The experts of Google Threat Analysis Group, specialized in the investigation of state hacking campaigns, electronic fraud and disinformation, report the detection of a new evasion technique used by threat actors in order to evade detection in financial fraud campaigns.
According to experts, this hacking group managed to create malicious code signatures that Windows identifies as valid but cannot be decoded or verified by OpenSSL, which would allow attackers to evade detection rules.
A threat actor could hide its identity in signatures without affecting its integrity, managing to evade detection for extended periods, extending as much as possible the existence of the useful life of its malicious certificates and providing the opportunity to expand the threat to more systems.
This technique seems to depend on OpenSUpdater, a variant of unwanted software that violates Google’s policies and can be harmful to users because it can be used to install potentially malicious software. The actors behind OpenSUpdater try to infect as many users as possible, mainly targeting users in the U.S. who turn to websites for downloading cracked video games and other samples of pirated software.
Typically, OpenSUpdater samples are signed with the same code signing certificate from a legitimate certificate authority. As for this campaign, the detected OpenSUpdater samples carry an invalid signature as a method of evading detection.
The signature in these samples was edited so that an End of Content (EOC) marker replaces a NULL tag for the ‘parameters’ element of the SignatureAlgorithm that signs the X.509 leaf certificate. EOC markers end encodings of indefinite length, but in this case an EOC is used within a defined length encoding (l = 13).
Security products that use OpenSSL to extract signature information reject encryption as invalid. For an analyzer that allows these encodings, the digital signature of the binary will appear legitimate and valid; apparently this is the first time that researchers have detected a hacking group using this technique to evade detection and at the same time preserve a valid digital signature in PE files.
In the following image, it can be seen that the Windows operating system identifies this signature as valid, thus completing the attack. This security issue has already been reported to Microsoft.
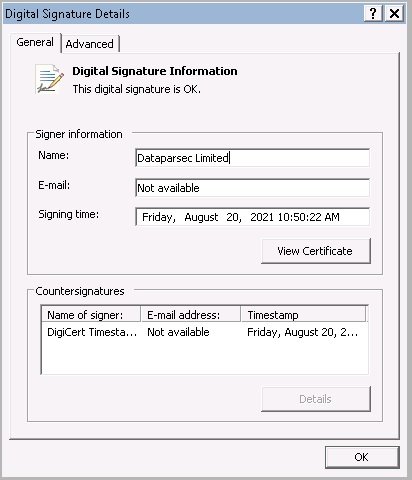
After the detection of this activity, the authors of OpenSUpdater have tested other variations of invalid encodings in order to evade possible security measures and be able to evade detection.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











