Experts report that the newly reported IP address validation vulnerability also impacts the IP address of the standard Python library. The flaw, tracked as CVE2021-29921, resides in the Python 3.x ipaddress module and exists due to a change made a couple of years ago by project maintainers.
A couple of months ago, reports were filed on a critical IP validation vulnerability in the network mask library used by thousands of applications. Tracked as CVE-2021-28918, this flaw exists in the npm and Perl versions of the network mask and other similar libraries.
The most recent report indicates that the ipaddress standard library introduced in Python 3.3 is also affected by this failure. According to the researchers responsible for the finding, the vulnerability exists due to incorrect ip address analysis by the affected library. As some will already know, the ipaddress module provides Python developers with various functions to easily create IP addresses, networks, and interfaces.
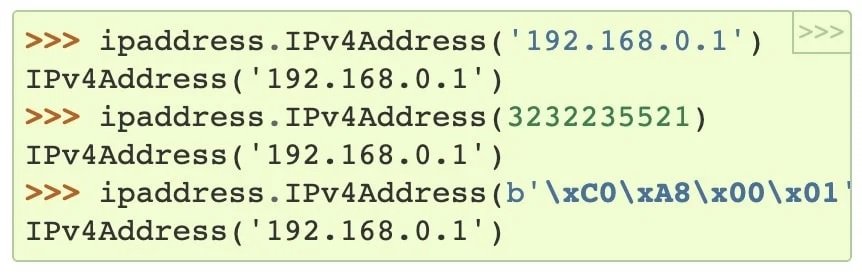
The IPv4 address can be presented in multiple formats (integers, decimals, hexadecimal, or octals), although it is usually presented in decimal format. Suppose you receive an IP address in decimal format, 127.0.0.1, which is widely understood as the local or localhost loopback address.
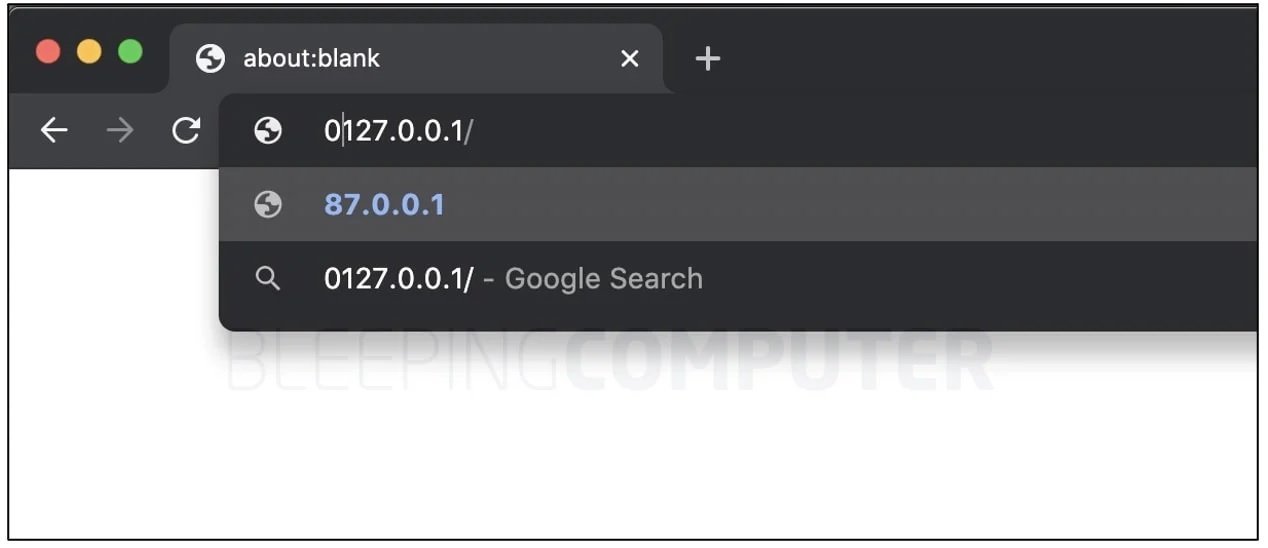
If you had to prefix a 0, should an application analyze it as 0127.0.0.1 or as 127.0.0.1? By analyzing the BleepingComputer platform website, you can type 0127.0.0.1 in the Chrome address bar, which the browser will try to complete as an IP address in octal format. Pressing Enter changes the IP to its decimal equivalent (87.0.0.1), which is how most applications assume to handle this type of IP address.
