Cybersecurity specialists report the detection of a set of malicious packages in Node.js package manager repository (npm) designed to collect Discord tokens and eventually take control of the affected accounts. As some users may recall, the npm repository is an open source platform for JavaScript developers to share and reuse blocks of code. Malicious packages can pose a threat to the supply chain as they can be used as building blocks in various web applications.
Security researchers at JFrog Security reported the detection of a set of 17 malicious packages, with different payloads and tactics. These tools were all designed to target Discord, the virtual meeting platform used by nearly 350 million users.
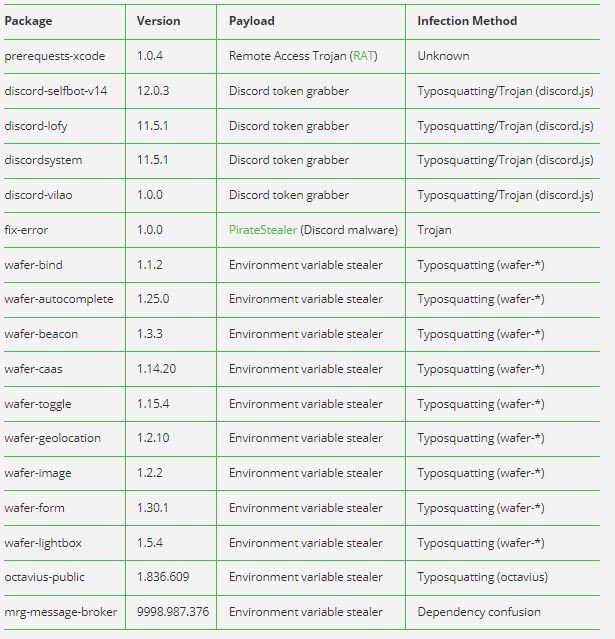
According to the report, the packages’ payloads are varied, ranging from information stealing tools up to full remote access backdoors: “The packages also have multiple tactics to deploy malicious actions”, researchers say. Besides, experts say Discord is the ideal target for these hackers for multiple reasons, including:
- The platform is also part of the attack. Discord servers are often used as anonymous C&C servers, remote access Trojan (RAT) controllers and even as botnet commanding tools
- A hacked Discord account can serve in social engineering campaigns and malware deployment automatically
- Hackers can compromise Discord Nitro accounts to resell them cheaply on an online marketplace. Discord Nitro costs $100 a year, so a stolen account is sold at just a fraction of the price
To lure users into downloading the packages, the malicious projects employ several tricks; for example, two of the 17 packages (discord-lofy and discord-selfbot-v14) hide themselves as modifications of the legitimate library discord.js, which enables interaction with the Discord API.
Malware developers also took the original discord.js library as the base and injected obfuscated malicious code into the file src/client/actions/UserGet.js in a classic Trojan tactic.
Npm code managers have removed any potentially malicious packages; however, some of them could still be active in some projects, so users of Discord developing tools should remain aware about this security risk.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











