A cybercriminal group is deploying a phishing campaign that uses a fraudulent website to collect Microsoft Office 365 credentials by creating html snippets stored locally and remotely. This method involves integrating various hidden HTML pieces into JavaScript files to get the fake login interface in which the victim delivers their sensitive information.
Potential victims receive an attachment disguised as an Excel document that is actually an HTML document with a URL-encoded piece of text. A report prepared by Trustwave researchers notes that decoding this text makes it possible to find more coded content.
A subsequent analysis noted the presence of a couple of links redirecting to two JavaScript files hosted on “yourjavascript.com”, which has recently been associated with other phishing campaigns.
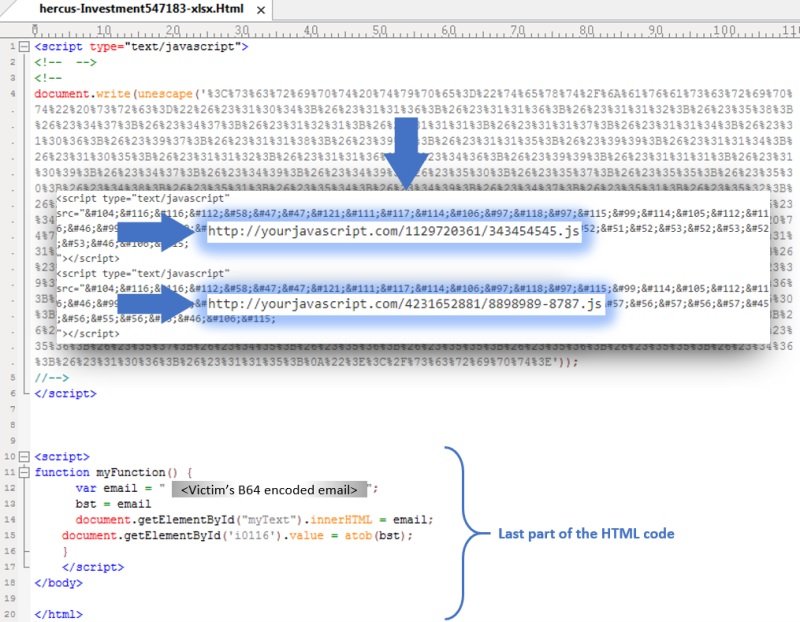
These JavaScript files contained two blocks of encoded text to hide HTML code, URL, and Base64 encoding. One of these files contains a section of the phishing website and the code to validate the victim’s email address and password. On the other hand, the second JavaScript file contains the “send” function, located through the form and the code to trigger a pop-up message informing victims that their connection had failed and they had to authenticate again.
Trustwave experts decoded nearly 400 lines of HTML code, grouped into five snippets in the two JavaScript files and one in the attachment sent to the victim, resulting in the Office 365 phishing website as if they were the pieces of a puzzle.
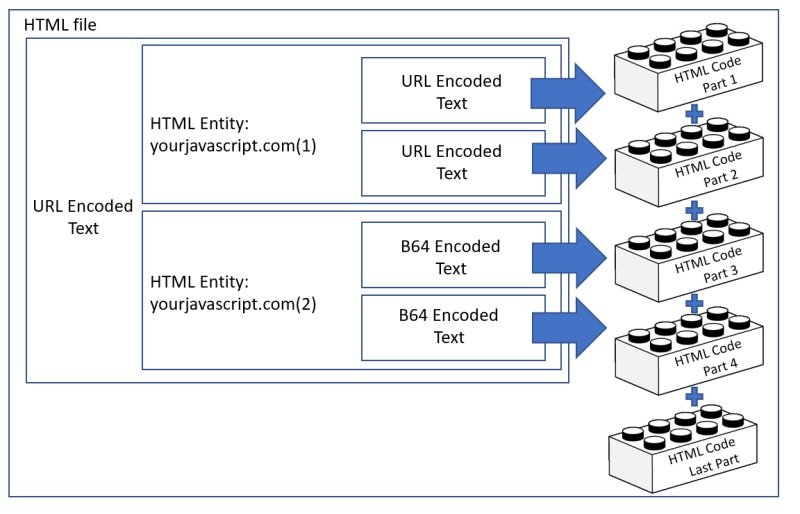
Specialists mention that the strangest thing about this campaign is that malicious code is downloaded in hidden fragments from a remote location and then assembled to a local location: “This allows threat actors to bypass protection mechanisms like Secure Email Gateways.”
Finally, Trustwave mentions that the URL that receives the stolen credentials in this campaign remains active, so office 365 account administrators need to stay on top of these security risks, ignoring any email sent by unknown users and trying not to visit potentially malicious websites.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











