A critical vulnerability in the trial version of WinRAR 5.70 would allow threat actors to intercept and modify responses from the RarLab server that should be received directly by application users. A successful attack would allow hackers to force code execution on the victim’s system.
Tracked as CVE-2021-35052, this vulnerability was discovered by chance when a team of researchers was using WinRAR 5.70; after using it for a few days, the app suddenly threw up a JavaScript error shown below:
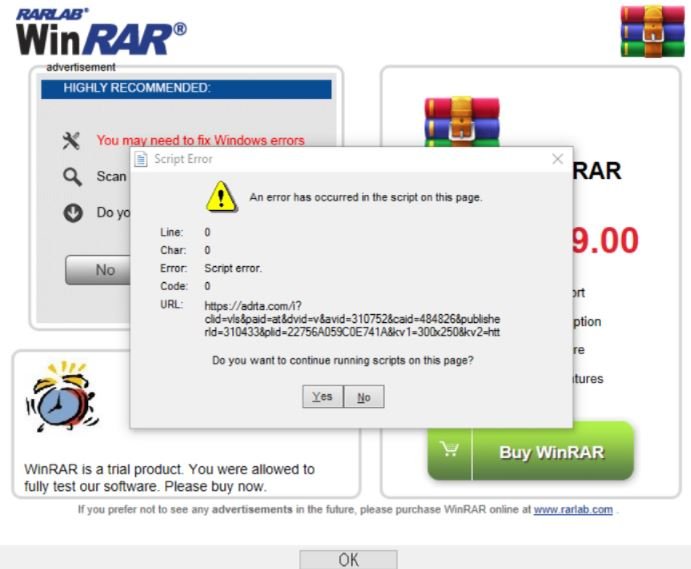
This dialog box began to appear when starting WinRAR after the end of the trial period, which puzzled the experts. After a deep look at the tool, it was discovered that the system where WinRAR was running used an mshtml.dll engine, which is the cause of the error.
To understand what the problem is and how it can be exploited, the researchers turned their Burp Suite test tool into the default Windows proxy for intercepting browser traffic. Since the transmission of requests occurs over HTTPS, the WinRAR user began to see a message about the impossibility to use that Burp certificate.
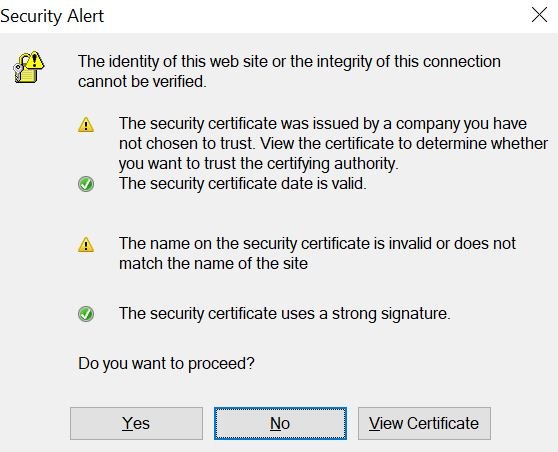
After seeing this alert, the researchers clicked on the “Yes” option to get the desired content. An attempt to modify the messages returned by the server was also successful.
Instead of substituting their domain instead of the default notifier.rarlab.com each time, the researchers replaced the response code with a redirect: error 301 Moved Permanently. In this case, a page redirect with a redirect is cached and all user requests are automatically redirected to an attacker-controlled site.
Experts described this condition as a kind of Man-in-The-Middle (MiTM) attack based on ARP spoofing; an address resolution spoofing that is possible when using the network ARP protocol.
The fact is that this old protocol does not provide authentication of requests and responses, and the interception of a transmission ARP request can be used to create a fake object of a distributed computer system, so an attacker only needs to be on the same network as the victim, to which Internet Explorer will respond by automatically assigning the malicious resource to security zone 1.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











