Cybersecurity specialists report the detection of a new malware family that is hidden in legitimate binaries for the infection of Linux systems. Identified as FontOnLake, this set of malicious tools features rootkit and backdoor features and is capable of generating persistence on affected systems.
According to ESET researchers, this malware family has various modules that interact with each other for the operation of malicious tasks, including the theft of sensitive data, persistence generation and C&C communication. Apparently, the first samples of FontOnLake were uploaded to VirusTotal since May 2020.
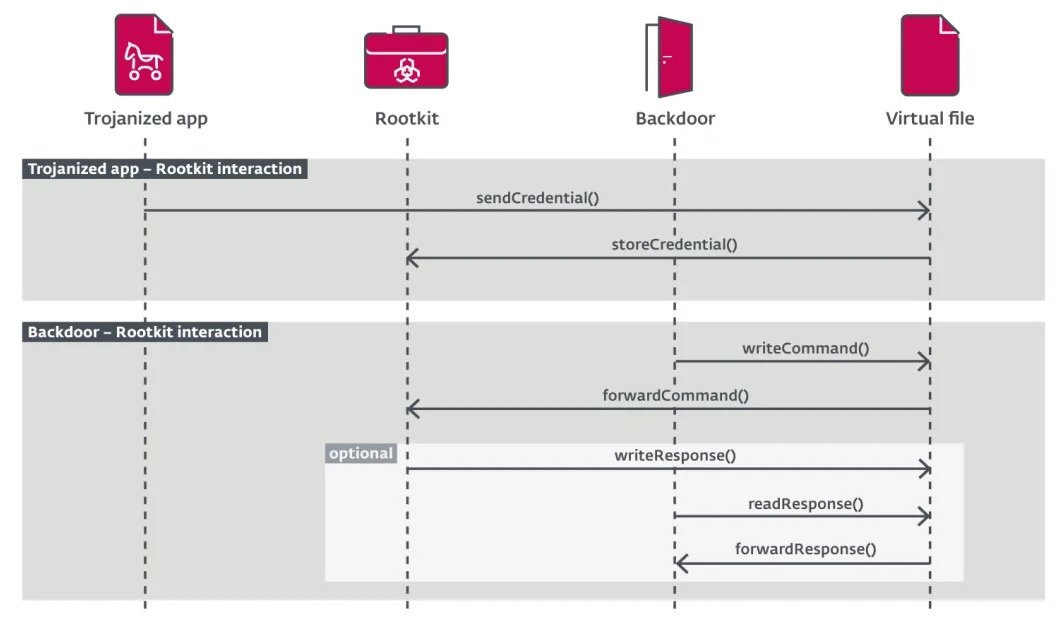
The researchers mention that FontOnLake is distributed through a “trojanized application”, although the method used by hackers to trick users into downloading malicious binaries is still unknown. In these attacks, threat actors modify various Linux system utilities, including:
- cat: to print the contents of a file
- kill: to list all running processes
- sftp: Secure FTP
- sshd: OpenSSH server process
According to Vladislav Hrčka, malware analyst at ESET, all malicious files are conventional Utilities of the Linux system and allow hackers to gain persistence by commonly running on any system.
The researchers believe that the malicious utilities could have been modified at the level of the source code. In addition to transporting the malware, these binaries are responsible for delivering additional payloads, collecting information, and other malicious tasks.
Experts found three backdoor variants written in C++ linked to this campaign, allowing attackers to gain remote access to the affected system. Typically, these backdoors focus on collecting SSHD credentials and bash command history for sending to the attackers’ C&C server, as well as employing custom commands to keep the connection active.
For ESET, FontOnLake is based on a malware variant previously identified by Tencent Security Response Team researchers and associated with an Advanced Persistent Threat (APT) group. Avast also conducted a report on a similar malware variant, identified as HCRootkit.
Avast described this malware family as a malicious development that is delivered using a binary written in C++, responsible for delivering a payload for a subsequent attack and evading security mechanisms on the affected systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











