Cybersecurity specialists report the discovery of a variant of cyberattack against Combined Charging Systems (CCS), one of the most used technological implementations in current electric cars. According to the report, the attack is capable of interrupting communications between the car and the charger, causing an interruption in the charging process.
Malicious activity can be deployed at a distance of up to 47 meters using electromagnetic interference, which would allow interrupting the charging process in more than one car at a time; In addition, researchers report that unsophisticated hardware and minimal knowledge are required to complete an attack. During the attack, hackers will try to abuse the HomePlug Green PHY, DIN 70121 and ISO 15118 standards, present in a large number of electric cars.
The attack, dubbed Brokenwire, could affect most of the more than 12 million electric vehicles currently used worldwide, not to mention that other electric means of transport such as ships, planes and heavy vehicles would also be affected.
Attack process
CCS technology is actually a collection of multiple technical standards. During the charging process, electric vehicles (EV) and Electric Vehicle Power Equipment (EVSE) exchange important messages, such as State of Charge (SoC). The high-bandwidth IP link used for communication is provided by HomePlug Green PHY (HPGP) powerline communication technology.
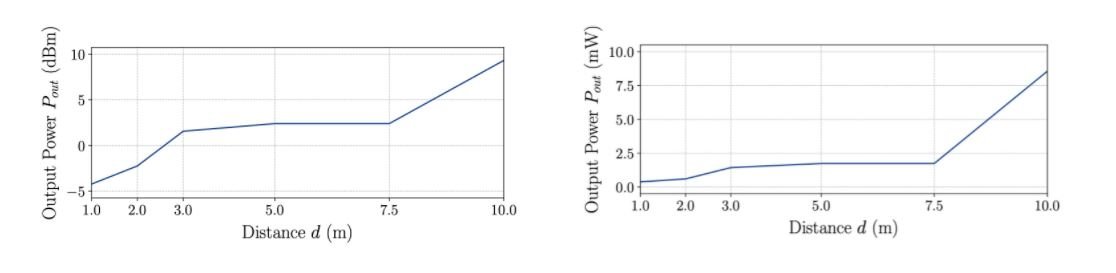
The attack was tested in a controlled environment for different distances between the charging cable and the attacker. The tests were conducted on the same HPGP modems found in most electric vehicles and charging stations.
The diagram below illustrates the test results, which indicate that minimal software and hardware requirements are needed to execute the attack from a distance of up to 10 meters.
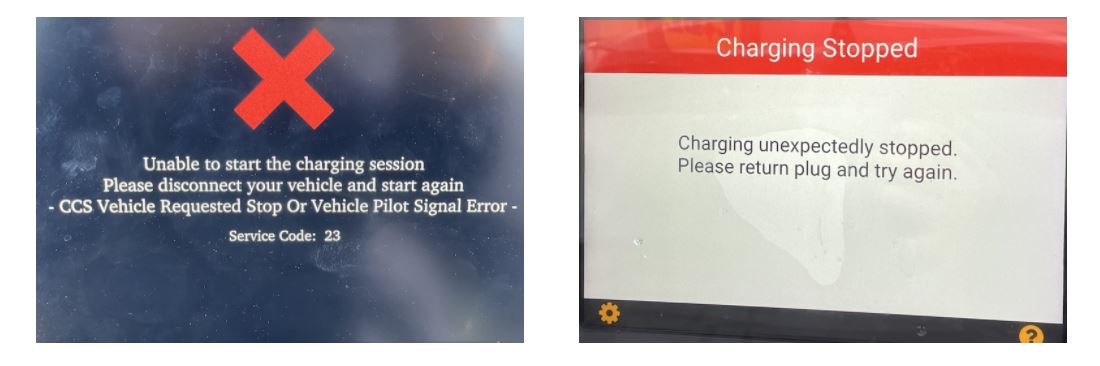
The following video shows an attack against a CCS HPC charger. The vehicle seems to carry out its charging process without any problems, but stops as soon as the malicious signal is emitted.
As mentioned above, the attack is fully functional in various samples of charging stations.
Most electric cars currently produced could be exposed to such an attack. The report has been presented to the various manufacturers to find the best way to address these failures.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











