Cybersecurity specialists report the detection of a new Android-based remote access Trojan (RAT) that is capable of recording the screen of the affected user in order to steal sensitive information such as online banking credentials and other access keys to perform fraudulent activities.
This malware was identified as Vultur and was distributed through the official platform Google Play Store hidden in an app called Protection Guard, which was downloaded more than 5 thousand times.
In its report, the security firm ThreatFabric notes: “This malicious development is capable of recording the user’s screen and recording keystrokes, applying a complex strategy for the collection of login credentials in an automated manner.”
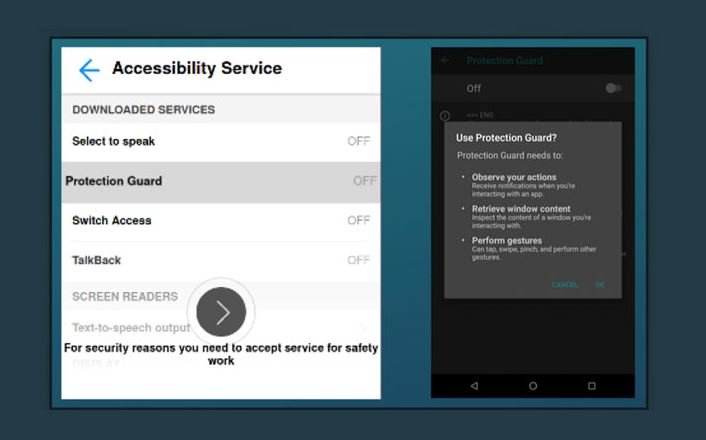
While other variants of banking malware such as MysteryBot, Grandoreiro or Vizom employ the well-known overlay technique to create fake websites and trick users, Vultur employs a technique that might seem more aggressive but has proved equally effective, as a demonstration that malicious hackers are increasingly developing better attack techniques.
This is not the only security risk of its kind. This week security firm Cleafy reported the discovery of UBEL, a variant of the Oscorp malware capable of interacting with a compromised Android system in real time. Experts mention that Vultur is able to interact with the affected devices in real time in a similar way, which makes the attack very difficult to detect.
Experts also mention that Vultur may be related to a dangerous malware known as Brunhilda, a dropper capable of abusing the Play Store for the distribution of other malicious developments. If the relationship between the two malware variants is confirmed, researchers believe that more hacking incidents related to this group could arrive in the future.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











