A new malware has been discovered that actively attacks home and small business routers in Europe and North America. That malware attacks SOHO router models. Among the countries where it has already attacked is Spain, according to researchers from Lumen Technologies Inc.’s company. The malware has been named as ZuoRAT.
The malware is described as a multi-stage remote access Trojan and is believed to have been active since 2020. The malware allows hackers to access the local network and other systems on the local area network by hijacking communications.
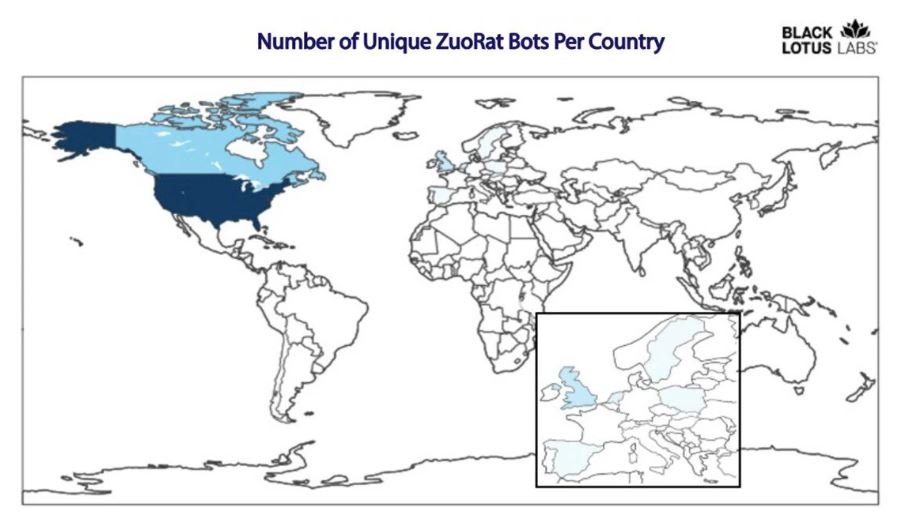
Experts believe that the reason SOHO routers are in the spotlight is because of the rise in remote work following the pandemic. It allows threat actors to take advantage of this opportunity against the traditional position of well-established organizations that have security measures in place. SOHO stands for Small Office, Home Office (SOHO) Connectivity and refers to routers used in homes that connect to a broadband service and therefore can be used by teleworkers.
In other words, according to experts, these hackers are taking advantage of the fact that, from home, teleworkers do not have such a secure environments as in companies and, therefore, this type of router could be the main objective.
Targeting home routers
Hacking routers is not new, but the researchers find it interesting that ZuoRAT is also looking to compromise routers for home offices. The use of “man-in-the-middle” attacks targeting SOHO routers is even rarer and suggests that those behind ZuoRAT demonstrate a high level of sophistication and are possibly a state-sponsored organization.
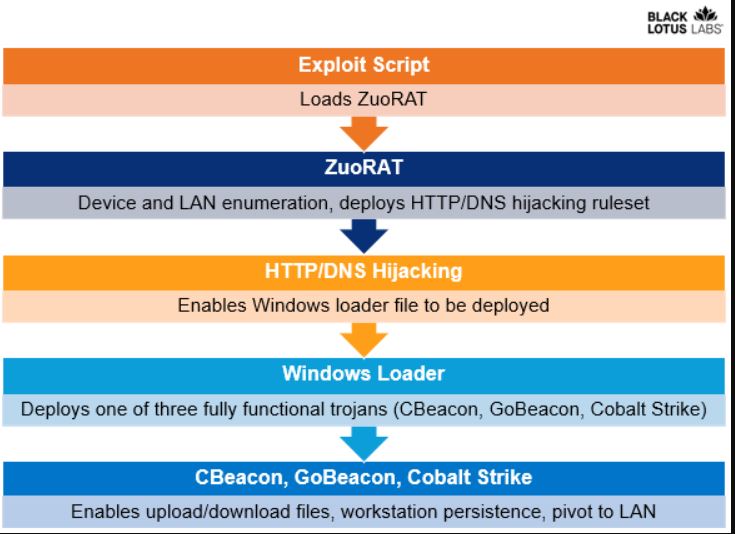
According to experts, “ZuoRAT is a compiled for SOHO routers that can enumerate a host and an internal LAN, capture transmitted packets through the infected device and perform man-in-the-middle attacks, including DNS and HTTPS hijacking. The captured data is then sent to a command-and-control server.”
SOHO firmware is not typically built with top security in mind, as they were traditionally not a huge attack vector and nobody actively manages them, so they are never patched or hardened.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











