Trend Micro’s recent threat hunting efforts have uncovered active exploitation of CVE-2023-36025, a vulnerability in Microsoft Windows Defender SmartScreen, by a new strain of malware known as Phemedrone Stealer. This malware targets web browsers, cryptocurrency wallets, and messaging apps like Telegram, Steam, and Discord, stealing data and sending it to attackers via Telegram or command-and-control servers. Phemedrone Stealer, an open-source stealer written in C#, is actively maintained on GitHub and Telegram.
CVE-2023-36025 arises from insufficient checks on Internet Shortcut (.url) files, allowing attackers to bypass Windows Defender SmartScreen warnings by using crafted .url files that download and execute malicious scripts . Microsoft patched this vulnerability on November 14, 2023, but its exploitation in the wild led to its inclusion in the Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities list. Various malware campaigns, including those distributing Phemedrone Stealer, have since incorporated this vulnerability.
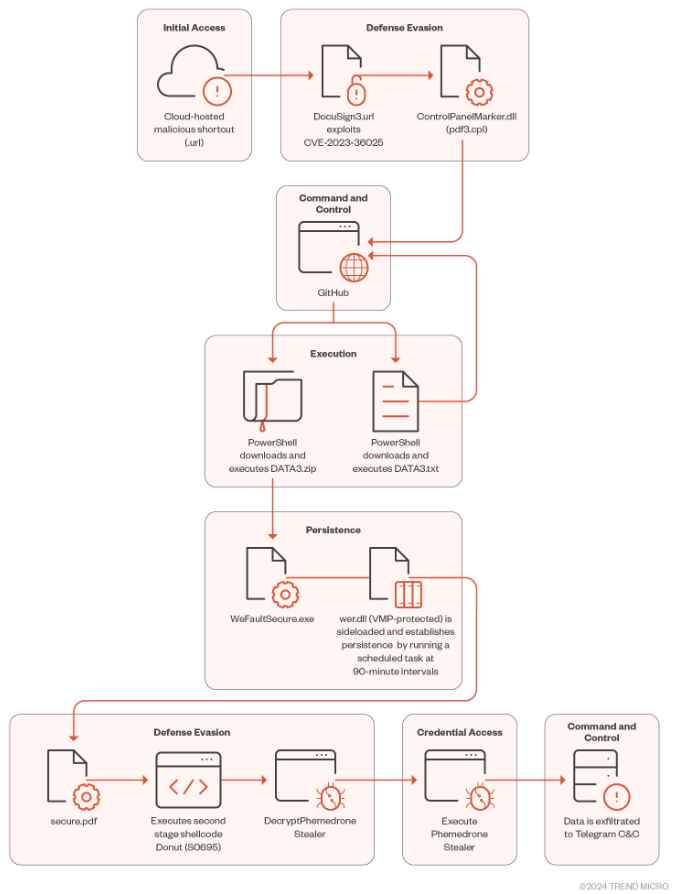
Initial Access via Cloud-Hosted Malicious URLs
As per the report, this involves leveraging cloud-hosted URLs that are malicious in nature. The article provides insights into how these URLs are used to initiate the attack, highlighting the strategies employed for distributing the malware and penetrating target systems. Attackers host malicious Internet Shortcut files on platforms like Discord or cloud services, often disguised using URL shorteners. Unsuspecting users who open these files trigger the exploitation of CVE-2023-36025.
Defense Evasion Tactics
The malicious .url file downloads and executes a control panel item (.cpl) file from an attacker-controlled server. This bypasses the usual security prompt from Windows Defender SmartScreen. The malware employs MITRE ATT&CK technique T1218.002, using the Windows Control Panel process binary to execute .cpl files, which are essentially DLL files.
- Initial Infection via Malicious .url File (CVE-2023-36025): The attack begins when a user executes a malicious Internet Shortcut (.url) file. This file is designed to bypass Microsoft Windows Defender SmartScreen warnings, typically triggered for files from untrusted sources. The evasion is likely achieved by manipulating the file’s structure or content, making it appear benign.
