The maintainers of Vue.js, a popular JavaScript framework, announced the correction of a dangerous cross-site scripting vulnerability (XSS) in the Chrome browser extension, noting that they had to wait for the bug to be fully fixed before making any announcements about it. The vulnerability was discovered by cybersecurity specialist Jiantao Li from Singapore-based security firm Starlabs.
As you may remember, this is a very common type of vulnerability in web applications that would allow third parties to inject JavaScript code or in other similar language into web pages visited by a vulnerable user.
This framework has about one million users in the software development community, so an exploitation campaign could have been highly risky.
Although at first the researcher tried to privately notify Vue.js, after two weeks without receiving a response Jiantao Lin decided to try a more assertive approach and publish a vulnerability report and proof of concept (PoC) to a GitHub repository.
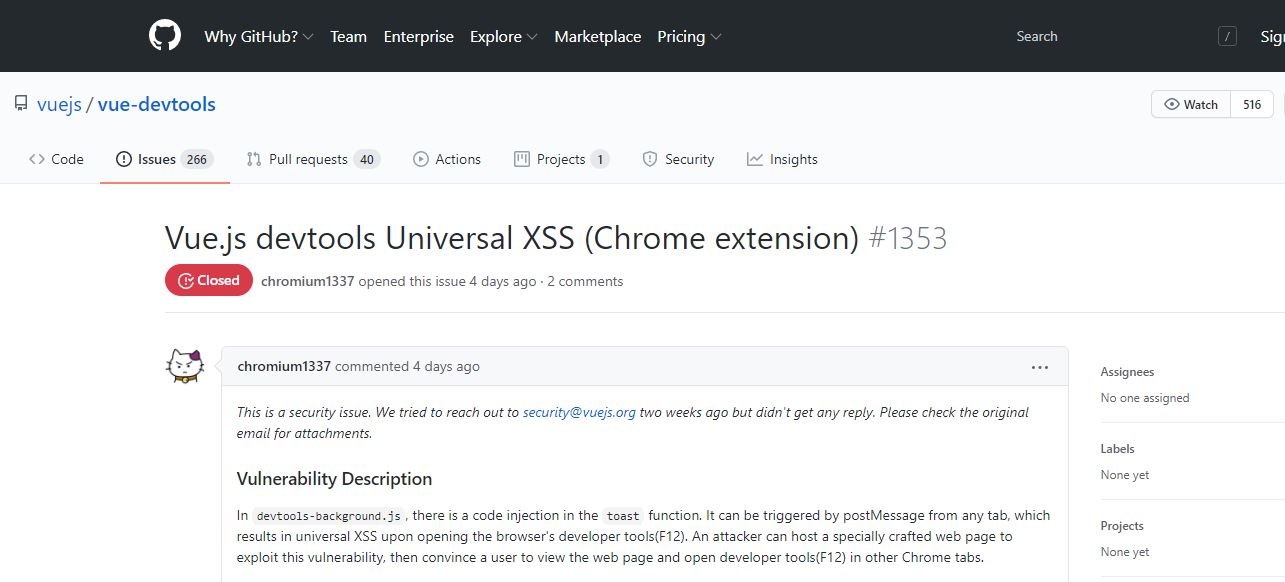
The researcher managed to get the attention of the cybersecurity community quickly, so just a few hours later the vulnerability had already been fixed.
The Starlabs report adds more details about the potential active exploitation of the vulnerability: “In devtools-background.js, there is an injection of code into the toast function; this condition could be triggered by postMessage from any tab, resulting in a universal XSS condition when opening browser development tools.” Apparently, a threat actor could host a website specially designed to exploit this vulnerability and subsequently trick the target user into entering that website and opening the development tools in other Chrome tabs.
In a simplified version of the report, Jiantao Lin mentioned: “This is a code injection flaw in a popular web browser extension; vulnerability exists because unverified data runs as code.” On the exploit process, the researcher adds: “The UXSS will allow malicious hackers to run JavaScript from one domain to any other domain if it is successfully exploited.”
Vue.js developers still need to respond to requests for information sent by various members of the cybersecurity community, so more details could be revealed during the next few days. For more information on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses, feel free to access the International Cyber Security Institute (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











