Sudo maintainers announced a fix for a vulnerability that could have allowed local users to obtain root privileges on Unix-like systems without any authentication. Sudo is an UNIX program with which system administrators can provide root privileges to regular users on sudoers while keep track of activities.
This system works with the principle of minimum privilege, which gives users the necessary requirements to work without compromising system security. However, when running commands on Unix-like systems, users with least privileges can use the <<sudo>> command to run commands as the root user.
This command can also be configured to allow regular users to execute commands like any other user by including special policies in the sudoers configuration file.
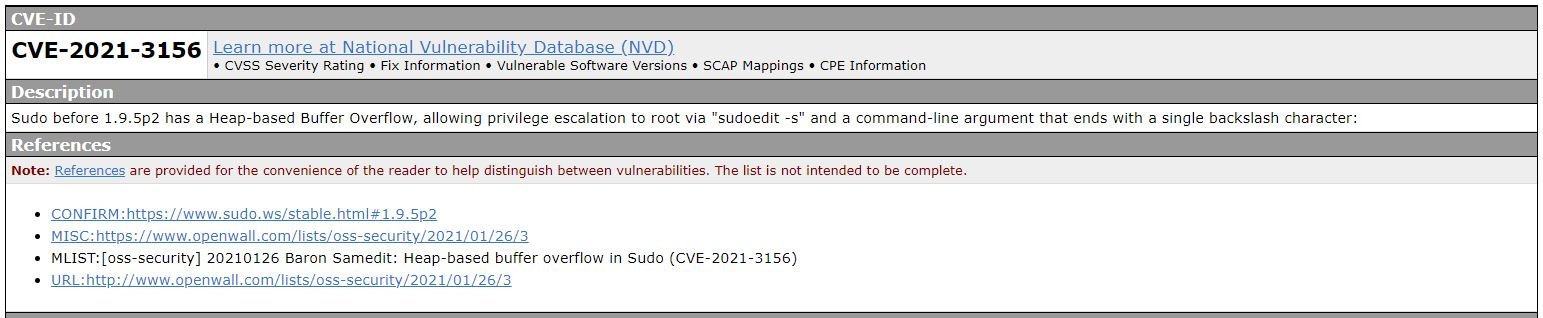
Tracked as CVE-2021-3156, this is a privilege escalation vulnerability initially reported by security firm Qualys in early 2021. According to their report, the problem exists from a heap-based buffer overflow that can be exploited by a local user without using administrator passwords.
“This buffer overflow is triggered when sudo incorrectly removes the diagonals invested in any argument,” the experts mention. The Qualys report also specifies that sudo usually escapes special characters when a command is executed through shell (sudo-s or sudo-i), however, it was also possible to run sudoedit with the -s or -i flags, in which case no escape had been made, making buffer overflow possible.
Researchers used three exploits for CVE-2021-3156 to demonstrate that a threat actor can successfully abuse this vulnerability. Using these exploits, researchers were able to obtain full root privileges on multiple Linux distributions, including Debian 10, Ubuntu 20.04, and Fedora 33.
The flaw would have been introduced with the Version of Sudo released in 2011, and is present in the default settings of all stable versions from 1.9.0 to 1.9.5p1, in addition to all legacy versions from 1.8.2 to 1.8.31p2. Sudo contributors have fixed the vulnerability in the sudo version 1.9.5p2 released today, while Qualys publicly revealed its findings.
To test whether your system is vulnerable, you must log in as a non-root user and run the “sudoedit -s /” command. Vulnerable systems will throw an error that starts with “sudoedit:” while patches will display an error that will start with “usage:”, mentioned the experts. For more information on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses, feel free to access the International Cyber Security Institute (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











