In recent times, threat actors have devised complex techniques for exploiting vulnerabilities in Docker containers and images, affecting even large companies such as Google, Facebook and Yahoo. While malicious hackers try to find more sophisticated attack methods, cybersecurity companies and independent researchers work on preventing these attacks, looking for ways to protect these resources from any potential risk.
The software unification process (DevOps) requires the establishment of functional image scanning and validation mechanisms, comprehensively protecting these processes. This time, web application security experts from the International Institute of Cyber Security (IICS) will show you the best methods to detect any potential vulnerability in your containers, as well as establish monitoring routines for added protection.
Up next we will briefly review the various options available to perform these security processes in Docker.
CLAIR

Clair is an open source project for exploiting vulnerabilities in Docker containers and applications. Web application security experts describe it as an API-driven analytics engine that checks layer by layer for container security flaws, and allows you to automatically monitor all containers for exploitable vulnerabilities by sending real-time notifications to the administrator.
It should be noted that this tool works with the information available in the National Vulnerability Database (NVD).
TRIVY
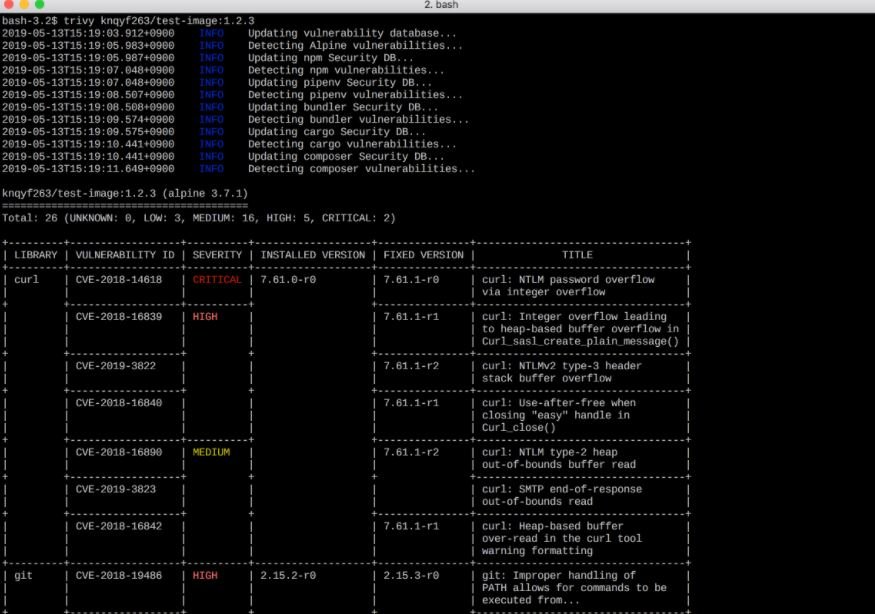
Trivy is an easy-to-use vulnerability scanner and great support for detecting packet failures across multiple operating systems and application dependencies.
Among Trivy’s main features are:
- Detection of complex vulnerabilities
- Simplicity
- Efficiency
- Compatible with Travis CI, CircleCI, Jenkins, GitLab CI, etc.
ANCHORE
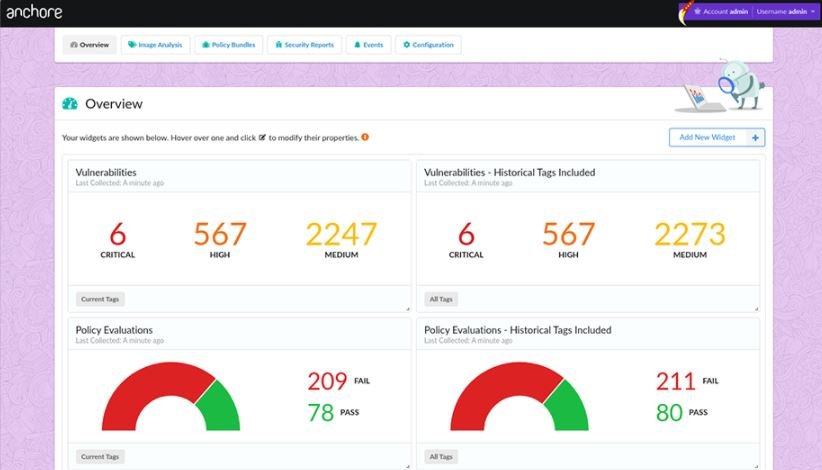
Anchore is an open source project for deep analysis of Docker images. It is also useful for image authentication, indicating whether it is secure or not.
