more than one page, so it’s best to look for the answer in the manual for a specific motherboard.
Regardless of the way, it’s critical to access the BIOS. You will most likely also need to change the startup list option to boot from a USB stick. By default, it is in the new UEFI mode and the USB device uses GRUB that runs through the MBR. In other words, we need the old Legacy/CSM mode, or both, but with the classic priority: Legacy/CSM+UEFI, known as Load Legacy Option Rom. The Secure Boot secure boot method is also disabled there. According to pentesting experts optionally, you can add your own trusted bootloader keys instead of disabling it.
Another obstacle that we will have to overcome is the password in BIOS/UEFI, which is usually written to the back of the battery on the motherboard, although this is resolved by removing the component to see the password. If the motherboard information is lost, you can log in to Google and search for the manufacturer’s password, common for all motherboards in the same series.
In addition, another way to reset the BIOS password using software is to generate an error in the checksum of the data blocks, something that can be realized using CmosPwd, utility created by Christophe Grenier. However, this method will not work if the utility is locked with an antivirus solution.
Get administrator access
Once we boot the system from the USB drive, we are ready to run some exploits. The first problem users face is the lack of read/write access to some directories.
These restrictions are set at the level of access control lists on the NTFS file system, but only the Windows system itself should verify them. Other individual operating systems and utilities may ignore these restrictions; for example, Linux and data recovery software do not use WinAPI, but access the disk through their drivers or directly. Therefore, they simply don’t see the security attributes set to NTFS and read it all.
It is possible to make a copy of any data that is already at this stage. The only possible obstacle is partition encryption. Built-in BitLocker protection will help you overcome ElcomSoft utilities (by the way, like many other virtual fences), but TrueCrypt, VeraCrypt and other serious cryptographic containers will need to be opened differently. The easiest way to do this is through social engineering methods, as the technical protection of these funds is an order of magnitude greater than the psychological protection of the owner.
Changing access rights is easy. By booting the system from a USB stick, it is possible to obtain privileges on the same Windows. However, it is more interesting to retain host rights, so administrator access is required. The best way to do this is to use the NT Password Edit password reset tool, developed by Vadim Druzhin.
According to pentesting experts in some cases this tool is sufficient, although similar tools like Active@ Password Changer provides better capabilities.
Password Changer also allows you to reset the password for any account and knows how to unlock it if it was previously disabled. Reset Windows Passwords has even more features. With your help, you can not only reset passwords, but also cover hacking traces.
Another option is to add a new user to the system, give them the desired rights and hide this account. Once this is done, you can sign in with a regular account without arousing suspicion and, if necessary, run any program on behalf of an account that you know only with full access. Of course, it won’t be possible to hide it completely, but at least it won’t appear on the welcome screen. To do this, simply change the UserList subkey in the registry.
Find or create the SpecialAccounts section, if you can’t find it. In this section we search for or create the UserList subsection, and there is a new DWORD parameter with the hidden account name. If you assign it a zero value, the corresponding account will not be displayed eer on the welcome screen or in the general list on the control panel. You can go further and strengthen the conspiracy. To this end, we look for the keys with the revealing name
We assign a value to the first 0x00000001 and the second 0x00000002. The current and last used account will also disappear from the lock screen.
As noted earlier, most permissions on Windows work computers are set at the NTFS file system level. It’s time to remember file streams and syntax functions. According to UNC, two points separate a drive letter from an additional path. In NTFS, this character is also used as a separator between the actual file name and the associated file stream.
According to pentesting experts if the rights set by each Windows file or directory are correct, there is no difference in how system files are accessed. This will be blocked by default, although rights setting is a long-term routine that has been simplified using third-party programs.
For example, if you do not have access to a passwords.txt file, the following command will still display its contents on the screen:
more & lt; passwords.txt :: $ DATA
This should not work if read/write restrictions are set correctly, but administrators often do not bother auditing access rights for each object in the file system. On a real computer, you often get an explosive mix of inherited and explicitly assigned rights.
There are situations where the administrator denies access to a subdirectory for certain users, but leaves them full access to top-level directories. In this case, an obvious contradiction arises and the restrictions are no longer applied. For example, not having read permission on a file does not work if you are allowed to read the list from the directory that contains it. The same goes for deletion.
