System logs analysis is one of the most useful hacking tasks for researchers and specialists in digital forensics and reverse engineering, so a tool that facilitates this process can be fundamental in an investigation.
This time, digital forensics experts from the International Institute of Cyber Security (IICS) will show you RegRipper, a tool for automatic registry analysis on the Windows system, which will provide you with this important information in a simple and convenient format for further investigation tasks. This tool is available on GitHub.
Digital forensics experts describe RegRipper as a set of open-source Perl scripts that operates thanks to the registry hive; a command is selected and as set a version of the system outputs is obtained in text format.
Install RegRipper
To get started, download the file from GitHub, unzip the file, and proceed to the menu items shown below. You will need to choose between two execution options: console (rip.exe) and windowed (rr.exe). The first option provides more flexible functions, while the second is the easier to use option.
We need the operating system log files. They can be removed from a non-system disk by simply copying them.
- Run the application with rr.exe
- Open the registry hive (let’s say SOFTWARE in this example)
- Indicate the output text file (SOFT. TXT)
- Click the Rip! button
One by one, all the commands relevant to the hive “SOFTWARE” will start to run (you can find out whether a plugin is suitable or not from its content, digital forensics experts mention).
The output file will contain information for each of the commands. The file obtained will be full of information of interest to researchers, but there are ways to obtain more specific information.
Working with RegRipper console version
This is where the interesting part begins, as we will be able to flexibly configure which plugins might work.
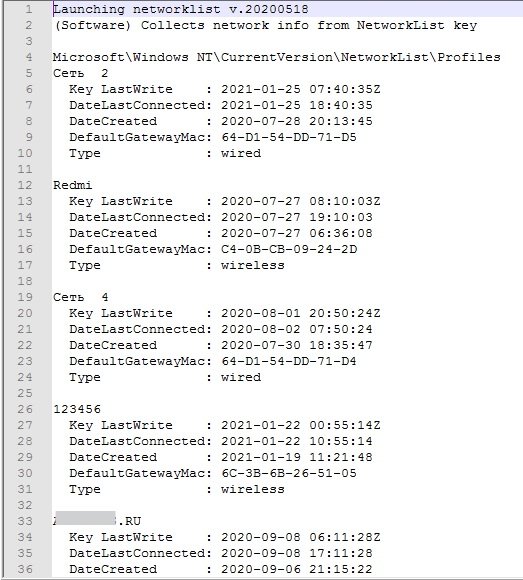
rip -r ..\reg\SOFTWARE -p networklist > networks.txt
The networklist command will run and display a list of networks and their installation data:
You can also find the target operating system version with the winver command:
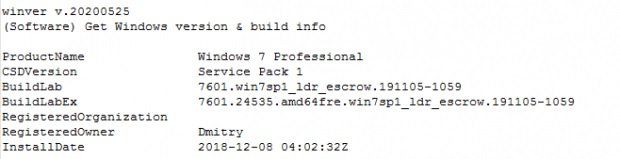
You will be able to find the time of the user’s last login by entering lastloggedon:
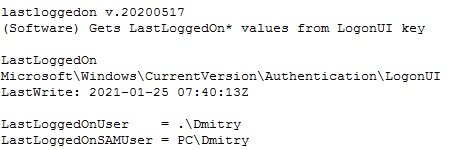
To conclude, you can also automatically run all available commandss automatically. The required command appears when you open the help options (-h).
As you can see, this is a magnificent tool that will allow you to get a lot of information from the analyzed system. Remember that this material was prepared for informational purposes and should not be taken as a call to action; IICS is not responsible for the misuse that may occur to the information contained herein.
To learn more about information security risks, malware variants, digital forensics, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











