A Microsoft security team has been closely monitored a cybercriminal group identified as BazarCall, dedicated to the deployment of tech support scams using call centers for the distribution of a dangerous malware variant. This group has been active since the beginning of 2021 and has already infected thousands of Windows devices.
In this regard, Palo Alto Networks researcher Brad Duncan mentioned that this malware variant allows threat actors to install a backdoor on compromised Windows devices: “After a user becomes infected, cybercriminals employ backdoor access to deliver malware, scan the environment, and exploit other vulnerable hosts on the network.”
Attacks begin by sending phishing emails to random users; these messages misled the victim by mentioning that a supposed trial subscription for Office 365 has expired and a monthly fee will be charged unless the user cancels via phone call. Via Twitter, Microsoft’s security team revealed one of the emails received by one of the potential victims.
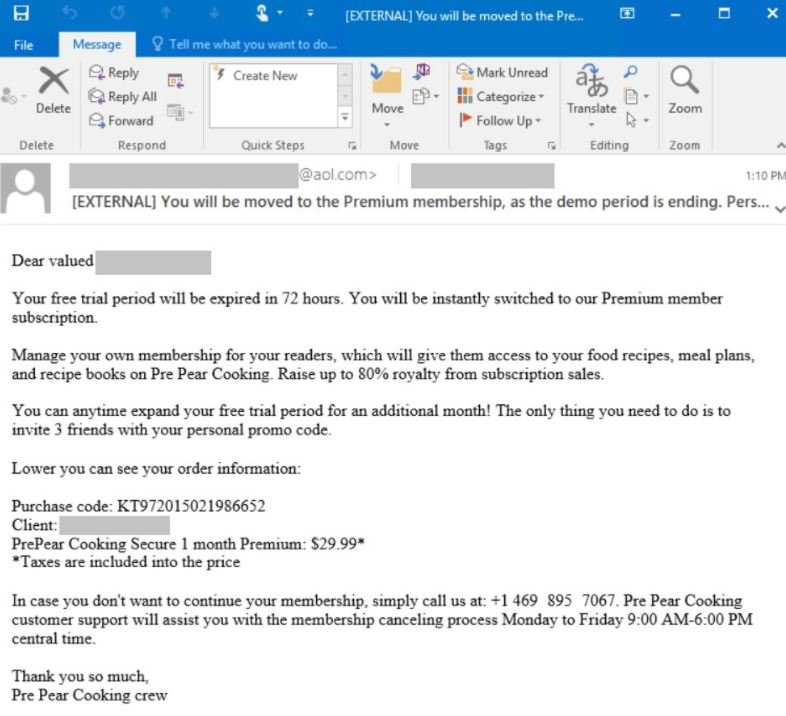
If users fall into the trap and call the phone number included in the message, the call will be directed to a call center operated by cybercriminals, who will trick the user into opening a fraudulent website and downloading an Excel file with a malicious macro to download the malware payload.
Microsoft researchers also detected that these hackers use the Cobalt Strike malicious kit to intercept sensitive information, including databases in Active Directory (AD). As many users will recall, Cobalt Strike is employed in lateral movement attacks after an initial engagement. On the other hand, AD theft has become one of the biggest problems for companies around the world, as it contains the credentials of an organization.
Microsoft created a GitHub repository to share some details about the BazarCall campaign, though the investigation is still active. The company promised to update the repository with new information as it is confirmed.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