Create a secret partition without access rights support
Sometimes administrators only prohibit file execution. For example, to prevent the user from starting a program, you can avoid this limitation by simply copying it to a FAT32 partition (as an option, on the same flash drive), where access rights cannot be set. They are simply not compatible with the file system itself. If it is too risky to constantly use a USB flash drive, it can make it more complicated. Run any disk partition editor from it once, reduce the system size, and create a new FAT32 volume in free space and (optionally) hide it.
Hidden partitions are not mapped to a letter on disk, so it does not appear in the file explorer. It can be mounted on Windows with Disk Management – diskmgmt.msc.
You have already assigned the necessary rights to run this tool in the last stage, when you learned the administrator password or created a new one.
If documents, databases, or media files were copied to the FAT32 partition, they will open smoothly. Nothing will stop you from running simple software that is installed by unpacking: in a new place everything will work as before. With the programs installed, not everything is so simple. They’ll have to change the routes in the settings. These are files .cfg and .ini in the same directory or registry keys. You can change the keys using a remote registry editor started from a USB flash drive on the same WinPE.
With this tool, you can avoid other restrictions recorded in the registry.
Bypassing the security of Kaspersky Antivirus
Most bans on user actions on Windows are implemented through NTFS registry and access rights. However, there is another option: the installation of specialized control programs.
For example, Kaspersky software loads its own drivers from .windows.system32.drivers and sysnative.drivers. With its help, it intercepts system calls and file system calls, controlling both program operation and user actions.
Kaspersky Anti-Virus SOS and Windows Workstation versions check the name of the main file. Therefore, simply do the following:
- Rename avp.exe (starting in WinPE or Safe Mode)
- Run the renamed file after a regular login
- Go to the “→ Settings” menu; turn off self-defense and password protection
- Save settings, download antivirus and rename them
Optionally, you can set your own password so that the administrator understands how you unknowingly suffered. This method will not work if the antivirus is centrally configured on your computer. However, you can always temporarily neutralize the guard in the manner described above.
It is easier with new Kaspersky products, whose script automatically detects the installed version of the antivirus and resets the specified password. In the batch file, you can see that in 32-bit and 64-bit versions of Windows it is stored in different registry branches:
HKEY_LOCAL_MACHINE – SOFTWARE – KasperskyLab – [product_name] – settings
Therefore, simply run this bat or edit the registry manually from WinPE. Simply query these branches and set the EnablePasswordProtect parameter to a null DWORD value according to pentesting experts.
Add a Trojan
The multiboot flash drive is a real Swiss knife. After you download it, you can unlock hidden accounts, reset passwords, edit the registry, and generally do anything. There’s only one problem: you can tell. Therefore, we will make an additional hole that does not require external tools. You can also create it through the recovery console. Either way, you can make a copy of utilman.exe then replace it with cmd.exe. First, let’s make a copy of the original file.
copy%windir% – system32 – utilman.exe%windir% – system32 – utilman-new.exe
Then overwrite the original .exe with cmd.exe:
copy%windir% – system32 – cmd.exe%windir% – system32 – utilman.exe
The drive letter (system partition) in the %windir% variable does not have to be C:. It can be found using the diskpart utility, the volume of the command list.
After replacing .exe cmd.exe, the next time you start Windows, you will see the familiar welcome screen. Only when you click “Accessibility” will the command line now open.
You can do everything in it as usual. For example, you can find out the current list of computer network user accounts and change their settings. It is possible to do anything with any account: turn on and off, change passwords, change their expiration dates and more. For more information about syntax, see .aspx) in the Microsoft website help.
We’ll talk more about politicians a little later (I don’t like politicians), but for now let’s take a look at a simple example: restricting the launch of programs through administrative templates.
Administrators like gpedit.msc editors. One of the most requested settings is called “Run only specific Windows applications”. Typically, with this tool, the office plankton can only run whitelisted applications. Word, Excel, calculator and other harmless things are incorporated. All other executable file names are automatically blocked. Therefore, we take the same cmd.exe or totalcmd.exe, rename it to winword.exe and use it calmly. You can view (and change) constraints through the same remote registry editor in WinPE. They are registered in this thread:
HKEY_CURRENT_USER \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer \ RestrictRun
Altering domain policies
In a domain, computers are centrally controlled by group policies, but this barrier can be overcome. The simplest way is to prevent policies from loading. To do this, start Windows in safe mode or simply disconnect the machine from the local network when it is powered on. According to pentesting expert in the second case, you can log in to the domain even without a physical connection, because Windows caches the data from the previous login, and if the connection to the domain controller is lost, verifies it locally.
