A recent report mentions that the Web Application Firewall (WAF) developed by Cloudflare is vulnerable to rule bypass attacks. WAF-protected websites block attacks based on denial of service (DoS) or inter-site scritps (XSS) vulnerabilities, so this failure poses a significant risk.
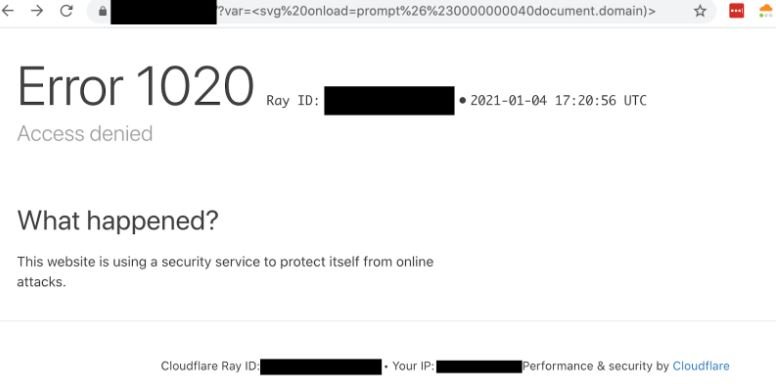
Jackson Henry, a cybersecurity researcher, shared a method for creating an SVG HTML tag to trigger a proof-of-concept (PoC) for an XSS failure on Cloudflare WAF-protected websites. Although the payload displayed in the PoC is equivalent to <svg onload s alert (“1”)>, adding some encoded characters makes the payload able to bypass the protection mechanisms.
The expert notes that this particular XSS attack method has been known publicly since at least June 4, 2019. These kinds of attacks seem to become more common every day; it is even possible to search the Internet for similar tactics.
Other flaws such as SQL injections, remote code execution, or deserialization errors could cause much greater damage. System administrators should remember that Cloudflare offers complementary protection measures, so a payload capable of dodging WAF does not guarantee the success of an attack; if the target website backend code has the right security measures, the attacker is unlikely to achieve its goals.
On this report, Henry mentioned to the cybersecurity community: “No organization should rely solely on tools like WAF to protect its systems; protection mechanisms against XSS, SQL and other attacks should be implemented in conjunction with the WAF of your choice.” Finally, the expert notes that setting highly restrictive configurations on the WAF could generate false positives, something undesirable for any organization’s operations.
On these reports, a Cloudflare representative mentioned: “We value any report of this nature, as they help us improve our capabilities; while these kinds of omissions are not considered vulnerabilities, knowing their behavior helps us block potential attacks.”

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