- Execution of a Control Panel Item (.cpl) File: Once executed, the .url file connects to an attacker-controlled server to download a .cpl file. In Windows, .cpl files are used to execute Control Panel items and are essentially Dynamic Link Libraries (DLLs). This step involves the MITRE ATT&CK technique T1218.002, which exploits the Windows Control Panel process binary (
control.exe) to execute .cpl files. - Use of rundll32.exe for DLL Execution: The .cpl file, when executed through
control.exe, then callsrundll32.exe, a legitimate Windows utility used to run functions stored in DLL files. This step is critical as it uses a trusted Windows process to execute the malicious DLL, further evading detection. - PowerShell Utilization for Payload Download and Execution: The malicious DLL acts as a loader to call Windows PowerShell, a task automation framework. PowerShell is then used to download and execute the next stage of the attack from GitHub.
- Execution of DATA3.txt PowerShell Loader: The file
DATA3.txt, hosted on GitHub, is an obfuscated PowerShell script designed to be difficult to analyze statically (i.e., without executing it). It uses string and digit manipulation to mask its true intent. - Deobfuscation and Execution of the GitHub-Hosted Loader: Through a combination of static and dynamic analysis, the obfuscated PowerShell commands within
DATA3.txtcan be deobfuscated. This script is responsible for downloading a ZIP file from the same GitHub repository. - Contents of the Downloaded ZIP File:
- WerFaultSecure.exe: A legitimate Windows Fault Reporting binary.
- Wer.dll: A malicious binary that is sideloaded (executed in the context of a legitimate process) when
WerFaultSecure.exeis run. - Secure.pdf: An RC4-encrypted second-stage loader, presumably containing further malicious code.
This attack is sophisticated, using multiple layers of evasion and leveraging legitimate Windows processes and binaries to conceal malicious activities. The use of GitHub as a hosting platform for malicious payloads is also noteworthy, as it can lend an appearance of legitimacy and may bypass some network-based security controls.
Persistence and DLL Sideloading
The malware achieves persistence by creating scheduled tasks and uses DLL sideloading techniques. The malicious DLL, crucial for the loader’s functionality, decrypts and runs the second stage loader. It uses dynamic API resolving and XOR-based algorithms for string decryption, complicating reverse engineering efforts.
- Malicious DLL (wer.dll) Functionality: It decrypts and runs a second-stage loader. To avoid detection and hinder reverse engineering, it employs API hashing, string encryption, and is protected by VMProtect.
- DLL Sideloading Technique: The malware deceives the system into loading the malicious wer.dll by placing it in the application directory, a method that exploits the trust Windows has in its own directories.
- Dynamic API Resolving: To avoid detection by static analysis tools, the malware uses CRC-32 hashing for storing API names, importing them dynamically during runtime.
- XOR-based String Decryption: An algorithm is used to decrypt strings, with each byte’s key generated based on its position. This method is designed to complicate automated decryption efforts.
- Persistence Mechanism: The malware creates a scheduled task to regularly execute WerFaultSecure.exe. This ensures that the malware remains active on the infected system.
- Second-Stage Loader (secure.pdf): It’s decrypted using an undocumented function from advapi32.dll, with memory allocation and modification handled by functions from Activeds.dll and VirtualProtect.
- Execution Redirection through API Callbacks: The malware cleverly redirects execution flow to the second-stage payload using Windows API callback functions, particularly exploiting the CryptCATCDFOpen function.
Overall, this malware demonstrates a deep understanding of Windows internals, using them to its advantage to stay hidden and maintain persistence on the infected system. The combination of techniques used makes it a complex and dangerous threat.
Second-Stage Defense Evasion
The second-stage loader, known as Donut, is an open-source shellcode that executes various file types in memory. It encrypts payloads without compression and uses the Unmanaged CLR Hosting API to load the Common Language Runtime, creating a new Application Domain for running assemblies.Here’s an overview of how Donut is used for defense evasion and payload execution:
- Donut Shellcode Loader:
- Capabilities: Allows execution of VBScript, JScript, EXE files, DLL files, and .NET assemblies directly in memory.
- Deployment Options: Can be embedded into the loader or staged from an HTTP or DNS server. In this case, it’s embedded directly into the loader.