Bypass advanced bans on program execution
The domain uses a more advanced tool to restrict the launch of programs: SRP. You know how to check, in addition to the names of executable files, their paths, hashes, and certificates. You can’t fool it by simply renaming the executable. How to be? Similarly: simply prevent the system from seeing these restrictions.
By default, only program launches are controlled, but not dynamic libraries because full verification requires too many resources.
In a domain, computers are centrally controlled by group policies, but this barrier can be overcome. The simplest way is to prevent policies from loading. To do this, start Windows in safe mode or simply disconnect the machine from the local network when it is powered on. In the second case, you can log in to the domain even without a physical connection, because Windows caches the data from the previous login, and if the connection to the domain controller is lost, verifies it locally.
The gpdisable utility injects the library into any process and stops seeing the group policy prohibitions of the corresponding registration branch.
HKEY_LOCAL_MACHINE – SOFTWARE – Policies – Microsoft – Windows – Safer – CodeIdentifiers
Eric Rachner then implemented a similar tactic in his Group Policy Bypass Tool; then, he was still the head of the Application Consulting Engineering (ACE team) team at Microsoft.
Both programs have the same disadvantage: to run them and inject the .dll, the user must already have some administrative privileges. But if it does, then the meaning of these utilities is lost. Nothing prevents the local administrator from manually removing restrictions on domain policies.
The ACROS Security blog five years ago described another way to circumvent domain restrictions, which is applicable in a real situation with the rights of a simple user.
- Rename the injectable library gpdisable.dll to deskpan.dll
- Create a new folder called files. .42071714-76d4-11d1-8b24-00a0c9068ff3
- Place the deskpan file.dll in it and open the folder
- Create a new document .rtf open it
This loads WordPad, which loads gpdisable.dll into memory as deskpan.dll. Let’s take a closer look at the method.
Create complicated shortcuts
The tricks in the previous section are possible because in Windows, along with normal folders, shortcut folders with predefined functions are used. For example, “My Computer”, “Control Panel” or “Printers”. All are implemented as COM servers with known class identifiers (CLSIDs). There are more than a hundred of them, so here are listed only the new ones in Windows 10:
- .3936E9E4-D92C-4EEE-A85A-BC16D5EA0819: Frequently used folders
- .018D5C66-4533-4307-9B53-224DE2ED1FE6 – OneDrive
- .679f85cb-0220-4080-b29b-5540cc05aab6 – quick access panel
- BB64F8A7-BEE7-4E1A-AB8D-7D8273F7FDB6: Security and Service
Any of them can be used to secretly start your programs.
In the following example, a subfolder was created in the user’s directory named LPT3. BB64F8A7-BEE7-4E1A-AB8D-7D8273F7FDB6. The name before the dot is prohibited in Windows because it matches the port name. To create it, you must obfuscate the shell with the sequence . . . and pass the full path to the directory created as an argument enclosed in quotation marks.
After this command, we get a directory that cannot be deleted by conventional means, which is displayed as LPT3 in the browser. When you double-click it, the contents of the folder will not open. Instead, the Security and Service Center is launched. In this case, executables within the folder can be accessed from batch files (.bat and .cmd) and from the registry (for example, in the start section).
Turn on the USB (in 7 different ways)
One of the obstacles to using a flash drive may be for the administrator to disconnect the USB ports from your computer. This can be done in different ways, so different counterattack methods are required.
1. Ports are physically disabled
This is only possible with additional ports that are wired to the motherboard. The rear ports are welded on the motherboard itself, and there are at least two of them. Therefore, bring a penny hub from home, connect it instead of a mouse or keyboard, and connect all standard peripherals through it. Leave the second one for the bootable USB flash drive.
2. Ports are disabled in BIOS/UEFI
The administrator can disable both ports completely (a rare case) and a separate USB boot option. It is she who is responsible for the ability to boot from a USB device. We’ve already figured out how to enter BIOS settings, and it won’t be difficult to find the desired option.
3. USB drivers removed
Smart administrators are simply destroying USB drivers through device manager, but that won’t stop you. The absence of drivers will not be too much to boot from a USB flash drive. By becoming a local administrator, you can easily install the missing drivers; Windows itself will be offered to do so.
