Researchers from firmware security firm Binarly confirmed the detection of some critical flaws in the Unified Extensible Firmware Interface (UEFI) of multiple business laptops produced by Dell. A couple of weeks ago, the technology company announced the release of patches for five vulnerabilities in System Management Mode (SMM) present in a total of 45 devices, including several models of Alienware, Inspiron and Vostro laptops.
The vulnerabilities were tracked as CVE-2022-24415, CVE-2022-24416, CVE-2022-24419, CVE-2022-24420 and CVE-2022-24421 and received scores of 8.2/10 according to the Common Vulnerability Scoring System (CVSS). In the report, they are described as validation errors that would allow authenticated local threat actors to execute remote code on affected systems.
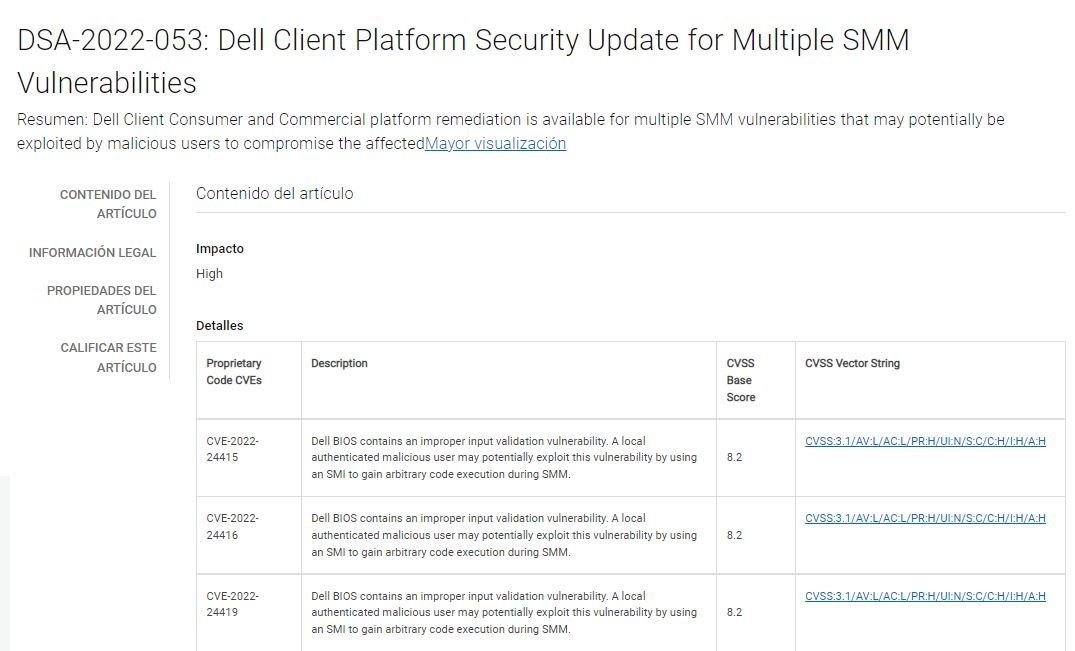
Updates have been available for all affected Dell devices since February, so the company recommends users of laptops, embedded PCs and exposed gateways address the flaws as soon as possible. Three of the reported flaws (CVE-2022-24419, CVE-2022-24420 and CVE-2022-24421) were identified by Binarly, which describes them as variants of the UsbRt error, identified in 2016.
Also known as Aptiocalypsis, these bugs could have been exploited for arbitrary code execution in SMMs to disable flash write protections and inject backdoors into affected firmware versions.
These flaws resided in devices running AMI-based firmware and multiple variants were identified in the months following the initial report. The bugs Dell recently addressed demonstrate that similar bugs continue to have a real impact on current devices, no matter that it’s been more than 5 years since Aptiocalypsis came along.
Binarly’s report adds that these flaws have been a constant target of exploitation over nearly six years, severely impacting the firmware supply chain and the operation of automatic vulnerability detection tools: “Most security practices revolve around compliance checklists with misconfigured static scanning tools and running an antivirus scan. This fundamental misunderstanding of design flaws leads to an expansion of code complexity and keeps devices in a perpetual state of exposure.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











