A HackerOne employee had improperly accessed vulnerability reports submitted to the platform by security researchers’ for personal gain. The employee anonymously took these reports, somewhat modified them and disclosed these vulnerabilities outside the HackerOne platform directly to the customer with the goal of claiming bug bounty.
The inquiry began after a HackerOne customer notified the company of reportedly receiving a threatening communication, outside the platform, about a vulnerability disclosure. After the report the company launched an investigation. During which additional evidence emerged that caused them to escalate the priority of the incident. The company considered every scenario of a possible exposure to disclosure data, including potential exploitation of an application, a remote compromise by a threat actor, customer, or analyst, a leak by misconfiguration, and others. After the investigation the company concluded that this was the work of an internal threat actor.
Upon this discovery, the company began a separate investigation into the insider threat with a contained group. An insider threat is a security risk that originates from within the targeted organization. It typically involves a current or former employee or business associate who has access to sensitive information or privileged accounts within the network of an organization, and who misuses this access. Traditional security measures tend to focus on external threats and are not always capable of identifying an internal threat emanating from inside the organization. The investigating team wanted to make sure if there were multiple insider threats or employees. As multiple customers and multiple vulnerabilities details were claimed by insider threat.
The company was able to reach a conclusion using the following methods. Its internal logging monitors employee access to customer disclosures for regular business operations, namely vulnerability intake and triage. Analysis of this log data suggested a likely threat actor. Only a single employee had accessed each disclosure that customers suspected of being re-disclosed by the threat actor.
This same threat actor created a fake HackerOne account and had received bounties in a handful of disclosures. After identifying these bounties as likely improper, HackerOne reached out to the relevant payment providers, who worked cooperatively with the company to provide additional information. Following the money trail, the company received confirmation that the threat actor’s bounty was linked to an account that financially benefited a then-HackerOne employee. Analysis of the threat actor’s network traffic provided supplemental evidence connecting the threat actor’s primary and fake accounts.
The company identified seven customers who received direct communication from the threat actor. Each of the customers of the investigation was asked for information related to their interactions. Facts shared from customer investigations corroborated the conclusion from the investigation.
The company has issued platform bans for the employee’s known HackerOne accounts. The employee has been terminated for violating company policies, and employment contracts. Subject to review with counsel, the company will decide whether criminal referral of this matter is appropriate. The company is still doing forensic analysis on the logs produced and devices used by the former employee. The company is reaching out to other bug bounty platforms to share details in case their customers received similar communications from “rzlr”. The threat actor’s motives appear to be financial in nature. All off-platform disclosures known to company have been made with the handle “rzlr”.
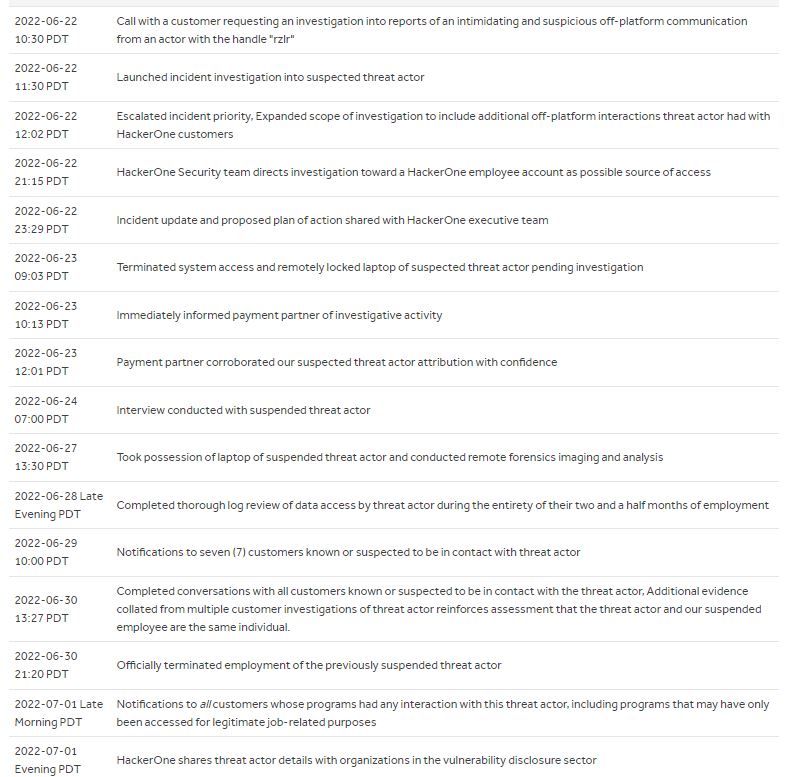
The threat actor had access to HackerOne systems between April 4th and June 23rd of 2022. If one of vulnerability reports from researchers were accessed by the threat actor, the company will contact the researchers.
.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











