The Internet of Things (IoT) is probably one of the most widely used technological concepts in recent times, as it has implementations in all kinds of environments, from complex industrial processes to domestic use. According to pentesting specialists, IoT architecture can be divided into 3 layers: hardware, communication or network and interfaces or services. In other words, the three elements that make up an IoT system are hardware, protocols, and communication services.
According to the specialists of the International Institute of Cyber Security (IICS), one of the most recent security threats is related to IoT devices, as malicious hacking groups have realized that these computers do not have the best security measures, which makes them easy and perfectly usable targets for the launch of other subsequent attacks, including botnet use, malware distribution, and denial of service (DoS) attacks.
The ease with which these attacks are launched has forced the cybersecurity community and pentesting specialists to find the best ways to prevent the compromise of these devices, something especially complicated considering the variety of IoT infrastructures, operating systems and firmware versions. However, there are options to strengthen the security of these networks in a practical way.
IoT-PT is a virtual machine for pentesting specially designed for IoT devices, composed of exploitation frameworks for IoT and Bluetooth hacking tools, reverse engineering firmware (automated and dynamic), iOS application analysis / APK and network security tools. This tool is available at GitHub.
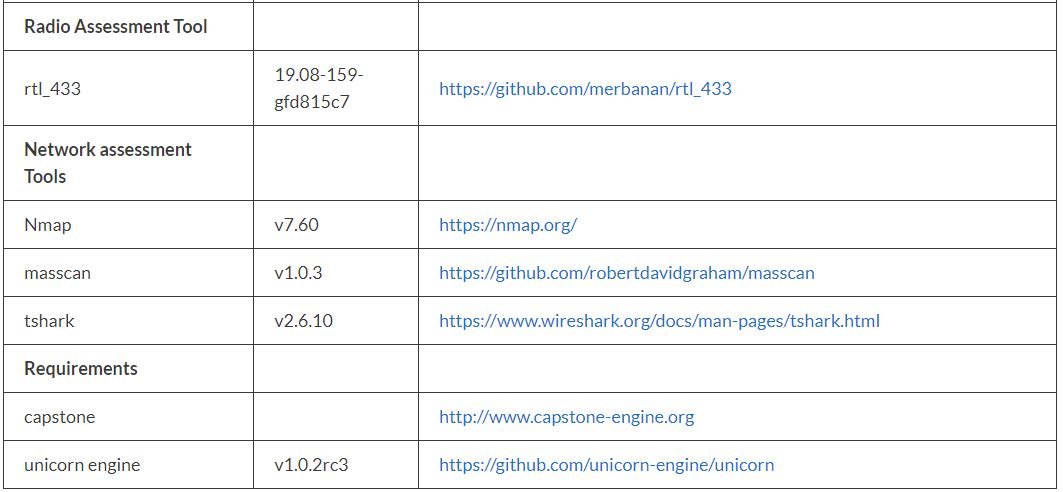
According to pentesting experts, the following list shows all the tools included in IoT-PT:
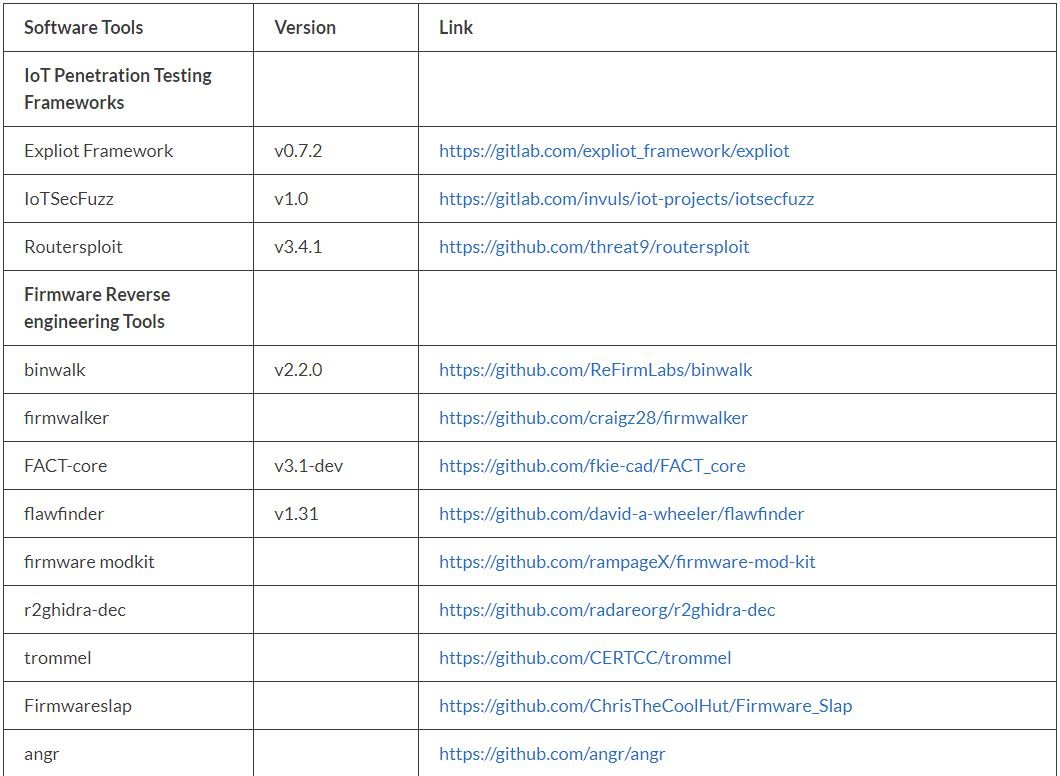
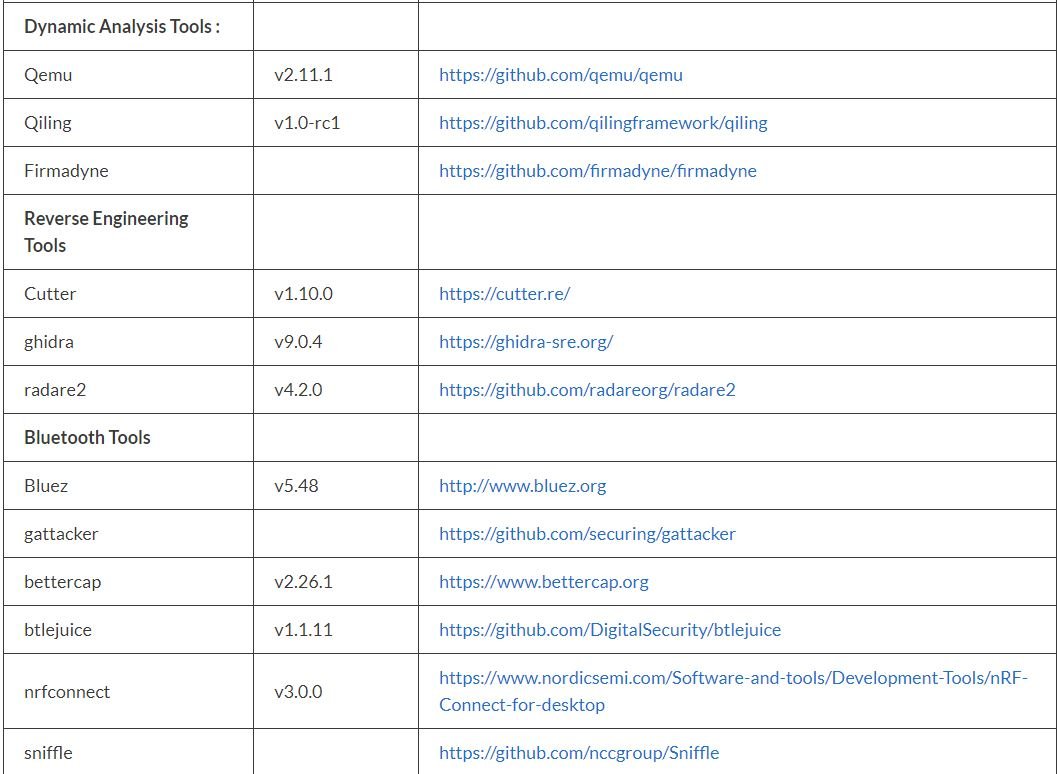
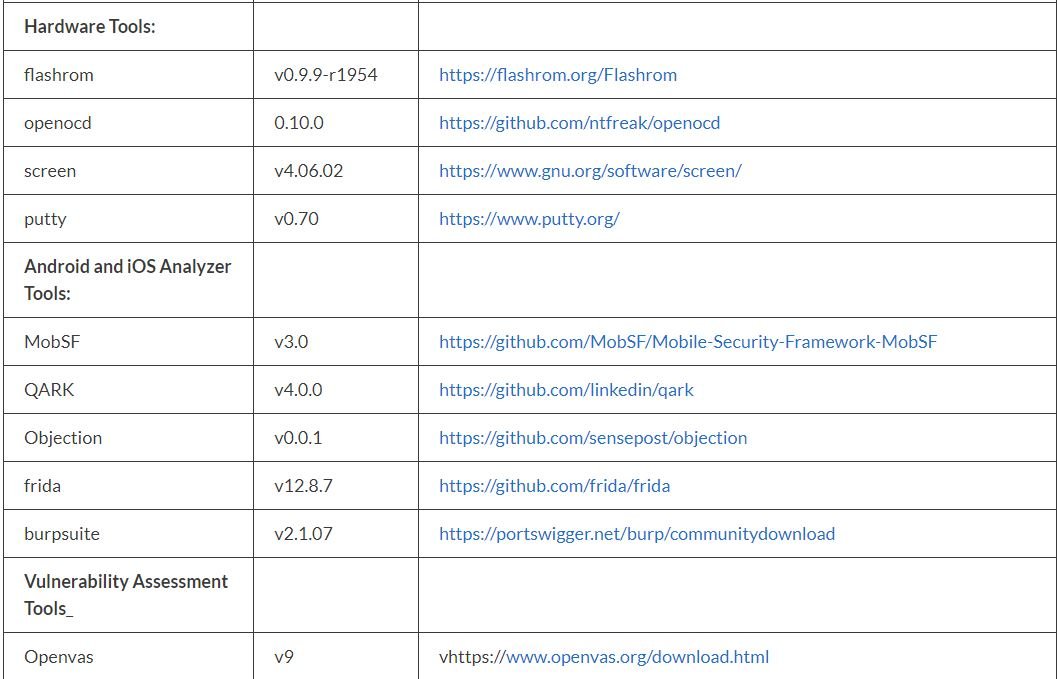
Before concluding, we remind you that this article was prepared for informational purposes and should not be taken as a call to action. IICS is not responsible for the misuse that may occur to the information contained herein. Remember that pentesting must be deployed for legitimate purposes and with the prior consent of the administrators of the analyzed system.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











