Security flaws could be detected on all kinds of technological devices, including on a coffee vending machine. A cybersecurity specialist has just revealed a way to compromise smart cards on older models of Nespresso coffee machines in order to get free and unlimited drinks. Polle Vanhoof, a Belgian security researcher, mentions that this hacking technique depends on modifying the values stored on smart cards.
“The process of decrypt the security keys and downloading the contents of these cards is feasible due to the security weaknesses inherent in their design and the technology with which they were manufactured,” Vanhoof says. These Mifare Classic cards are included in the first models of Nespresso machines.
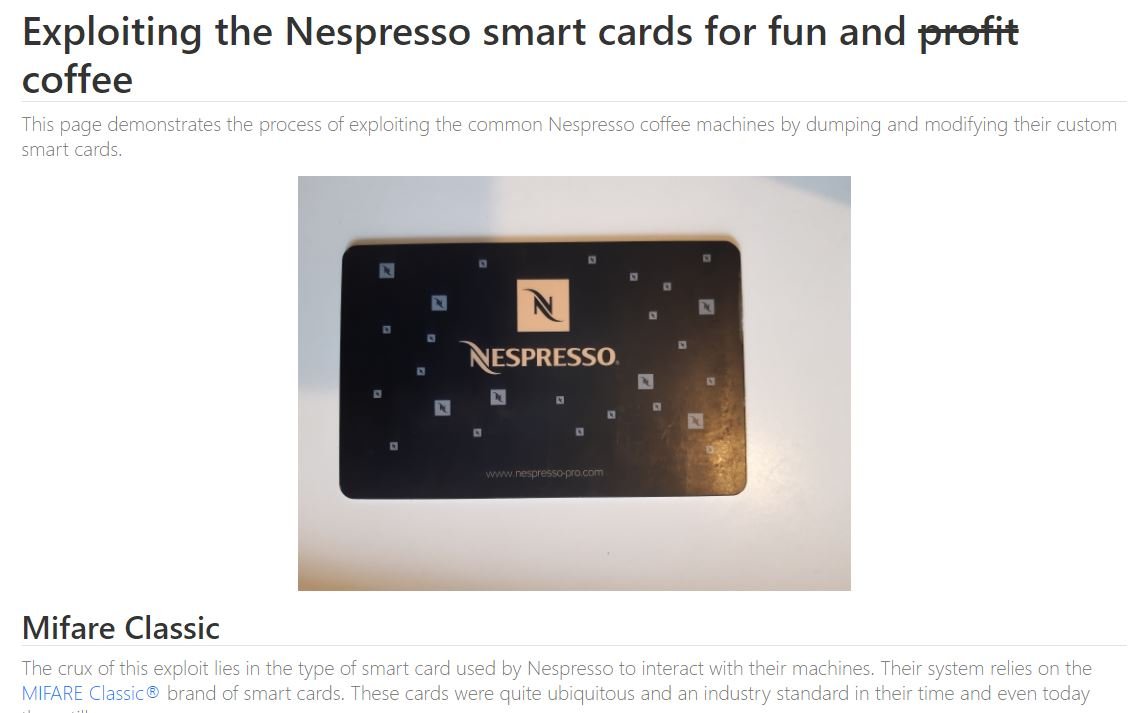
The flaws detected in this technology have been documented for more than a decade, although they had never been exploited to compromise a coffee machine; these flaws would allow threat actors to read and write arbitrary data, leading to the decryption of security keys. It should be mentioned that Mifare Classic cards were replaced by Mifare Plus technology, considered much safer.
“These flaws are especially harmful in Nespresso machines because coffee machines use this card to store the monetary value that users enter; that is, a threat actor can overwrite the stored value and enter an arbitrary amount, so the machine will believe that the amount of the coffee has been inserted,” the specialist adds.
Although a more developed system would completely block this attack through a monetary value check on the backend system, in the case of Nespresso this approach would only work if all smart cards had a network connection, something that seems unthinkable when it comes to such a device. This approach would also require providers of these coffee machines to provision a backend server to manage these searches.
The researcher presented his report to the company, which responded by mentioning that a backend feature was already offered, as well as an option for customers to upgrade to more secure hardware tokens. The report was presented in September, so Vanhoof only waited for the deadline set by the cybersecurity community to be met to publish their findings. To learn more about computer security risks, malware, vulnerabilities and information technologies, feel free to access the International Cyber Security Institute (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











