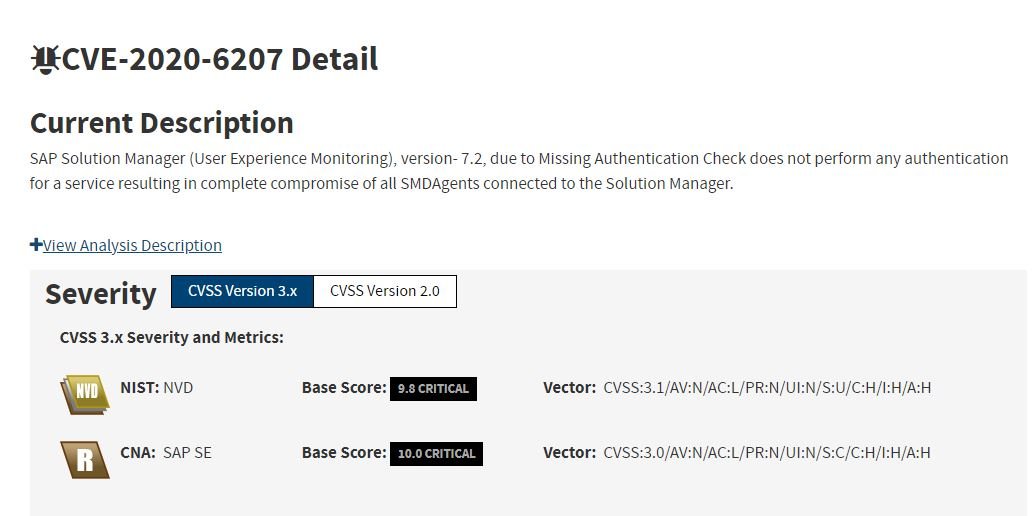
Information security specialists reported that a group of threat actors has released an exploit to abuse a critical security flaw in SAP enterprise software. This exploit is capable of compromising systems that do not yet receive the updates that fix CVE-2020-6207, a flaw in the authentication verification process in EEM Manager, a component of SAP Solution Manager (SolMan).
Although SAP fixed this flaw in March 2020, vulnerable systems still exist because its administrators have not installed the necessary updates. According to a report by Onapsis Research Labs, the exploit for this flaw was published a few days ago in a GitHub repository: “A successful attack would put SAP applications, business processes, and critical information from affected organizations at risk,” experts say.
About the vulnerable product, experts mention that SolMan is a management system used in all SAP environments in a similar way to solutions like Windows Active Directory: “Some companies don’t attach to SolMan’s security update policy, which plays in favor of malicious hackers,” the researchers add.
Researchers also warn that various groups of threat actors have performed massive scans on the Internet to detect SAP deployments vulnerable to this attack, so the problem must be taken into account with the necessary seriousness. Administrators should remember that installing updates completely fixes the flaw.
In this regard, an SAP spokesperson mentions: “Our security report on CVE-2020-6207 also includes steps to enable some workarounds, but the security patch is the main measure we recommend. SAP adds that with the release of the exploit an attack would be relatively simple and the consequences could be disastrous, so system administrators are invited to upgrade their installations as soon as possible.
Satnam Narang, Tenable’s specialist, says: “This recent report is a major challenge for the cybersecurity community; this non-authentication vulnerability means that threat actors could access vulnerable systems trivially, so it is critical that organizations rethink their system update policy to prevent these attacks from reaching unsuspected scales.”
For more information on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses, feel free to visit the International Cyber Security Institute (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