- Payload Compression and Encryption:
- Compression Techniques: Supports aPLib, LZNT1, Xpress, and Xpress Huffman through RtlCompressBuffer.
- Encryption: Uses the Chaskey block cipher for payload encryption. In this instance, only encryption is used, without compression.
- Execution Process via Unmanaged CLR Hosting API:
- CLR Loading: Donut configures to use the Unmanaged CLR Hosting API to load the Common Language Runtime (CLR) into the host process.
- Application Domain Creation: Creates a new Application Domain, allowing assemblies to run in disposable AppDomains.
- Assembly Loading and Execution: Once the AppDomain is prepared, Donut loads the .NET assembly and invokes the payload’s entry point.
The use of Donut in this attack is particularly notable for its ability to execute various types of code directly in memory. This method greatly reduces the attack’s visibility to traditional security measures, as it leaves minimal traces on the filesystem. Additionally, the use of memory-only execution tactics, coupled with sophisticated encryption, makes the payload difficult to detect and analyze. The ability to create and use disposable AppDomains further enhances evasion by isolating the execution environment, reducing the chances of detection by runtime monitoring tools. This approach demonstrates a high level of sophistication in evading defenses and executing the final payload stealthily.
Phemedrone Stealer Payload Analysis
Phemedrone Stealer initializes its configuration and decrypts items like Telegram API tokens using the RijndaelManaged symmetric encryption algorithm. It targets a wide range of applications to extract sensitive information, including Chromium-based browsers, crypto wallets, Discord, FileGrabber, FileZilla, Gecko-based browsers, system information, Steam, and Telegram.
Command and Control for Data Exfiltration
After data collection, the malware compresses the information into a ZIP file and validates the Telegram API token before exfiltrating the data. It sends system information and statistics to the attacker via the Telegram API. Despite the patch for CVE-2023-36025, threat actors continue to exploit this vulnerability to evade Windows Defender SmartScreen protection. The Phemedrone Stealer campaign highlights the need for vigilance and updated security measures against such evolving cyber threats.
Mitigation
Mitigating the risks associated with CVE-2023-36025 and similar vulnerabilities, especially in the context of the Phemedrone Stealer campaign, involves a multi-layered approach. Here are some key strategies:
- Apply Security Patches: Ensure that all systems are updated with the latest security patches from Microsoft, particularly the one addressing CVE-2023-36025. Regularly updating software can prevent attackers from exploiting known vulnerabilities.
- Enhance Endpoint Protection: Utilize advanced endpoint protection solutions that can detect and block sophisticated malware like Phemedrone Stealer. These solutions should include behavior-based detection to identify malicious activities.
- Educate Users: Conduct security awareness training for all users. Educate them about the dangers of clicking on unknown links, opening suspicious email attachments, and the risks of downloading files from untrusted sources.
- Implement Network Security Measures: Use firewalls, intrusion detection systems, and intrusion prevention systems to monitor and control network traffic based on an applied set of security rules.
- Secure Email Gateways: Deploy email security solutions that can scan and filter out malicious emails, which are often the starting point for malware infections.
- Regular Backups: Regularly back up data and ensure that backup copies are stored securely. In case of a malware infection, having up-to-date backups can prevent data loss.
- Use Application Whitelisting: Control which applications are allowed to run on your network. This can prevent unauthorized applications, including malware, from executing.
- Monitor and Analyze Logs: Regularly review system and application logs for unusual activities that might indicate a breach or an attempt to exploit vulnerabilities.
- Restrict User Privileges: Apply the principle of least privilege by limiting user access rights to only those necessary for their job functions. This can reduce the impact of a successful attack.
- Incident Response Plan: Have a well-defined incident response plan in place. This should include procedures for responding to a security breach and mitigating its impact.
- Use Secure Web Gateways: Deploy web gateways that can detect and block access to malicious websites, thereby preventing the download of harmful content.
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and address potential security gaps in the network.
By implementing these measures, organizations can significantly reduce their risk of falling victim to malware campaigns that exploit vulnerabilities like CVE-2023-36025.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











