SonarSource cybersecurity specialists report the detection of various vulnerabilities in PEAR, a development environment and distribution system for PHP code components. According to the report, these vulnerabilities could have been easily exploited for the deployment of supply chain attacks, which could lead to severe disruptions in systems around the world.
Since the SolarWinds supply chain attack incident these hacking variants have become common. A report by the European Union Cyber Security Agency (ENISA) studied 24 attacks reported between January and July 2021, noting that up to 50% of these attacks came from known threat actors, a trend that could increase in the following months.
These attacks could prove even more significant in an implementation like PEAR, as this resource is likely to run on a computer before being deployed to production servers, which could give hackers access to a compromised network.
It is estimated that around 285 million packages of pear.php.net have been downloaded, the most popular being the PEAR client itself, Console_Getopt, Archive_Tar and Mail. Although alternatives like Composer cover a larger sector of the market, these PEAR packages are still widely used.
SonarSource found at least two bugs, claiming that both have been exploitable for more than 15 years. If a threat actor manages to exploit the first vulnerability and publish malicious releases, the second flaw would allow access to the central PEAR server.
While this is a considerable security risk, the good news is that maintainers have already begun to address the issue. A first patch was released on August 4, introducing a secure method to generate pseudorandom bytes in the password reset feature.
As shown in the following screenshot, a string composed of 16 random bytes is mapped to $random_bytes, while md5($rand_bytes) is named afterwards. This second variable does not exist ($random_bytes vs $rand_bytes) and this operation will always result in the MD5 hash of an empty string (d41d8cd98f00b204e9800998ecf8427e).
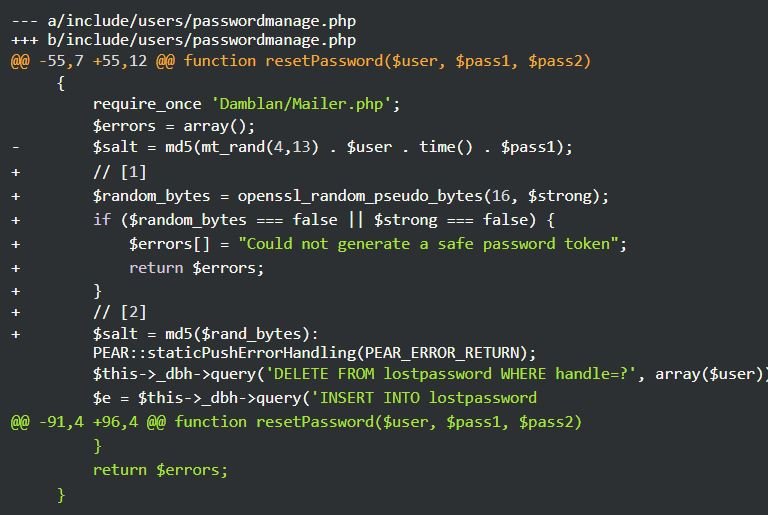
These issues were reported to PEAR maintainers in July 2021 and their full correction could be ready next May.
The researchers recommend users of affected deployments stay on top of the release of updates, as well as consider other options such as Composer, which has a more active and constantly maintained community of collaborators, focused on preventing flaws and attacks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











