One of the main variants of attack against Windows systems is the abuse of Active Directory using tools for credential theft such as Mimikatz. According to network security specialists, the use of Mimikatz and other similar tools allows threat actors to extract passwords stored in memory from the Local Security Subsystem Service (LSSAS. EXE), so it is considered a severe security threat.
This time, network security experts from the International Institute of Cyber Security (IICS) will show you the best methods to protect against password theft using Mimikatz, allowing you to consolidate a complete cybersecurity environment.
As usual, we remind you that this article was prepared for informational purposes only, so this should not be considered as a call to action. IICS is not responsible for the misuse that may occur to the information contained herein.
Method 1: Avoid the debugging possibilities
Debugging mode is enabled by default on Windows systems and is granted to the local Administrators group (BUILTIN\Administrators). According to network security experts, almost 99% of administrators do not use this feature, so it is better to disable it before threat actors try to exploit it.
To do this, go to Group Policy (local or domain) and go to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment and enable the Debugging Program Policy.
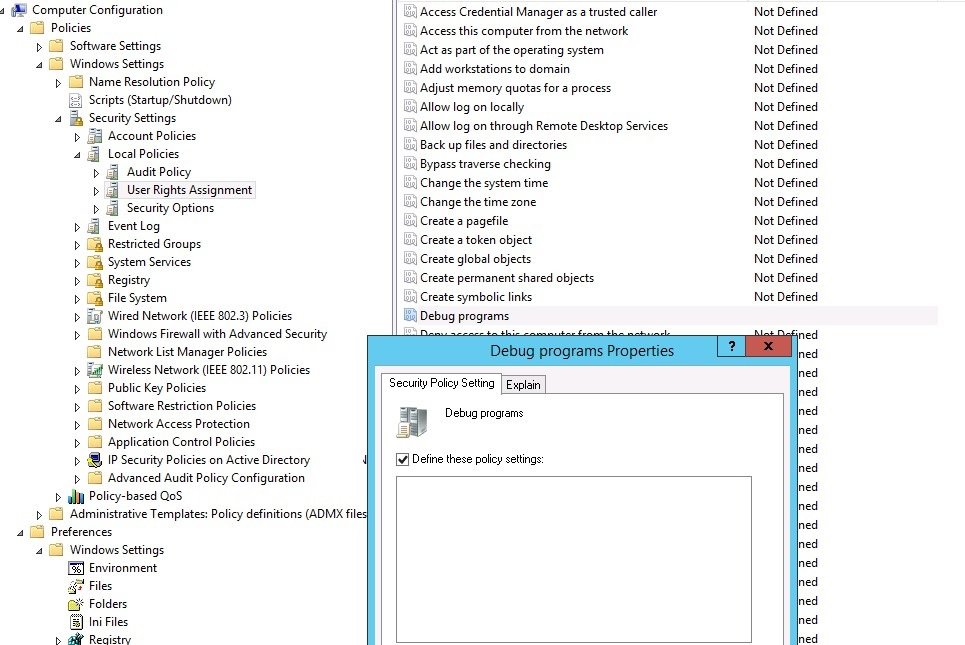
This configuration must be included in the domain group of users who require debug rights, leaving this space empty so that no other user can access this privilege.
After applying these changes, if the system detects a debugging attempt through mimikatz, the attacker will receive an error in response:
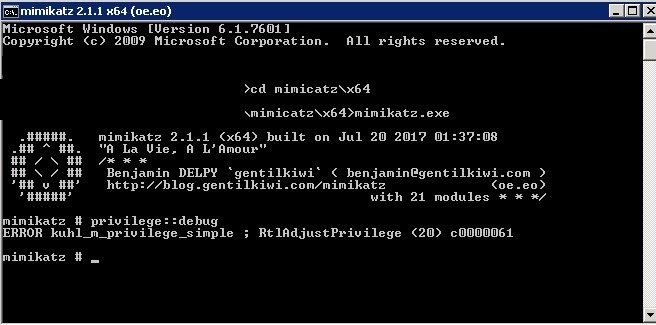
This should not be considered a full protection, as this restriction can be easily evaded by an experienced hacker.
Method 2: Disable WDigest
This protocol was introduced in Windows XP and allows HTTP Digest authentication, a feature that requires the use of the user’s password in clear text. Windows 8.1 and Server 2012 R2 add the ability to completely prevent LSASS from storing passwords in clear text.
