After a brief period of recent activity, this weekend it was detected that the REvil ransomware group could have shut down its operations again after an unidentified actor took control of its platforms on the Tor network. REvil’s Tor sites have been out of service for hours, plus ransomware operators confirmed the situation on a hacking forum.
Cybersecurity specialist Dmitry Smilyanets also reported the incident, mentioning that an unknown user hijacked the Tor services associated with REvil, so he believes that the person responsible could have copies of all the information of this ransomware operation under his control.
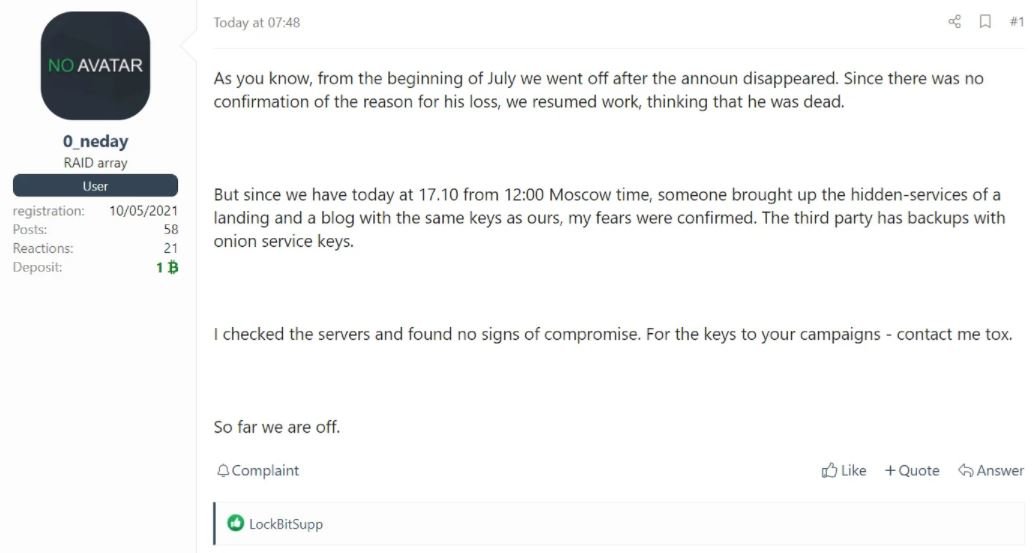
Soon after, a threat actor known as 0_neday confirmed that the individual responsible for the attack was able to access backups of REvil’s onion service. This individual also mentioned that no attack features have been found on their servers, although the best thing for the time being would be to close the hacking operation; in addition, the hacker asked REvil affiliates to contact operators to continue deploying their attacks.
REvil platforms function as a hidden Tor service, the launch of which requires generating both a public and a private key; the private key must be protected and restricted for trusted administrators, as anyone with access could start the onion service on their own server.
Because the attacker was able to hijack REvil’s domains, they could also have access to the hidden service’s private keys; the alleged operator of the ransomware also believes that the Tor server was compromised.
As some users will recall, REvil hackers shut down their operations after a massive attack on Kaseya, which began to attract the attention of authorities in the U.S., so the hackers decided it would be best to get away from the problems for a while. REvil remained inactive for a couple of months until a few weeks ago its hidden platforms began to reactivate.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











