A group of researchers has produced a report in reference to the most popular tactics employed by hacking groups to evade the Antimalware Scan Interface (AMSI) security tool. Developed by Microsoft, this is an interface designed for the integration of anti-malware products into Windows systems, increasing protection for users.
AMSI’s integration with Office 365 was recently updated to include Excel 4.0 macro scanning to try to prevent malicious macros from entering as an infection vector.
This report was prepared by a research team from the security firm Sophos, mentioning that hackers resort to virtually any known method to disable AMSI, including obfuscation attacks, steganography and the uploading of malicious files.
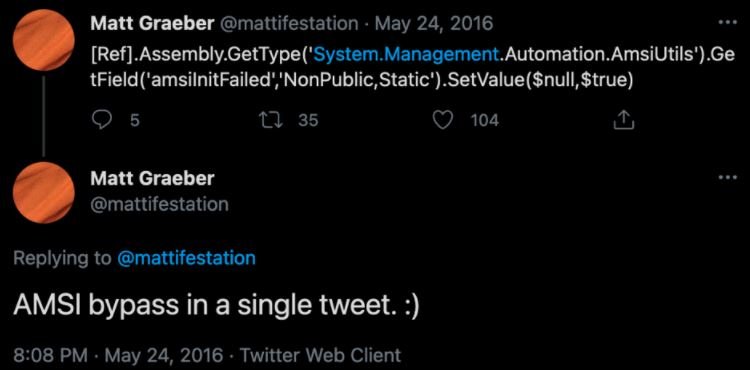
A few years ago Sophos’ researchers revealed a line of code capable of reversing a PowerShell attribute for AMSI integration that could have interrupted some processes of this interface. This script has already been identified as malicious, although it is the starting point for the development of some methods to bypass AMSI in the most recent implementations.
Most of the attack methods detected in the last two years appear to be focused on post-exploit activities, including lateral movement. One of the main methods is based on trying to retrieve a PowerShell backdoor from a web server within a private IP address space. This same method is based on a separate incident related to the Proxy Logon attack connecting to a remote server.
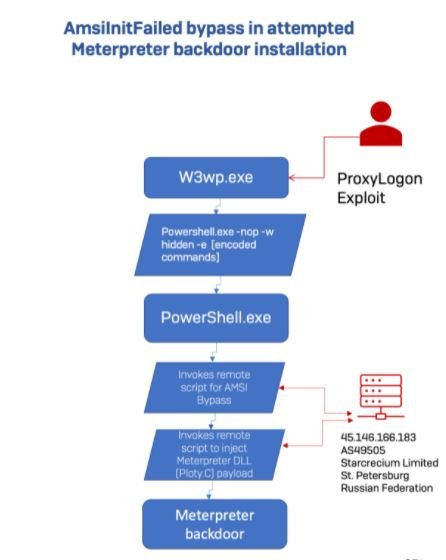
Another technique of growing popularity is the use of an offensive tool known as Seabelt, which consists of a PowerShell script for creating a delegated process that uses reflection to access the .NET interface for AmsiUtils.
Sophos experts mention that nearly 99% of these attacks are carried out by manipulating the AMSI library. It should be noted that there are multiple malware variants capable of finding AmsiScanBuffer to overwrite instructions and force a severe failure in AMSI scan requests.
Other tactics include using Cobalt Strike, remote command-line scripts in PowerShell before the release of updates, and creating fake DLLs designed to trick PowerShell into loading a fake version of amsi. dll.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











