Researchers from SEC Consult Vulnerability Lab reported the detection of a sandbox breakout vulnerability present in some Konica Minolta bizhub multifunctional models. Detected in late 2019, successful exploitation of this flaw would have given attackers full read/write access to the device’s operating system, in addition to root access to stored data.
Threat actors could have manipulated compromised devices in multiple ways, without legitimate users even being able to identify the malicious activity. The flaws were addressed in early 2020 and since then the company has actively monitored the problem, although this is not enough to prevent all risks.
The disadvantage of the firmware patches issued by Konica Minolta is that they had to be applied manually by the company’s technical service teams, which already represents a problem considering that there are hundreds of thousands of users of these multifunctional devices. As if that were not enough, the pandemic severely delayed the application of the patches, leaving an undetermined number of users totally exposed to the attack.
EXPLOITATION PROCESS
To better understand the active exploitation risk, SEC Consult Vulnerability Lab developed a proof of concept (PoC), trying to successfully replicate an attack on the Konica Minolta bizhub C3300i and C3350i devices, or more precisely on its terminal.

At the conclusion of the tests, the experts demonstrated that it was possible to deploy three different attacks, which were assigned a CVE vulnerability key:
- CVE-2022-29586: Sandbox bypass in the tactical display terminal
- CVE-2022-29587: Running UI/Chromium terminal as root
- CVE-2022-29588: Passwords stored in plain text in the file system
Below is a brief explanation of each error.
SANDBOX BYPASS IN THE TACTICAL DISPLAY TERMINAL
These machines have a touch screen for ease of use. According to the report, the touch screen terminal has a user interface based on a proprietary application; when opening some applications through this terminal, it is possible to notice a slight change in the appearance of the user interface.
This behavior is the result of a context change, so the applications that run are not based solely on the proprietary application. After connecting a keyboard to one of the printer’s multiple USB ports and pressing specific key combinations, it was possible to determine that some parts of the application run an ordinary Chromium browser in “kiosk mode”, which can be easily escaped from the secure environment.
The researchers mention that the exploitation of this fault involves a few steps:
Step 1 – Public User Access
Physical access is required to exploit this vulnerability, in addition to using “User Authentication” and enabling “Public User Access” on the device. The “Public User Access” button must be pressed on the touch screen terminal of the physical printer.
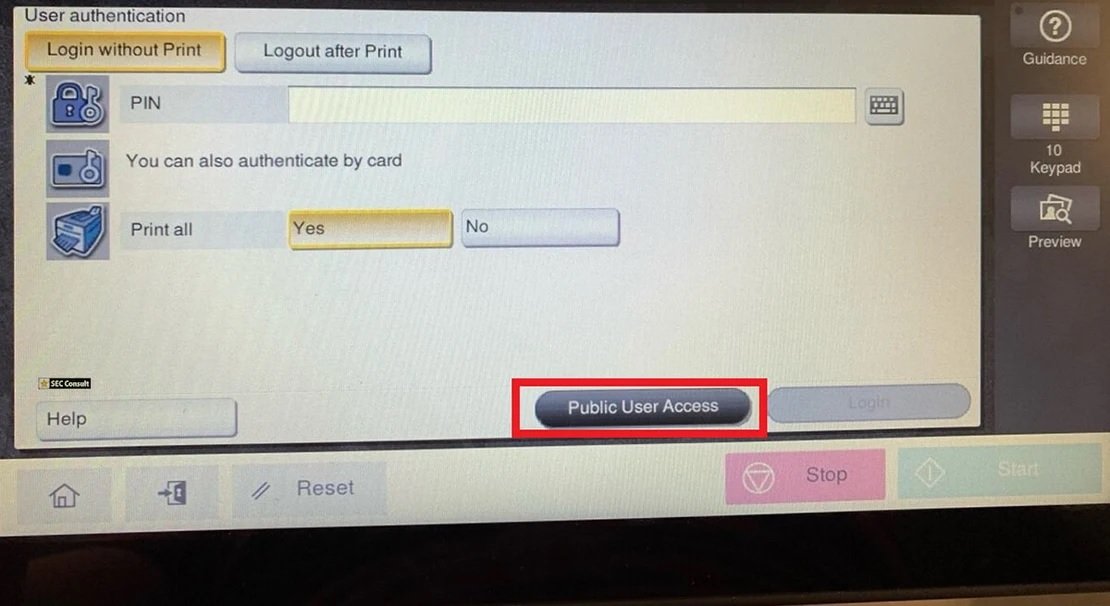
Step 2 – Utility
After enabling “Public User Access”, a menu opens where you can select functions such as “Scan”, “Copy” and “Utility”, which is the button that should be pressed below.