According to web application security experts, Anchore can run on a stand-alone platform as well as on platforms such as Kubernetes, Rancher, Amazon ECS, Docker Swarm, and is available in Jenkins plugins for CI/CD scanning.
DAGDA
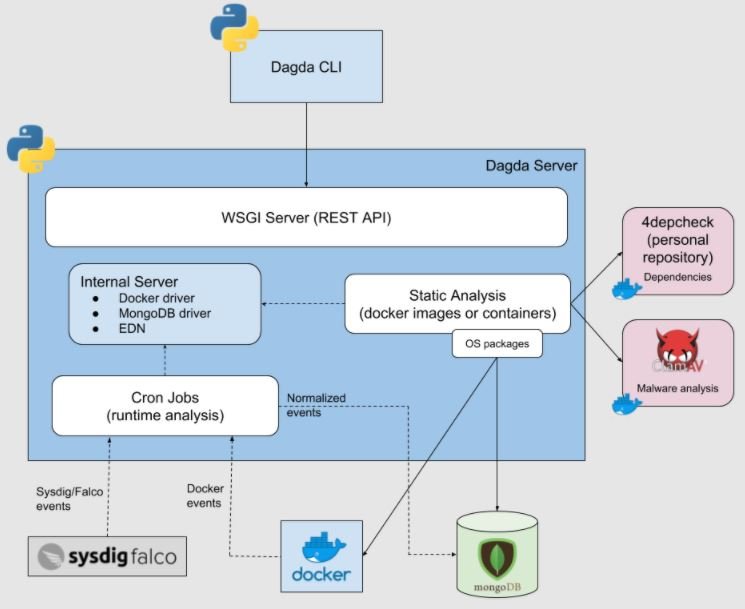
Dagda is an open source tool for static analysis of known vulnerabilities. The tool is highly functional in detecting security threats like Trojans and other malware variants. This tool is based on the ClamAV antivirus engine, which makes detection of security threats more efficient.
Dagda searches for information in sources such as Common Vulnerabilities and Exposures (CVE) and has advanced features such as:
- Support for multiple Linux images (CentOS, Ubuntu, OpenSUSE and Alpine)
- Dependency analysis in java, python node js, javascript, ruby, PHP
- MongoDB storage
FALCO
Falco is an open source project designed to operate as a threat detection engine in Kubernetes. Web application security specialists mention that this is a runtime security tool for detecting anomalous activity on hosts and containers running on Kubernetes, providing advanced security capabilities.
Falcon uses syntax such as tcpdump to create rules and uses libraries such as libscap and libinsp that can enter and get data from your Kubernetes API server or container runtime. This metadata can be used to obtain information about pods, tags, and namespaces to create specific rules for a specific namespace or container image.
AQUA SECURITY
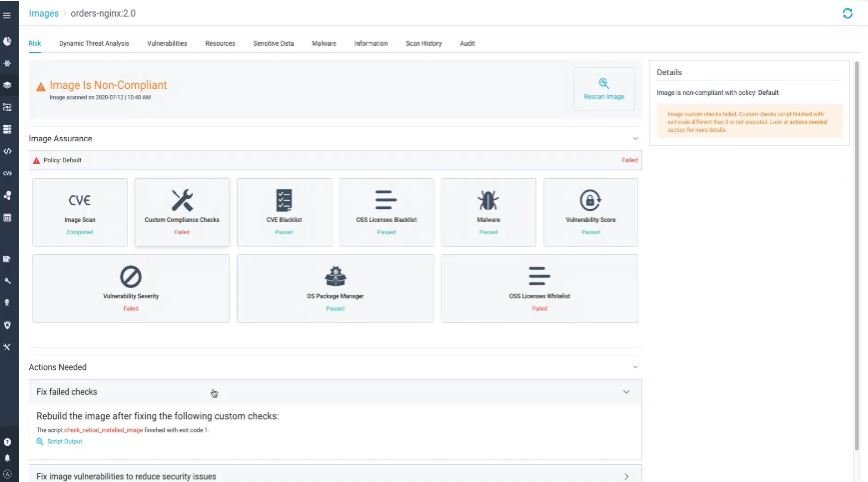
Aqua Security is a deployment designed to protect cloud-based applications, including containers. This tool provides researchers with superior vulnerability analysis and management for Kubernetes and other technologies. It is a comprehensive security platform that ensures containerized applications are protected and running in a secure environment.
