The security teams of the technology firm Palo Alto Networks announced the correction of a set of vulnerabilities in Prisma Cloud Compute, a solution for the protection of workloads in the cloud. The patches also address a flaw in the Windows agent for the Cortex XDR detection and response platform.
According to the report, the most severe flaw is a local privilege escalation error in Cortex XDR that received a score of 7.8/10 according to the Common Vulnerability Scoring System (CVSS). This flaw was tracked as CVE-2021-3042. Apparently, authenticated local threat actors could abuse this flaw to gain file creation privileges on the root directory.
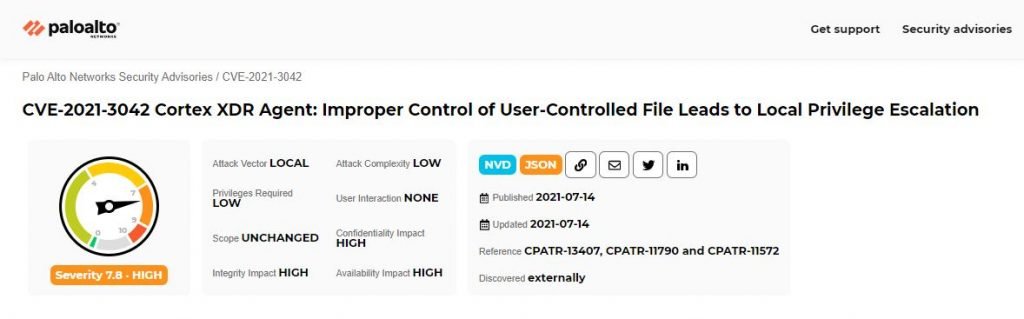
This flaw resides in all versions of the Cortex XDR agent that did not receive content update 181 or later. To mitigate the risk of exploitation, Palo Alto recommends that you prevent users from creating files in the vulnerable directory.
Moreover, the report describes the detection of CVE-2021-3043, a cross-site scripting (XSS) flaw that resides in the Prisma web console. The flaw received a CVSS score of 7.5/10. A remote hacker could abuse this flaw to execute arbitrary JavaScript code in the web console of the affected product. It should be noted that this flaw can only be exploited as long as a legitimate administrator uses the web interface.
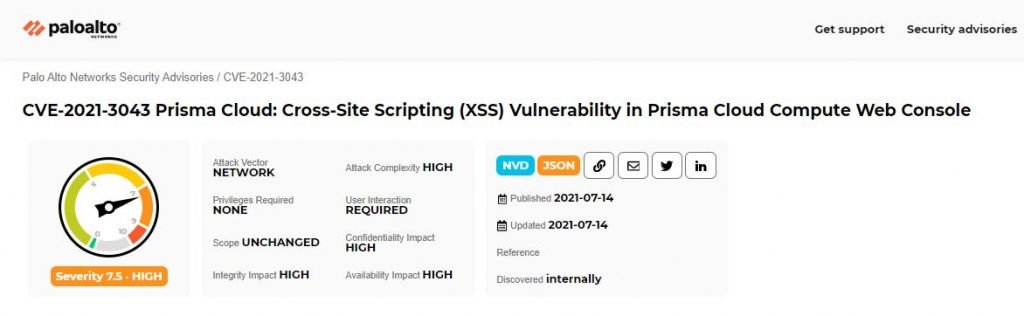
This flaw resides in Prisma versions 20.12 and 21.04. Updates will be applied automatically along with the Prisma Cloud Compute SaaS installation.
The company concluded its security alert by mentioning that so far no attempts at active exploitation of these flaws have been detected.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











