A report published by cybersecurity researcher Ahmed Hassan mentions that the “People Nearby” feature, which allows Telegram users to see who is in nearby locations, could be abused by threat actors to triangulate the location of unsuspecting users.
While the feature is disabled by default, users who enable it ignore that, by doing so, they might reveal their location with a high degree of accuracy.
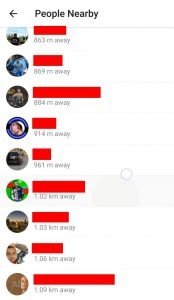
This feature lists Telegram users within a radius of approximately 2.5 kilometers. According to the Expert Advisor, it is possible to impersonate a user’s location by calculating the distance between three different points and accurately pointing out the location of the target user.
All malicious hackers need to fake a location is to walk in the given area, collect its latitude and longitude, and determine how far away the target user is.
Hassan also mentions that it is possible to complete the attack using a GPS forgery tool: “Any app available on the Play Store is functional for the attack; attackers should only install apps like GPS Spoof and create three locations close to the user within an 11-kilometre radius.”
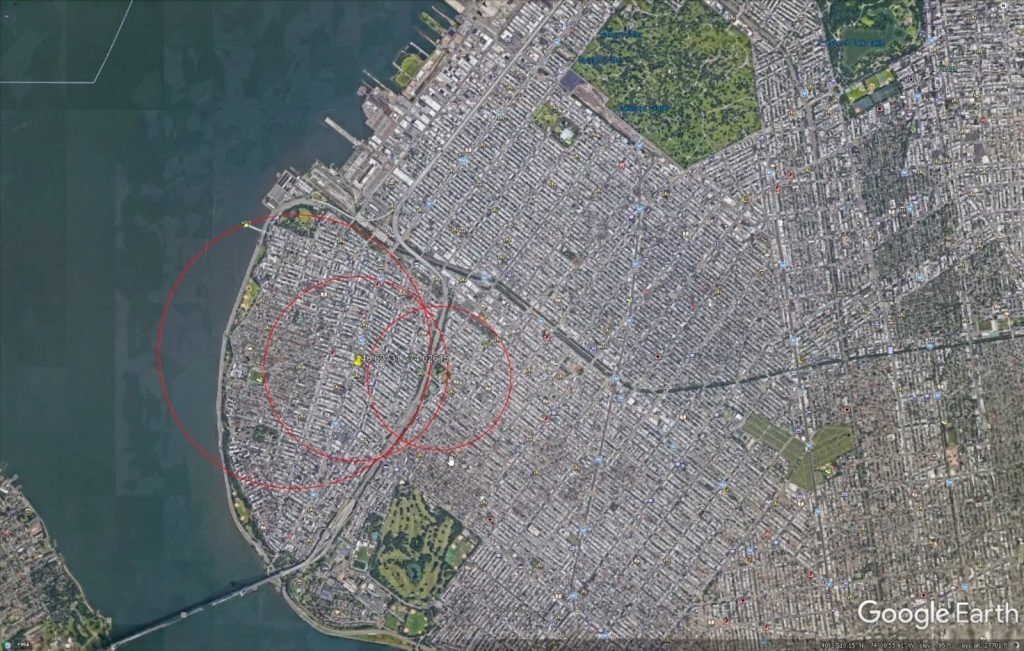
Using these three locations, threat actors could use tools like Google Earth Pro to connect counterfeit locations and calculate the midpoint between the three: “I successfully tested the attack with an app user,” the researcher says.
In this regard, Telegram mentions that this is not considered a security flaw, so the report was rejected: “The function is disabled by default; while it is possible to determine a user’s location under specific conditions, this report is not covered by our vulnerability bounty program.”
To prevent this from happening again, the company could round users’ locations to the nearest mile to avoid sending accurate locations. In addition, Hassan recommends adding random noise to the function in a similar way to what Tinder did when an identical issue was reported on the platform.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











