Cybersecurity specialists reported the detection of a new malware campaign specially designed to infect Mac devices, accumulating nearly 30,000 successful infections by the time now. This new variant, dubbed “Silver Sparrow”, was discovered in a joint investigation of Malwarebytes and Red Canary.
As mentioned above, researchers have detected 29,139 infected macOS endopoints across more than 150 countries, mainly in territories such as the United States, the United Kingdom, France and Germany. Due to the large number of infected systems, experts believe it is a serious security threat, not just a development test malware.
While thousands of cases have been detected in a short period of time, researchers still don’t know much about this variant of malware, its spreading methods and whether victims have anything in common: “Silver Sparrow may be deployed through malvertising campaigns, malicious apps or fake Flash updates,” experts mention , which also ignore the targets of hackers.
On the other hand, the researchers were able to detail how an attack develops; after this malware infects the target system it will remain dormant waiting for commands sent by hackers for the deployment of subsequent malicious actions: “We believe that this variant may be able to detect whether it is being analyzed while learning from researchers, which would eventually represent the inclusion of new capabilities.”
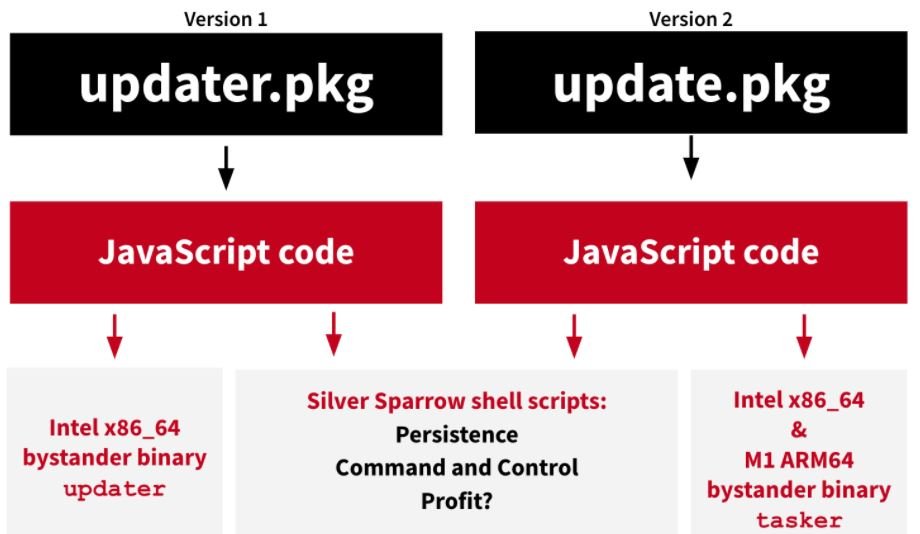
While thousands of cases have been detected in a short period of time, researchers still don’t know much about this variant of malware, its spreading methods and whether victims have anything in common: “Silver Sparrow may be deployed through malvertising campaigns, malicious apps or fake Flash updates,” experts mention , which also ignore the targets of hackers.
The researchers were able to detail how an attack develops; after this malware infects the target system it will remain dormant waiting for commands sent by hackers for the deployment of subsequent malicious actions: “We believe that this variant may be able to detect whether it is being analyzed while learning from researchers, which would eventually represent the inclusion of new capabilities.”
Specialists collected multiple data about this campaign, including compromise indicators such as malicious files, malware-created paths, and other details that may indicate an infection. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











