Xen is a hypervisor that allows multiple computer operating systems to run on the same computer hardware simultaneously. The Xen Project community develops and keep Xen Project as free and open-source software, subject to the requirements of the GNU General Public License (GPL), version 2. Xen Project is at present available for the IA-32, x86-64 and ARM instruction sets The Xen Project has disclosed three vulnerabilities in its hypervisor – all of which would allow a malicious actor to take control of a host OS via VM. The Xen Project Is Focused On Advancing Virtualization In A Number Of Different Commercial And Open Source Applications, Including Server Virtualization, Infrastructure As A Services (Iaas), Desktop Virtualization, Security Applications, Embedded And Hardware Appliances, And Automotive/Aviation.
Following are three vulnerabilities discovered by Google Project Zero team
CVE-2022-26364, CVE-2022-26363
Xen maintains a type reference count for pages, in addition to a common reference count. This design is used to maintain invariants required for Xen’s safety, e.g. PV guests may not have direct writable access to pagetables; updates need auditing by Xen.
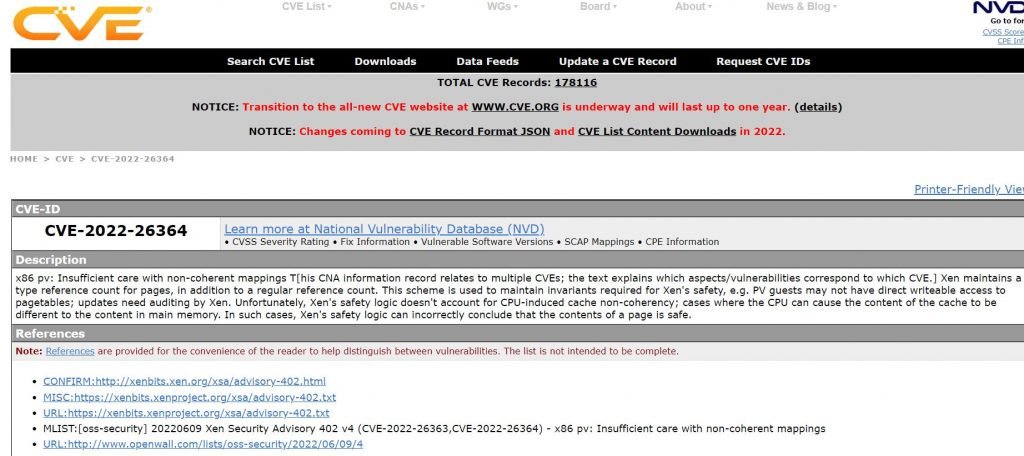
Regrettably, Xen’s safety logic doesn’t account for CPU-induced cache non-coherency; cases where the CPU can produce the content of the cache to be distinct to the content in main memory. In such cases, Xen’s safety logic can wrongly conclude that the contents of a page is safe.
IMPACT : Malicious x86 PV guest administrators can escalate privilege so as to
control the host OS system.
VULNERABLE SYSTEMS : All versions of Xen are vulnerable. Only x86 PV guests can provoke this vulnerability.
Only x86 PV guests configured with access to devices (e.g. PCI Passthrough) can provoke the vulnerability.
Only CPUs which can issue non-coherent memory accesses are affected. CPUs that list the SelfSnoop feature are not impacted, except as noted in errata. Thus, the team believes that Xen running on Intel IvyBridge or later CPUs is not affected by the vulnerability.
MITIGATION: Not passing devices through to untrusted x86 PV guests will prevent the vulnerability.
RESOLUTION : Applying the appropriate patches resolves this vulnerability.
CVE-2022-26362
Xen maintains a type reference count for pages, in addition to a regular reference count. This design is used to maintain invariants required for Xen’s safety, e.g. PV guests may not have direct writable access to pagetables; updates need auditing by Xen. Regrettably, the logic for acquiring a type reference has a race condition, whereby a safely TLB flush is issued too early and creates a window where the guest can re-establish the read/write mapping before writability is prohibited.
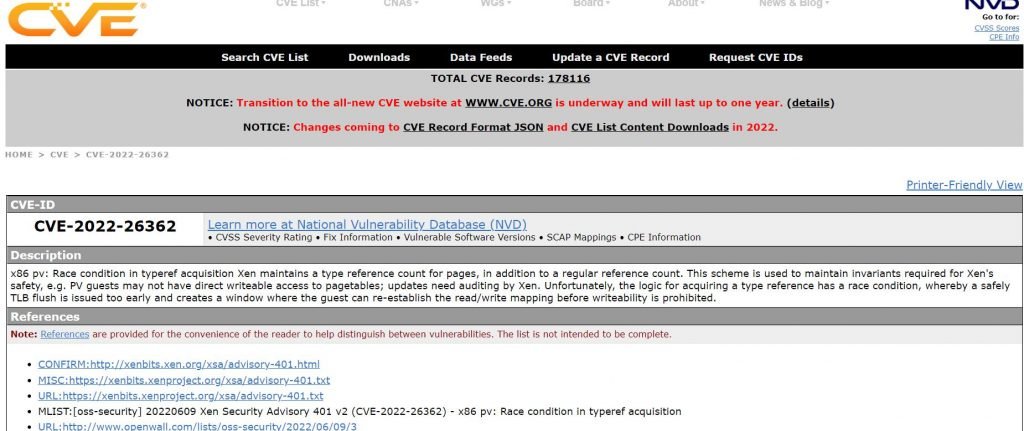
IMPACT : Malicious x86 PV guest administrators may be able to escalate privilege so as to control the host OS system.
VULNERABLE SYSTEMS: All versions of Xen are vulnerable. Only x86 PV guests can trigger this vulnerability. To exploit the vulnerability, there needs to be an undue delay at just the wrong moment in _get_page_type(). The degree to which an x86 PV the guest can nearly control this race condition is unknown.
MITIGATION: Not running x86 PV guests will avoid the vulnerability.
RESOLUTION: Applying the appropriate patches resolves this vulnerability.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