When developers create images, they have a set of technologies and libraries to create them. Aqua Security allows them to scan these images to make sure they are clean.
DOCKER BENCH SECURITY
This is a script with multiple automated tests to validate container deployment best practices. To run the Docker Bench security system, you need Docker 1.13.0 or later.
The following is the command required to run this tool:
docker run -it --net host --pid host --userns host --cap-add audit_control \
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
-v /var/lib:/var/lib \
-v /var/run/docker.sock:/var/run/docker.sock \
-v /usr/lib/systemd:/usr/lib/systemd \
-v /etc:/etc --label docker_bench_security \
docker/docker-bench-security
After the user runs the script, they can verify all warning messages and make corrections.
HARBOR
Harbour is an open source cloud registry that provides role-based security and access control (RBAC) policies. Web application security experts mention that this tool stores, signs, and scans Docker images for vulnerabilities.
JFROG XRAY
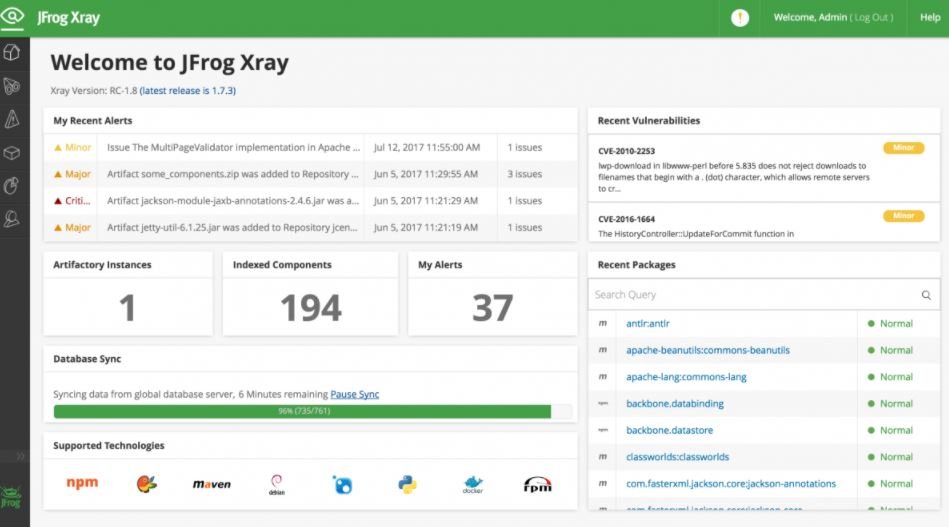
JFrog Xray is a security tool for container and image analysis. This solution allows you to continuously scan any dependencies for security vulnerabilities and licensing issues.
JFrog XRay proactively identifies security vulnerabilities that could affect our environment, and integrates natively with JFrog Artifactory.
QUALYS
Qualys is a tool used to discover, track and protect containerized environments in an automated manner, mentioning web application security experts.
This solution analyzes vulnerabilities within images or containers in the DevOps pipeline and deployments in on-premises or cloud environments, and provides a free version for users to make a decision about using these tools.
SCANNING IN DOCKER
The beta version of Docker Scan uses the Synk engine and is capable of scanning the local Dockerfile, images, and their dependencies for known vulnerabilities. You can run Docker scanning with the following command:
docker scan mydockerimage
CONCLUSION
Scanning vulnerabilities in Docker containers and images is a practice that certainly strengthens web application ssecurity, establishing the necessary mechanisms for preventing cyberattacks that could have disastrous consequences. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











