Over the past few days a Ukrainian researcher has waged a campaign against the operators of the Conti ransomware, inadvertently spying on their work and leaking all sorts of sensitive details, including private conversations and even snippets of source code.
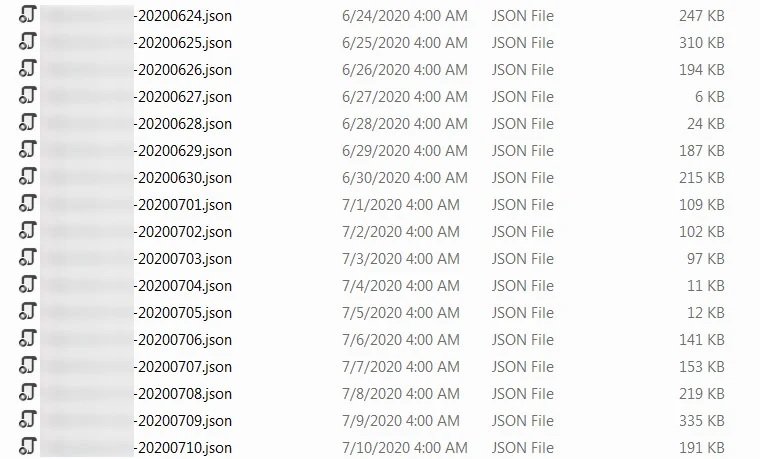
Through a Twitter account identified as @ContiLeaks exposed the leak of some 393 JSON files with more than 60,000 internal messages taken from the XMPP private chat server associated with groups such as Conti and Ryuk.
Thanks to these leaks, the cybersecurity community discovered all kinds of details about these cybercriminal operations, including cryptocurrency addresses under their control, methods of evasion against law enforcement, attack patterns and many more details. A couple of days later the investigator continued to leak confidential messages.
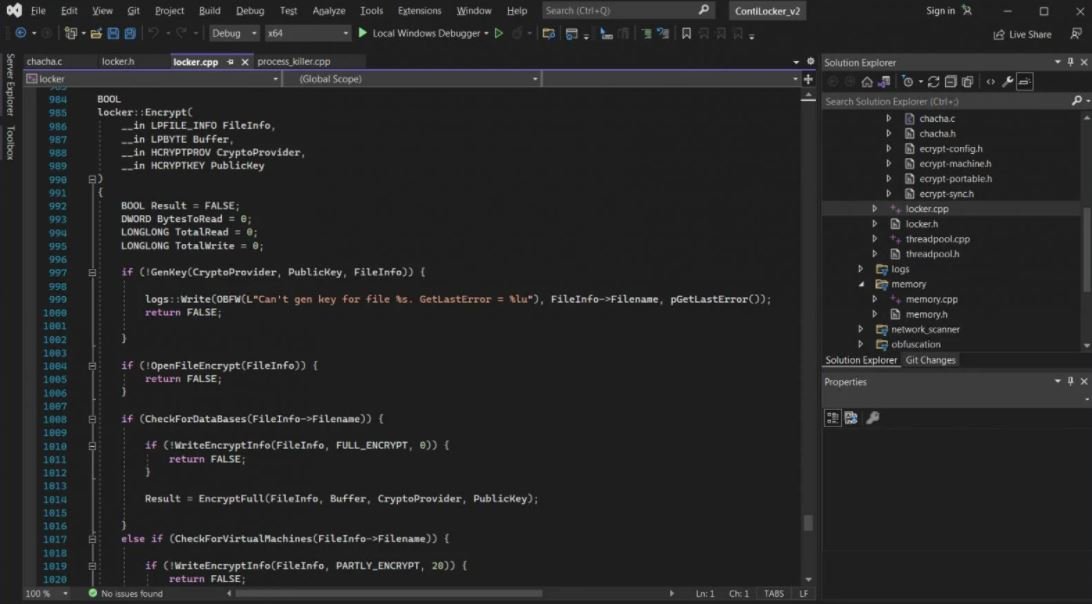
Although these messages are revealing, what has attracted the most attention is the leak of a password-protected file that appeared to store the source code of the Conti ransomware. The Ukrainian researcher did not share this password, other researchers took very little time to decrypt this data and therefore access the source code of the ransomware.
Although this could prove beneficial to malware analysts, specialists believe that other malicious operations could take this source code to develop their own versions of ransomware.
At the moment the impact that this incident could have on Conti’s operations is unknown, although investigators believe that the sophistication of these hacking groups could allow them to continue operating smoothly despite the leaks.
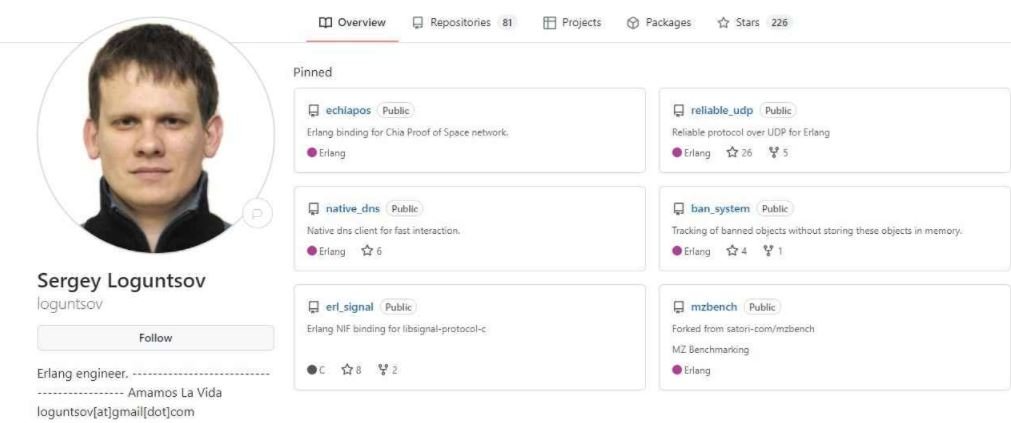
In addition to these leaks, the researcher claims to have deceived one of the members of the ransomware operation, which allowed him to discover his real identity. According to the leaker, this individual is named Sergei Loguntsov and uses the alias “Begemot”.
Finally, the researcher decided to publish the backend of the TrickBot command dispatcher, the backend of the TrickBot data collector, the list of Conti storage servers and many more data about this cybercriminal operation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