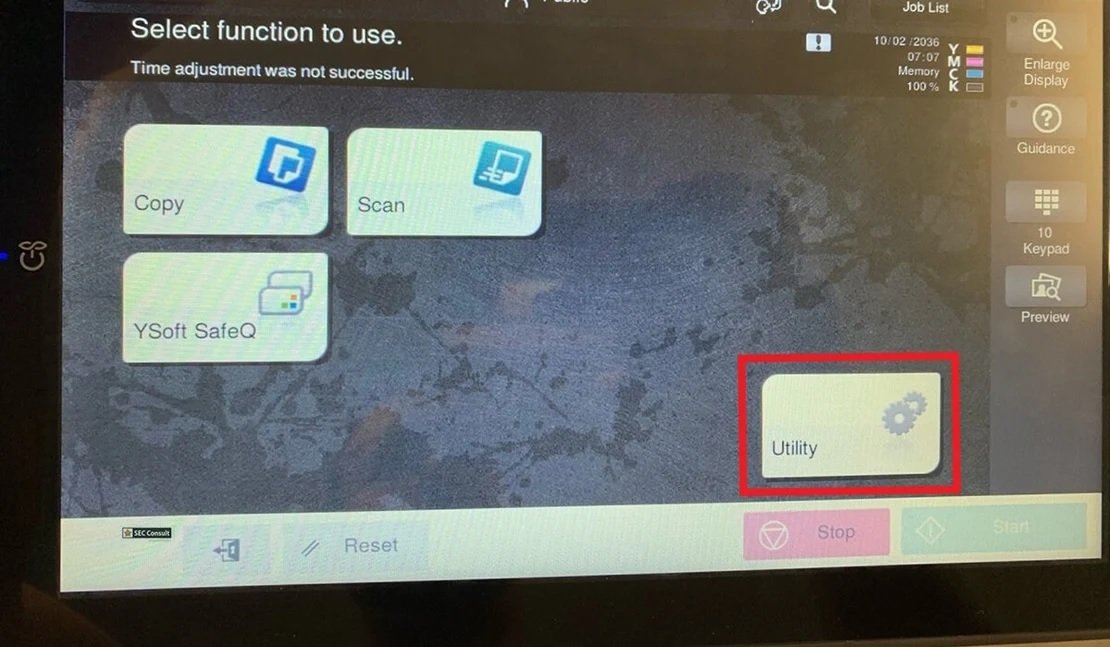
Step 3 – Utility X2
The “Utility” button should be pressed again as shown below:
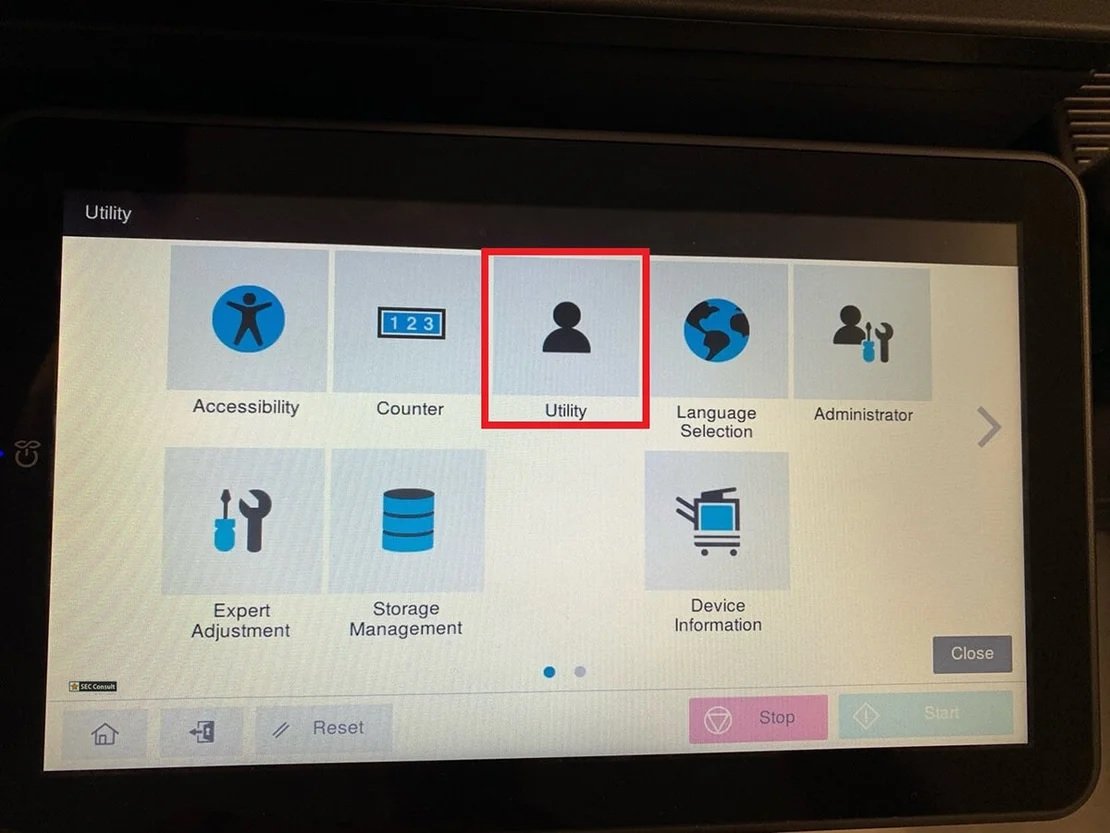
Step 4 – Access to Chromium
At this stage a slight change in the user interface is observed. This is because