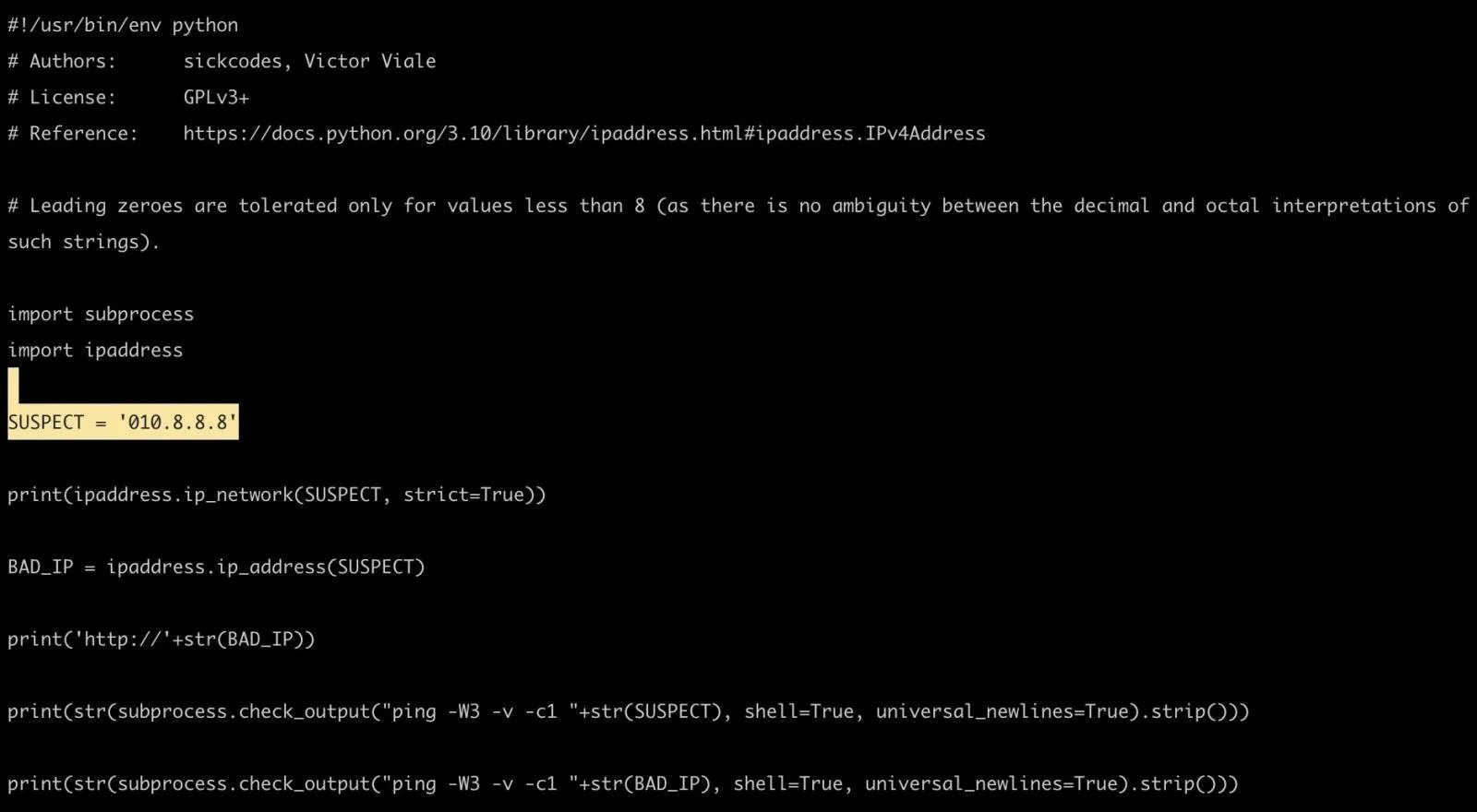
According to the original specification, for ambiguous IP addresses, parts of an IPv4 address can be interpreted as octal if they have the prefix “0”; however, in the case of the IP address of the standard Python library, the leading zeros will simply be removed. A proof of concept shows that the Python IP address library would simply discard the zeros at startup. To put it another way, when parsed using the Python ipaddress module, ‘010.8.8.8’ would be treated as ’10 .8.8.8′, instead of ‘8.8.8.8’.
“Incorrect input validation of octal strings in Python 3.8.0 to v3.10 stdlib ipaddress allows threat actors to perform Man-in-The-Middle (MiTM) attacks, request forgery, among other attack variants,” the investigation notes.
Although the ipaddress module was introduced in Python 3.3, this regression error was introduced in the module from Python version 3.8.0 through 3.10. Multiple options for temporary risk mitigation have been published on the project’s official platforms. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











