A South Korean cybersecurity firm has reported detecting a fraudulent campaign targeting players of Valorant, a popular video game for Windows systems. In this campaign, threat actors post videos on YouTube offering tips and supposed tools for cheating in the game, seeking to implant a dangerous malware variant on affected systems.
The tools to aim automatically are highly sought after by players of the shooter genre, as they allow users to increase the effectiveness of their shots in the video game and level up more quickly. In most cases, these bots work as plugins installed in the game, so their use is relatively easy.
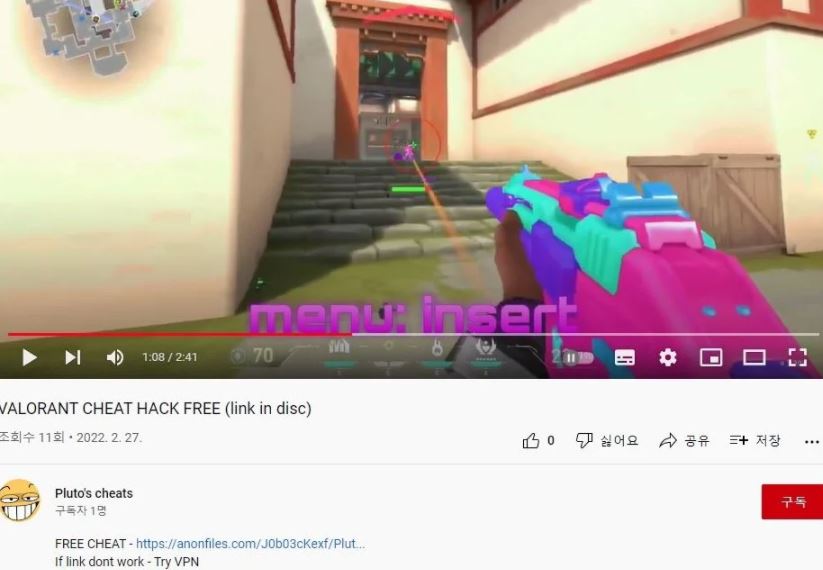
According to the report, the videos used by the hackers include links in the description, which redirect users to a website for downloading a RAR file with an executable identified as “cheatinstaller.exe.” Actually, this file hides a sample of RedLine, a dangerous malware for stealing passwords and other sensitive details.
Once installed on the target system, the malware will begin searching for information of interest to hackers, including:
- Overview: Device name, username, IP addresses, Windows version, system information and list of active processes
- Websites: Passwords, payment card numbers, autocomplete data, bookmarks and cookies from Chrome and Firefox-based browsers
- Cryptocurrency credentials: Armory, AtomicWallet, BitcoinCore, Bytecoin, DashCore, Electrum, Ethereum, LitecoinCore, Monero, Exodus, Zcash and Jaxx
- Other data: Use of VPN, profiles and tokens from Steam, Discord and other platforms
At the completion of the information collection process, RedLine packages these records into a ZIP file identified as “().zip”, extracting the files via a WebHook API POST request to a Discord server.
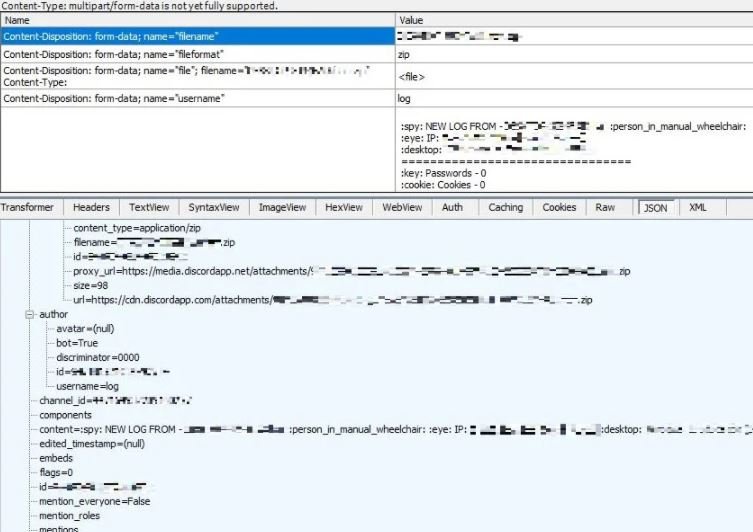
These are real and constant security threats, as bots, whether authentic or just a tactic to hide malware, are always developed by unreliable entities and lack digital forms, which is highly useful for groups of threat actors.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