the proprietary application launches in a Chromium browser in kiosk mode:
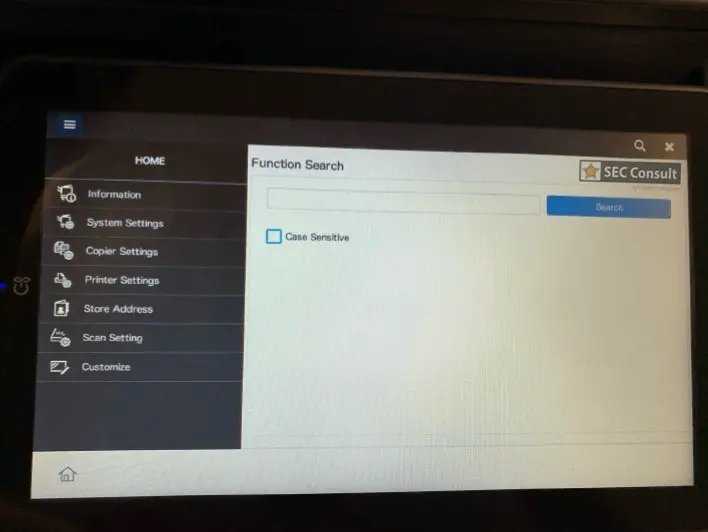
Step 5 – Connect a keyboard
For the next step, a USD keyboard is connected, since the touch screen keyboard does not have some keys necessary for the attack.
