Information security specialists reported a notable increase in activity related to the Hello XD ransomware, which has been updated to add much stronger encryption than in its previous versions. This malware variant was first identified in late 2021, apparently developed from the leaked code of the Babuk ransomware and linked to multiple double extortion campaigns.
Experts at Palo Alto Networks report that the creator of this malware variant developed a new encryptor focused on bypassing detection and changes in the encryption algorithm, which has put Hello XD far ahead of Babuk and other similar malware strains, significantly increasing its effectiveness.
As mentioned by Palo Alto experts, Hello XD was developed by a presumably Russian threat actor identified as X4KME, known for publishing various online tutorials for the implementation of Cobalt Strike for malicious purposes.
Attack process
Unlike other ransomware operations, Hello XD does not use a site on the Tor network to publish victims’ leaked information, but instead carries out a negotiation process through the TOX chat service. In addition, the latest version of the malware adds a still-in-development onion website in the ransom note shown to victims, so it is unknown for what purpose it will be created.

In addition to the new encryptor, the attacker developer of Hello XD included MicroBackdoor, an open-source backdoor that allows hackers to navigate the infected system, execute arbitrary commands and remove any trace of malicious activity. The backdoor executable is encrypted with the WinCrypt API along with the encryption malware payload.
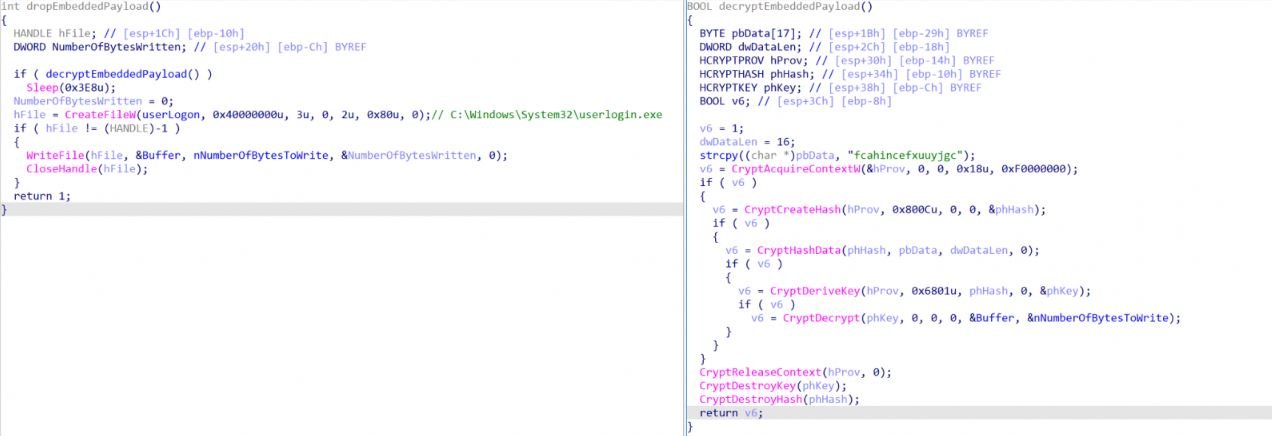
On the other hand, the payload packer has two layers of obfuscation. The malware developer derived the encryptor by modifying UPX, an open-source packager widely used by other malware developers.
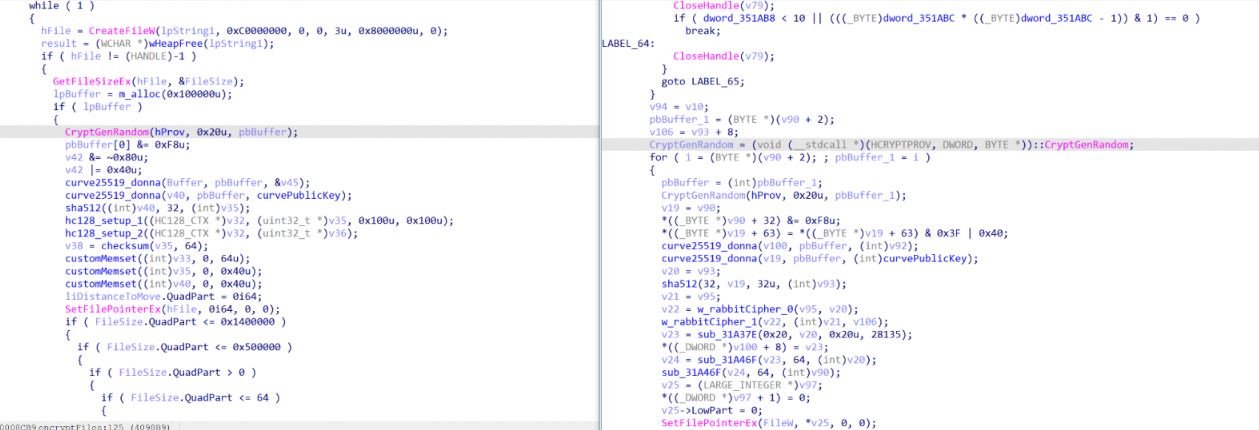
The decryption of embedded blobs requires a custom algorithm with unconventional instructions such as XLAT, while API calls in the packager are not obfuscated. Hello XD also changed its encryption algorithm from HC-128 and Curve25519-Dona to Rabbit Cipher and Curve2519-Donna.
Experts believe that the features added to the new version of Hello XD could make it one of the dominant ransomware variants over the next few months, so it’s important for the cybersecurity industry to stay on top of the development received by this malware.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











