As seen in multiple security incidents, supply chain networks are a target of great interest and easily accessible to threat actors, as well as being a highly vulnerable point for affected networks. The Palo Alto Networks research team recently reported the finding of a new supply chain attack capable of abusing a cloud video platform for the operation of a skimming campaign.
As some users may already know, a skimming attack involves injecting malicious JavaScript code into a website so that threat actors can take control of the HTML form and collect sensitive information from users. In this case, the malicious code is hidden in a video, which when imported will extend the skimming task to other platforms.
So far, at least 100 websites in the real estate industry affected by this campaign have been detected, indicating the great capacity of expansion of hackers. All compromised websites belong to a parent company and the source of the attack is the import of the video loaded with malicious scripts.
Compromised platforms
Virtually all affected websites feature a form that users can fill out to request additional reports on a property for sale. As we can see below, the forms request personal information from the interested parties.
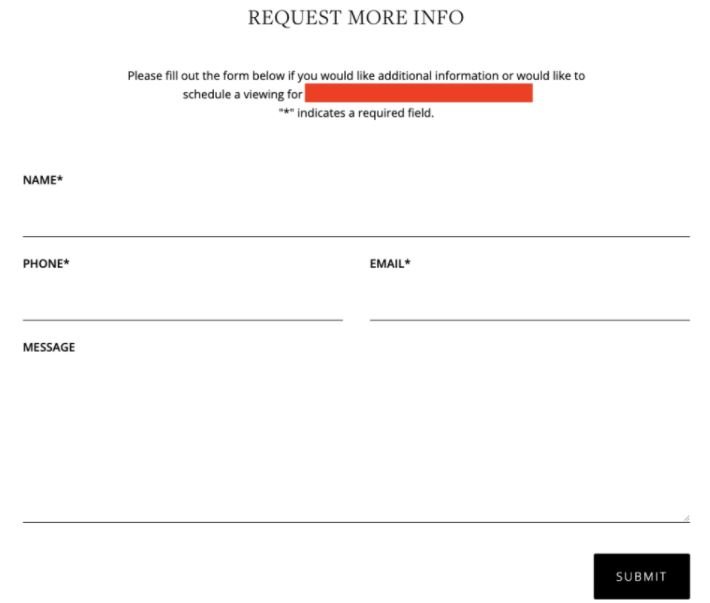
When trying to access the page, the researchers managed to detect the skimmer load on an iframe URL:

Later the researchers managed to identify the skimming code, which is carefully obfuscated. The researchers had to divide the code into four different parts to better understand how it works, which allowed all its functions to be fully identified.
Malicious video
As mentioned above, the most prominent feature of this attack is the use of the video loaded with malicious code. Apparently, this tactic is possible because when users of cloud platforms create a player, it is possible to add their own JavaScript customizations by uploading a file to be included in their player. In this case, the user uploaded a script to hide malicious code.
The researchers theorize that the threat actors managed to alter the static script in its hosted location by attaching the skimming code; in the next player update, the video platform re-integrates the compromised file and delivers it along with the affected player. Further analysis reveals that the malicious code attempts to collect sensitive information from victims (names, email addresses and phone numbers) and then sends this data to a collection server, identified as malicious on the VirusTotal platform.
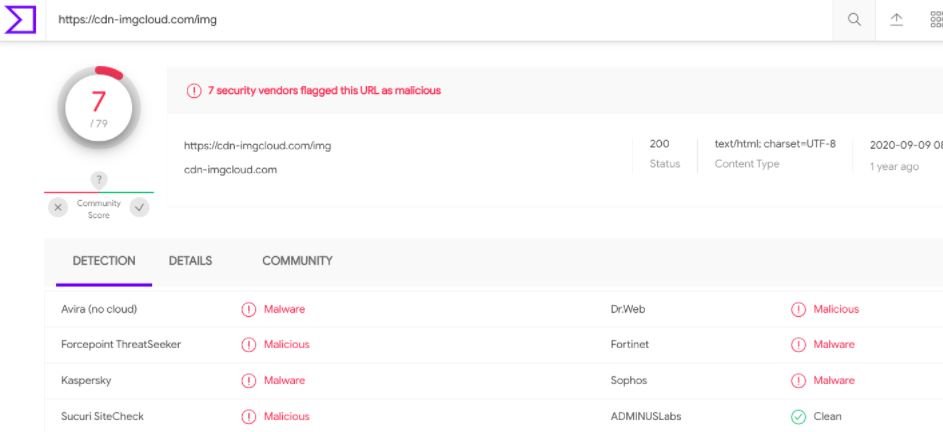
Researchers also believe that this campaign is effective thanks to the combination of carefully obfuscated malicious code and the use of the cloud video platform, which could also extend excessively due to its intrinsic qualities.
Palo Alto assures that organizations must adopt new prevention strategies, as threat actors continue to create new ways of attacking, exploiting vectors never before seen or even thought of before, because the simple blocking of domain names or malicious URLs is not able to prevent these security breaches.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