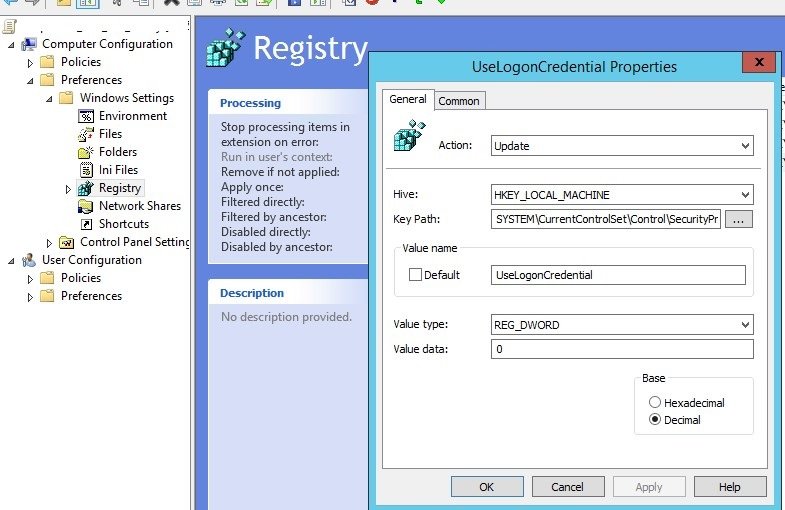
To prevent WDigest from being stored in memory, a DWORD32 parameter called UseLogonCredential and a value of 0 in the registry key HKEY_LOCAL_MACHINE \System\CurrentControlSet\Control\SecurityProviders\WDigest were added, mention network security specialists.
If you need to completely disable the WDigest authentication method, set the value of the Negotiate key to 0 in the same branch, experts recommend. Implementing these measures in Windows 7, 8 and Windows Server 2008 R2/2012 requires the installation of a specific update (KB2871997).
Method 3: LSA protection against connecting third-party modules
For users of Windows 8.1 and Windows Server 2012 R2 systems, there is the possibility of including LSA protection, a security measure for LSA memory that prevents connection to unprotected processes.
To enable this protection, network security experts recommend that you create a RunAsPPL parameter with a value of 1 in the registry key HKEY_LOCAL_MACHINE \SYSTEM\CurrentControlSet\Control\LSA.
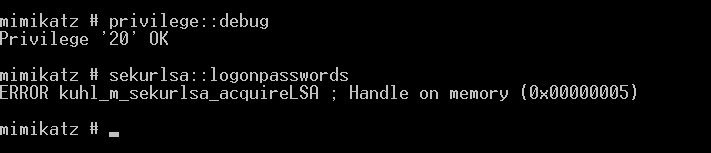
After applying this parameter, the attacker will not be able to access the LSA memory, so Mimikatz will only get the erorsecurlsa::logonpassword command in response.
Method 4: Disable LM and NTLM
The legacy LM authentication protocol and the associated LM stored hash must be disabled using the Network Security Group Policy. Network security experts do not recommend saving the LAN Manager hashing value in the next password change.
You must also stop using at least the NTLMv1 protocol (this is changed in Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options – Network Security: Restrict NTLM) and, in some cases, NTLMv2.
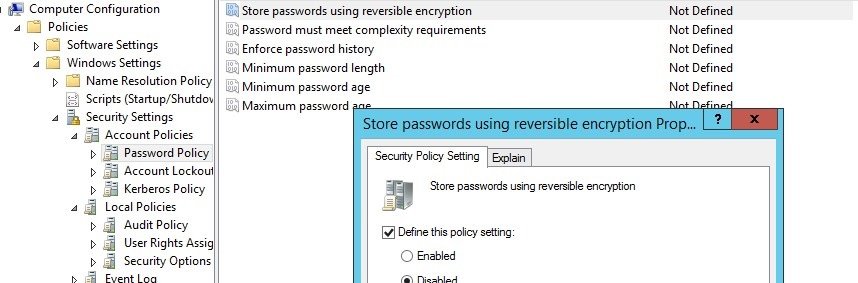
Method 5: Avoid using reversible encryption
Network security experts should strictly prohibit the storage of user passwords in plain text in Active Directory. To avoid this practice you must disable the Store Password using reversible encryption domain policy, which you must apply to all users; go to Computer Configuration -> Windows Settings -> Security Settings -> Account Policies -> Password Policy and set its value to Disabled.