Step 6 – Access to Chromium Developer Console
Most available shortcuts are locked on a normal Linux operating system or block the printer. However, it is possible to gain full access to the system by pressing F12 from the USB keyboard, allowing you to open the Chromium Developer Console as shown below:
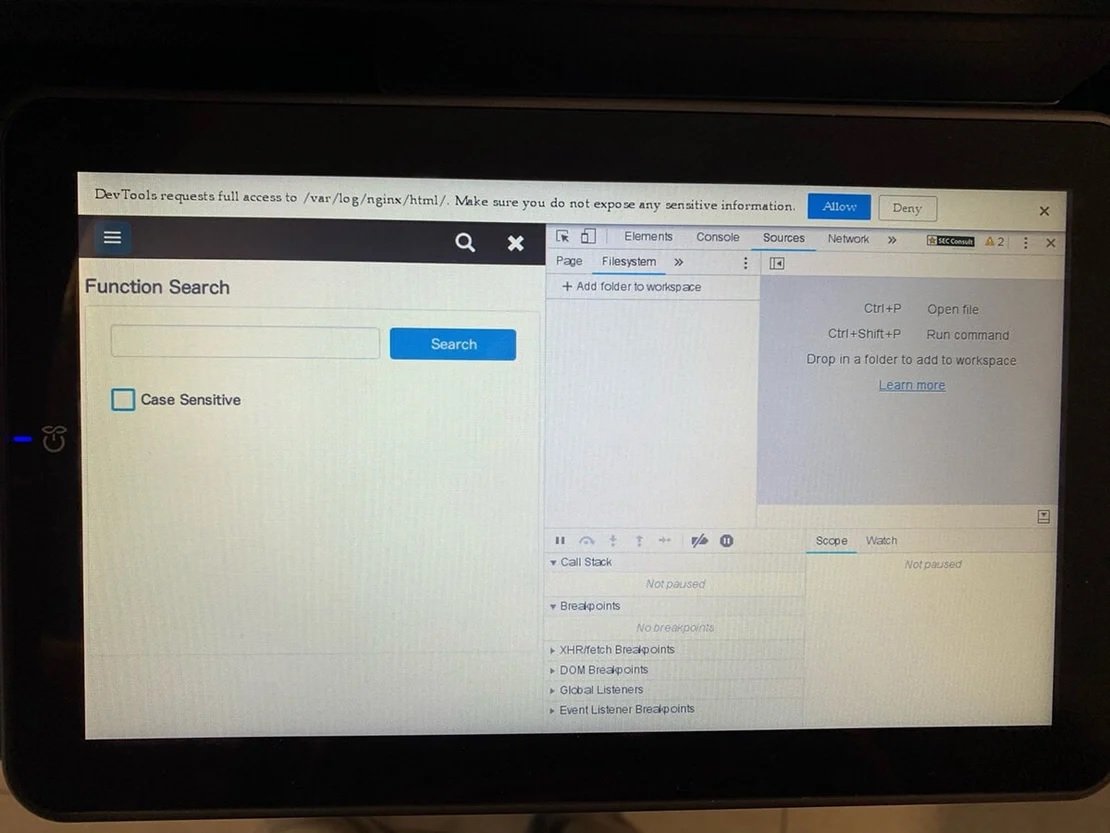
This allows hackers to access the file system, from where a folder can be added using the “Add folder to workspace” option. In the window that appears, approval is requested to add the folder, where it is enough to click on the “Allow” button.
If these steps are completed properly, attackers will be able to access arbitrary files in the file system with root access and write arbitrary files, manipulate web application scripts, and other hacking tasks.
PASSWORDS STORED IN PLAIN TEXT IN THE FILE SYSTEM
Threat actors who have successfully exploited the first of these flaws can access the “/var/log/nginx/html” directory. This folder contains a file called ADMINPASS that, as we can guess, contains the administrator password in plain text for the printer terminal and the web interface.