4. Some USB devices are locked
A more subtle method is to prohibit the use of USB drives. However, other types of USB devices continue to work. A restriction is established through the registration branch
HKEY_LOCAL_MACHINE – SYSTEM – CurrentControlSet – Services – USBSTOR
When the smart parameter is set, the use 0x00000004 of flash drives and external drives is prohibited, and when 0x00000003 is allowed. You can deal with this with the same method as in the previous paragraph: boot from the USB flash drive and change the USBSTOR section through the offline registry editor.
When the Start parameter is set, the use 0x00000004 of flash drives and external drives is prohibited, and when 0x00000003 is allowed. You can deal with this with the same method as in the previous paragraph: boot from the USB flash drive and change the USBSTOR section through the offline registry editor.
5. USB drives are prohibited through Group Policy
The Group Policy Editor allows you to define an administrative template that denies access to removable storage devices. Boot back from the USB flash drive, find out the local administrator password (or restart it if it was not possible to find out), along the way, activate the account if it was disabled. After that, run gpedit.msc and turn off the ban.
6. Restricted rights to read the usbstor.inf and usbstor.pnf files in the directory – Windows – Inf
Another trick with NTFS rights. If these files are impossible to access in a limited account, flash drives will not connect. We use the rights of a local administrator or simply move these files via WinPE to a FAT32 volume. After returning to the inf, the access rights will disappear.
7. The connection of devices via USB is controlled by a separate program
To help administrators, many utilities have been written to restrict the use of flash drives and external drives. Most of these programs simply change the value of the registry key mentioned above, but there are also advanced options. These can remember the flash drives allowed by volume number (VSN – Volume Serial Number) and lock the rest. You can simply download the processes of these programs from memory or replace VSN. According to pentesting expert This is a 32-bit value that maps to a volume when formatted with the current date and time.
An unexpected obstacle to the use of flash drives arises on computers with a mediocre power supply (reading, on most cheap work machines) without any effort on the part of the administrator. The fact is that the 5 V bus sinks so much that the flash drive does not have enough power. In this case, the other device from the adjacent USB port (paired) or use an active hub with its own power supply. Through it you can power at least one external hard drive.
Internet connection
Many restrictions on work refer to the use of the Internet. In general, they can be circumvented by redirecting all traffic to a server outside of company control. For example, use an anonymous proxy server through the FoxyProxy browser plug-in or similar. Changing the proxy address more often makes it harder to figure out its use. Activating the proxy server at home will increase the speed and security of the connection while gaining access to your LAN.
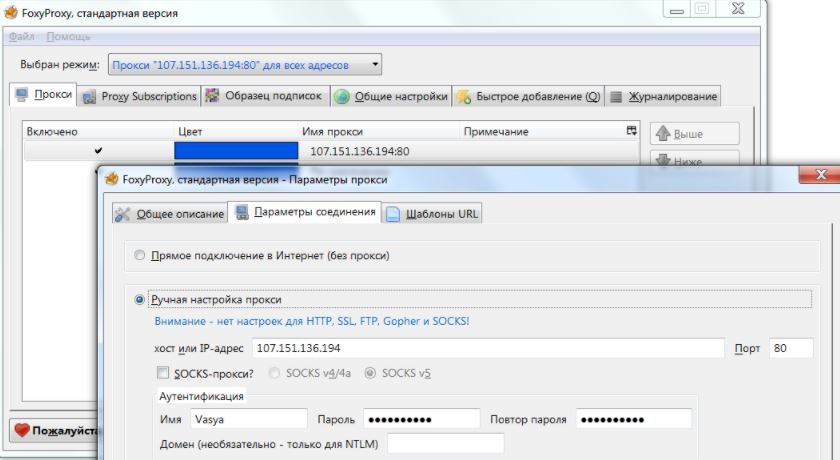
Sometimes the problem lies not so much in the prohibition of visiting certain sites as in the traffic quota. The easiest way to make an unlimited connection today is by using a smartphone. By connecting a favorable rate to the mobile Internet, you can distribute traffic over WiFi or use USB anchoring. A wired smartphone does not turn on in the air and raises less suspicion.
All methods described are of limited use due to the variety of configuration options. Step-by-step instructions quickly become obsolete, but the general principles remain the same for years to come.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