Method 6: Using the Protected Users group
Windows Server 2012 R2 allows the use of a special protected group to increase the security of highly privileged users. These accounts are better protected against hackers, as members of this group can authenticate through Kerberos and other services.
This group can include users with administrator accounts for a specific domain or server. This feature works on servers and runs on Windows Server 2012 R2, network security experts mention.
Method 7: Avoid using stored passwords
Another recommended measure is to prevent domain users from saving their passwords to network shares in CreedManager. To do this, enable the Network Access Policy and go to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options to prevent password storage.
If this measure is applied, remember that users will also be prohibited from using passwords saved in the programmer’s jobs.
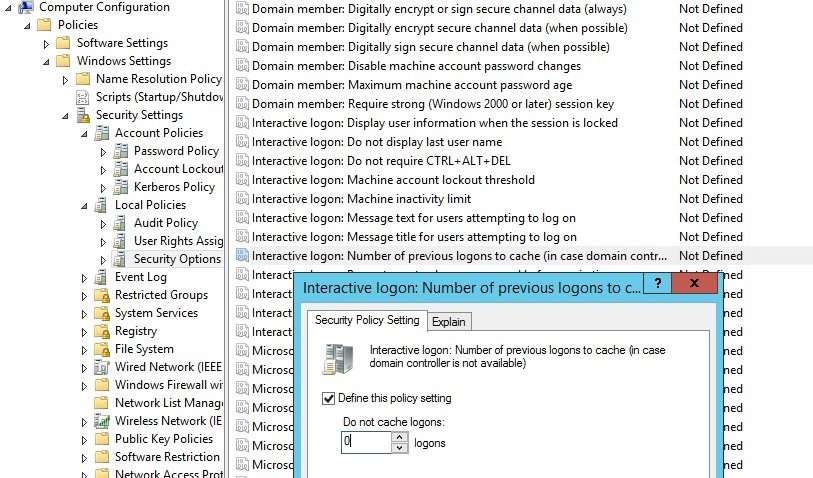
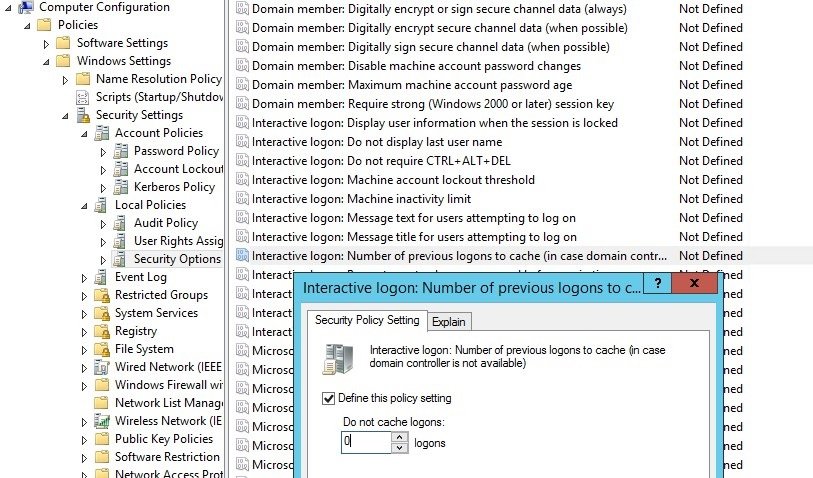
Method 8: Disable credential caching
One of the functions of Mimikatz is to obtain a hash of the passwords of the system users of the registration branch HKEY_LOCAL_MACHINE \ SECURITY \ Cache, which stores by default the hash of the password of the last 10 records in the system. These hashes are used to authorize users on the system if the domain controller is unavailable.
Network security experts recommend disabling this feature with the activation of the Interactive Login Policy in Computer Configuration -> Windows Settings -> Local Policy -> Security Options, where we must change the value of this parameter to 0.
While these are not all methods to protect a system against the use of tools like Mimikatz, they are some of the most functional network security practices, helping thousands of administrators stop countless attacks on a daily basis.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