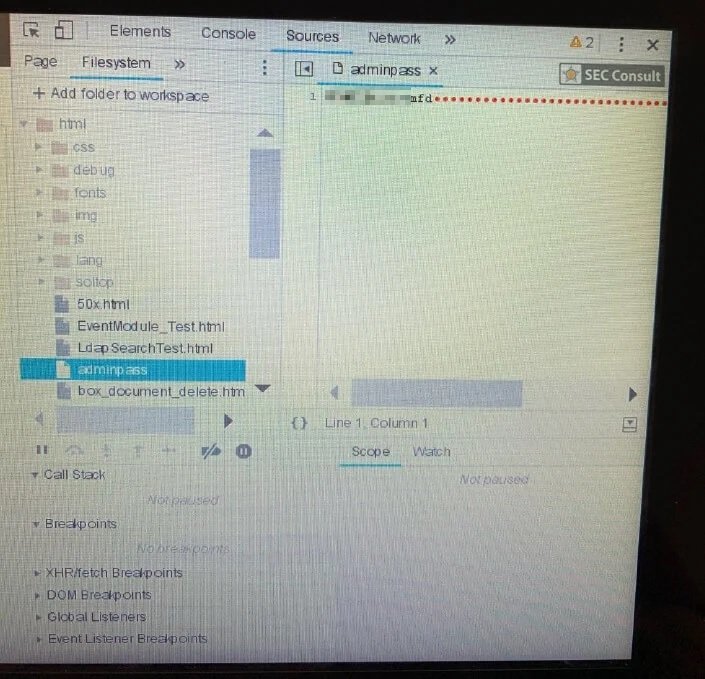
The following screenshot shows how this information is fully exposed to malicious activity.
RUNNING UI/CHROMIUM TERMINAL AS ROOT
Finally, the researchers identified that it is possible to access files such as /etc/shadow, as can be seen in the following image:
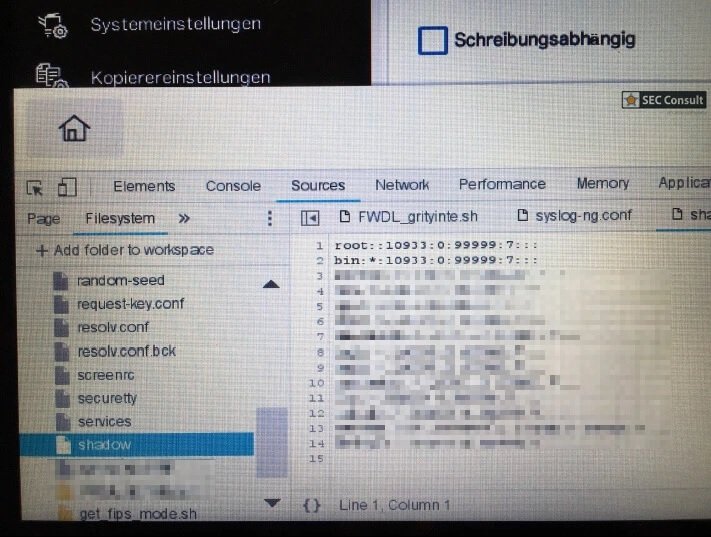
Experts thought of two possible explanations for this behavior:
- An incorrect set of permissions for files with sensitive data
- Chrome browser is running as root
Eventually Konica Minolta confirmed the second of these hypotheses.
The manufacturer determined that a total of 46 models of multifunctional Konica Minolta Bizhub MFP are affected by these flaws. As mentioned above, there are hundreds of thousands of users of these machines worldwide; In addition, these devices are renamed and sold by other companies that will also be affected by security issues.
Konica Minolta is still trying to correct these flaws, although it is difficult to estimate the number of missing users of the patches or if these bugs have been actively exploited.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











